JASON Web Token
This feature is applicable only to version 22.3 and later.
JSON Web Token (JWT) is an open standard that defines a compact and self-contained way for securely transmitting information between parties as a JSON object. This information can be verified and trusted because it is digitally signed. JWTs can be signed using a secret (with the HMAC algorithm) or a public/private key pair using RSA or ECDSA.
Once encoded in a URL-safe form the JWT can be transferred from a client to a server as part of a URL query string or in a HTTP header.
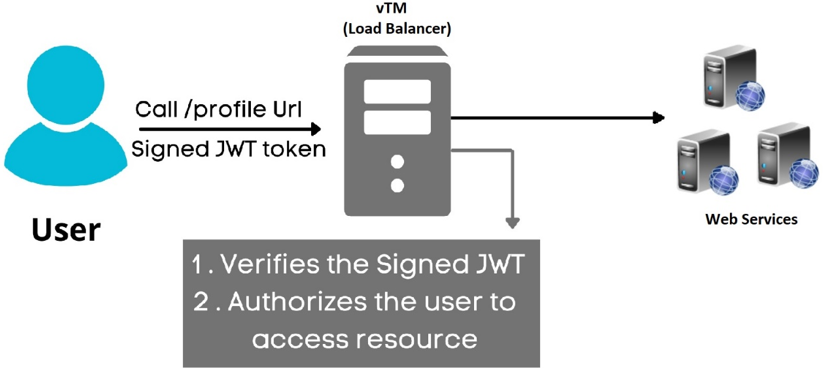
The signing and verification of JWT tokens requires cryptographic keys, either in the form of a shared secret, the public part of an asymmetric key-pair, or the entire key-pair depending on the desired mode of operation.
The Traffic Manager uses JWT catalogue to provide a centralized store of JWT keys. The JWT catalogue contains shared secrets, public and private keys that can be used to validate or generate a JWT, with the following vTM configuration:
•Import RSA/ECDSA Public Key - import a PEM encoded RSA or ECDSA Public Key
•Generate RSA/ECDSA Key Pair - generate public, private key RSA or ECDSA key pair
•Configure HMAC Shared Secret - configure a HMAC shared secret in base64 encoded format
Deployment Use Case
JWT is simply a standardized way of sending information between parties, and it is possible that a JWT token could safely send via,
•URL query parameters of a HTTP request – Not recommended. (JWTs could become too long for most browsers. Browsers have limits on the length of URLs, and it’s possible for JWT tokens to be longer than those limits.)
•Authorization header of a HTTP request – Recommended. (Authorization: Bearer <token>)
The Traffic Manager uses the following traffic script functions to parse, validate and generate the JWT tokens.
•jwt.parseheader( Input string ) : Parse the header of a JWT token and returns a hash of "error" and "description" if parsing fails else hash of key/value pairs present in header.
•jwt.validate( Input string, key, key_file, algorithm ) : Validates the JWT token against the provided key with expected algorithms and return the hash of "error" and "description" if validation fails or "claim" if validation is successful.
•jwt.generate( Input string, key, key_file ) : Generate the signature or digest for the input token( encoded jose header and claims ) using provided key and return the hash of "error" and "description" if generation fails or "signature" if generation is successful.
Configuring JWT on Traffic Manager
•Generate Private-Public Key Pair
Configure Public Key
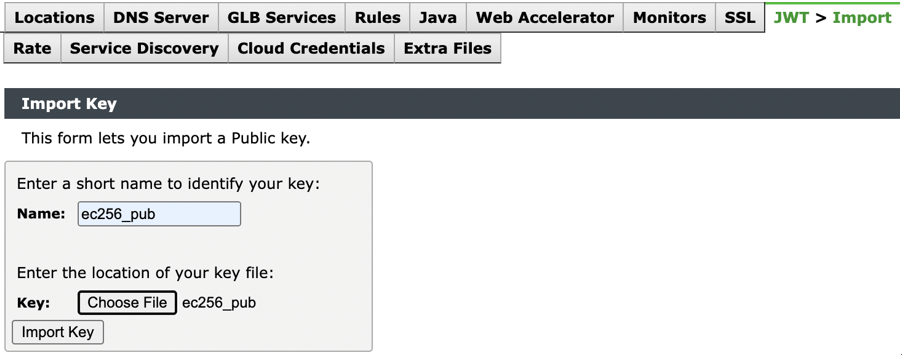
To configure public key on vTM:
1.Navigate to Catalogs > JWT > Import.
2.Enter the Name.
Name should be unique, and it should not match with other key names in JWT Public Key Catalog.
3.Click Choose Key and select public key file.
4.Click Import Key.
Generate Private-Public Key Pair
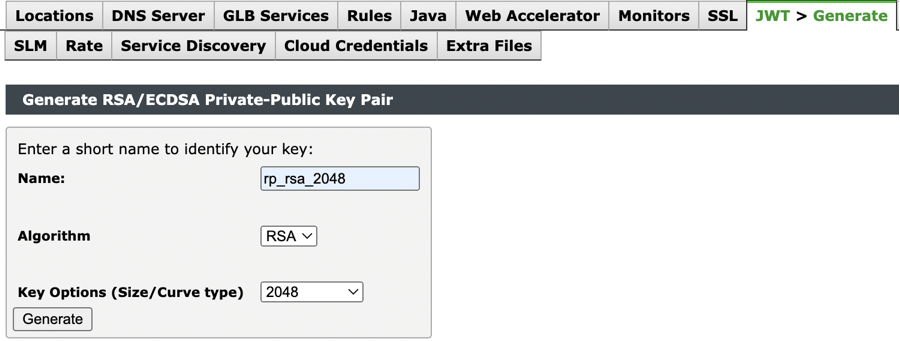
To generate private-public key pair on vTM:
1.Navigate to Catalogs > JWT > Generate.
2.Enter the Name.
Name should be unique, and it should not match with other key names in JWT Private-Public Key Catalog.
3.Select either RSA or EC from Algorithm drop-down box.
4.Select Key options as per RSA or EC from Key Options drop-down box.
5.Click Generate.
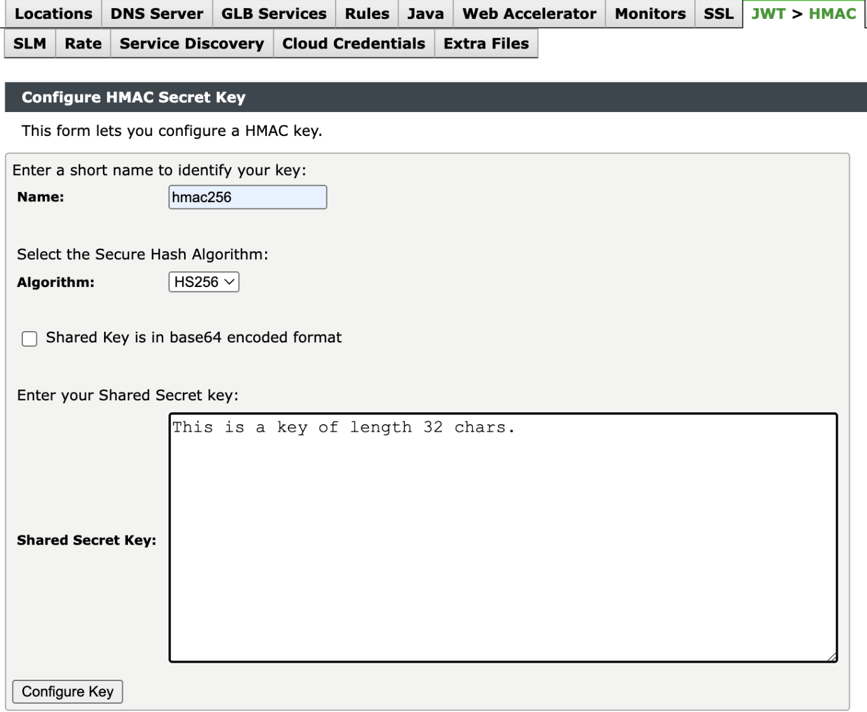
Configure HMAC Secret Key
To configure HMAC secret key:
1.Navigate to Catalogs > JWT > HMAC.
2.Enter the Name.
3.Select Hash Size from Algorithm drop-down.
4.Select Shared Key is in base64 format check-box if shared key is in base64 encoded format.
5.Enter the Shared Key in Text Box.
6.Click Configure Key.
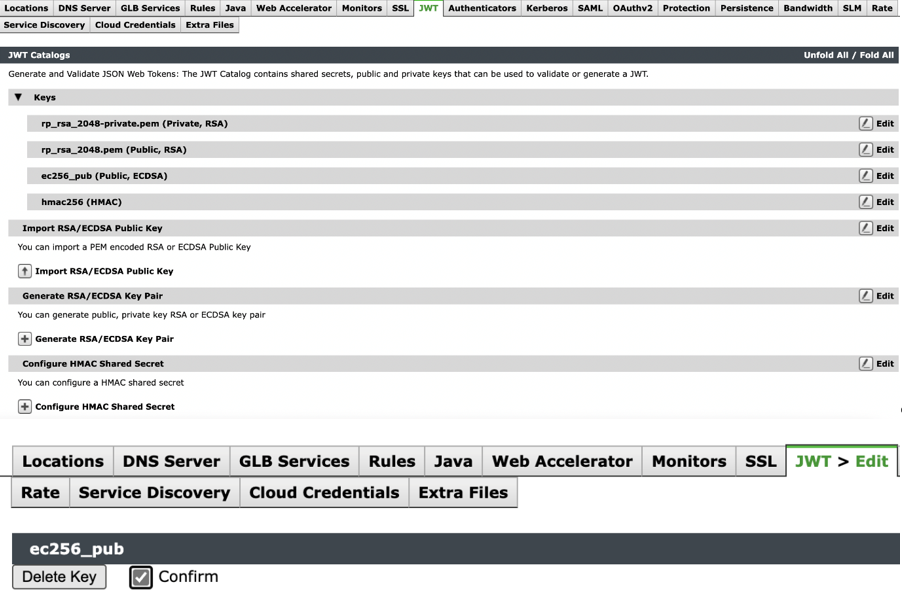
Delete Key
To delete the key on vTM:
1.Navigate to Catalogs > JWT.
2.Expand the Keys section to see the list of configured keys.
3.Select the Key you want to delete and click Edit.
4.In the Delete page, check Confirm box and Click Delete Key.