Scenario 1: Corporate Laptop on Wired/Wireless Network and personal device on Wireless Network (Corporate Access)
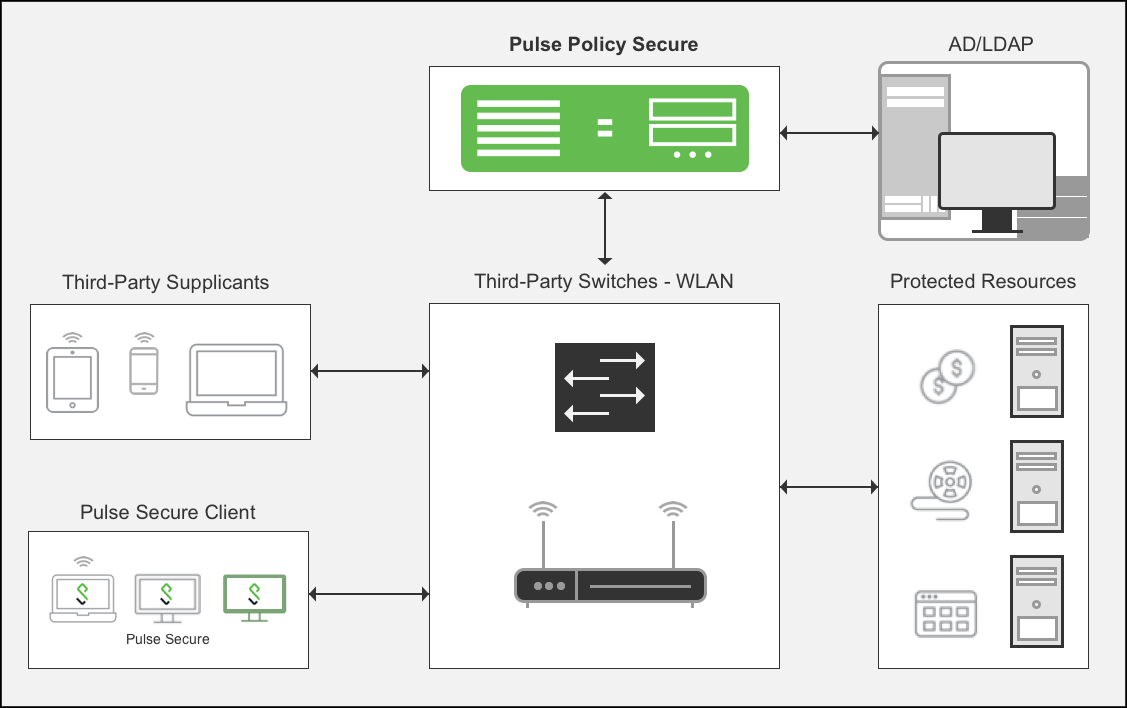
In our first scenario, an employee, Joe, wants to access the office network resources using his corporate laptop by connecting to either corporate wired or wireless network. Joe may also want to access the Internet on his personal mobile phone using office wireless network while he is away from the laptop.
When Joe’s corporate laptop is connected to the office wired/wireless network, it is connected to a Switch/WLC that is 802.1X enabled. User authentication is done by exchanging the credentials in an encrypted TLS tunnel (EAP-TTLS). Host Checker information is collected by the Pulse client and then sent to IPS inside a proprietary EAP-JUAC protocol. IPS first performs a host check to ensure that Joe’s laptop is healthy and complies with the corporate security policies. If Joe’s device is deemed healthy and compliant. If not, Joe’s device may be quarantined and could be subject to automatic or manual remediation, depending on the situation or issue. Once Joe’s device passes the host check, IPS communicates with AD server for authentication and authorization. Based on the User Role assigned to Joe in AD, the IPS sends the RADIUS attributes back to the Switch. The attributes could be a VLAN ID, a filter ID (ACL), or other attributes. The Switch port is opened, and Joe has access to network resources. After getting the access to the network, Pulse client installed on Joe’s laptop creates a L3 connection directly with IPS and periodically monitors the device health and provides this information to the IPS. If Joe’s laptop becomes non-complaint at any point, Pulse client shares this information with the IPS and server either disconnects the device by sending RADIUS disconnect or quarantines it by sending RADIUS CoA depending on the corporate policy.
In the personal mobile phone scenario, the process works a little differently. As the device is owned by Joe, the entire 802.1X authentication process is done using the mobile phone’s native 802.1X supplicant. In this scenario, the WLC acts as the authenticator and the IPS server functions as the RADIUS server. The IPS receives the authentication and authorization information from the backend AD server, and pushes the appropriate policy rules to the WLAN controller. The compliance check can be done using integration with MDM/EMM such as Pulse WorkSpace (PWS), Airwatch, MobileIron, and Microsoft Intune.
How does Pulse Client add value when compared with native/third-party 802.1X supplicant?
Host Check Prior to Authentication (Pre-admission Control
In the first scenario, the Pulse client delivered a full host check, before Joe could enter his credentials. Ivanti host checker functionality includes patch assessment/remediation, check for viruses, malware, and other threats before switch or WLAN controller ports are opened. This allows IT admin to ensure that an infected device has no connectivity to the Dynamic Host Configuration Protocol (DHCP) server or any other resource in the data center or on the network prior to the completion of host check. Ivanti provides these capabilities via a proprietary EAP-JUAC plug-in.
Layer 2 and Layer 3 Access Control via SSO
Using Pulse client, the enterprise users can deploy 802.1X based access control such as VLAN or filter assignments at Layer 2, and provide more granular Layer 3-based access control through next-generation firewalls (For example, Juniper SRX, Checkpoint, Fortinet or Palo Alto Networks Firewall). Once the IPS authenticates the user, these credentials are cached on the Pulse client. Once the Switch/WLAN controller opens the port and the device is part of the corporate domain appropriate to the user’s role, the relevant resource access policies for the user will be pushed to the firewall to access protected resources. This entire process is transparent to the end user, and can be achieved with a single sign-on (SSO) from the end user’s perspective.