The Pulse Secure Virtual Web Application Firewall
Pulse Secure Virtual Web Application Firewall (vWAF) is an enterprise-level Web Application Firewall that provides attack detection and protection for the latest generation of mission-critical Web applications.
It enables centralized security monitoring, reporting and alerting and provides custom protection for your Web applications and infrastructure against external attacks.
This is an optional capability of the Traffic Manager that is only activated through the appropriate license key upgrade. Contact your support provider for more details.
Overview
vWAF is an optional component of the Traffic Manager. Once licensed and enabled in your cluster, it becomes fully integrated into the overall capability of the Traffic Manager software.
The Traffic Manager provides the infrastructure and overall control of your Web services, passing traffic to the vWAF when instructed to do so.
This chapter provides an overview of the vWAF and how it interacts with the Traffic Manager. For full instructions on configuring and using the vWAF, see the Pulse Secure Virtual Web Application Firewall: User Guide and on-line help.
Enabling the vWAF
ATTENTION
Do not enable the vWAF component on a mixed cluster of software and non-software instances of the Traffic Manager. This configuration is not supported.
To use the vWAF, obtain a suitable license key from your support provider. Once you have installed the new license, the Traffic Manager activates the System > Web Application Firewall page in the Admin UI. Use this page to enable, disable, and configure the vWAF component.
As with other configuration changes, enabling or disabling the vWAF on one Traffic Manager in your cluster automatically causes all other cluster members to make equivalent changes to their configuration.
vWAF Features in the Traffic Manager Admin UI
To control and configure the vWAF, use the button provided in the Traffic Manager navigation bar. This button operates as a toggle between the Traffic Manager and vWAF user interfaces.
You must enable the vWAF component to make this button visible.
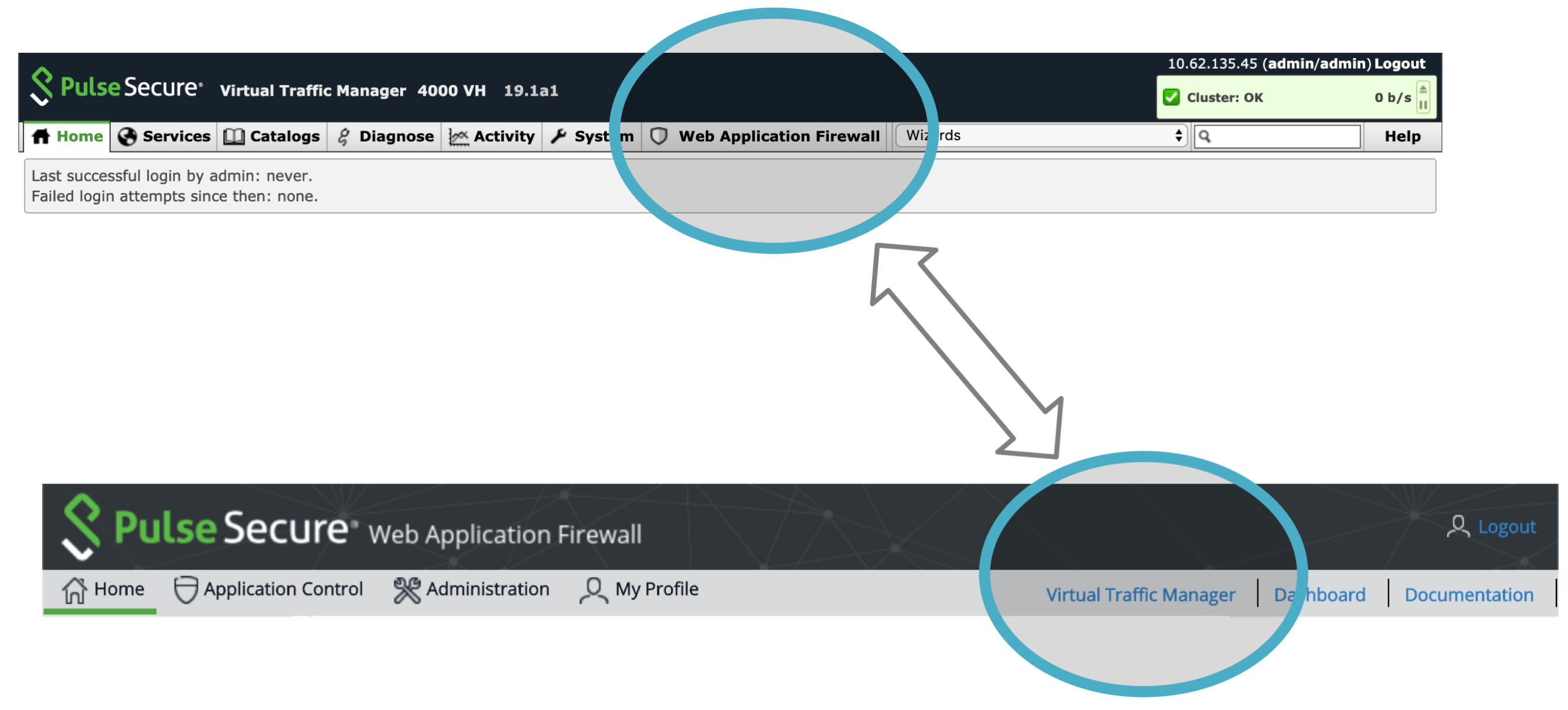
There are additionally a number of features in the main Traffic Manager Admin UI that govern vWAF communication and behavior:
•The System > Web Application Firewall page contains sections to enable and disable the vWAF component. It also contains low-level vWAF settings, including what network ports it uses and the number of processes it runs.
•A "Restart Web Application Firewall..." button is added to the Software Restart section of the System > Traffic Managers page. Certain configuration changes might require a restart of the vWAF without requiring the Traffic Manager itself to be restarted.
•The “Basic Settings” section of the Services > Virtual Servers > Edit page contains a control to enable or disable the vWAF for each of your HTTP services.
•The Rules catalog contains a new built-in TrafficScript rule, "Application Firewall Enforcer", that the Traffic Manager uses to maintain communication with the vWAF service.
•The Traffic Manager provides status messages in its event and audit logs relating to the vWAF service, particularly pertaining to its current running state. Any software stops, starts and restarts are recorded, along with specific configuration key changes and monitor errors. The vWAF also maintains its own local event log for attack and other event information relating to the security of your services. You can view this log through the vWAF Admin UI. See the Pulse Secure Virtual Web Application Firewall: User Guide for further information.
•A vWAF configuration section is present on the Diagnose page, which provides more detailed descriptions of any firewall problems that occur within your cluster. Should communication between the Traffic Manager and the vWAF be interrupted for any reason, the Status Applet shows that an error has occurred. Click on this error indicator to access the Diagnose page where you can see which particular problem has occurred and determine the appropriate action to remedy the situation.
The System > Web Application Firewall Page
This page contains configuration options for vWAF performance and communication.
During normal operation, you do not need to modify any of the settings in this section. The descriptions given here are for information only.
The vWAF requires a dedicated base port for communication between the Decider process and the Enforcer TrafficScript rule.
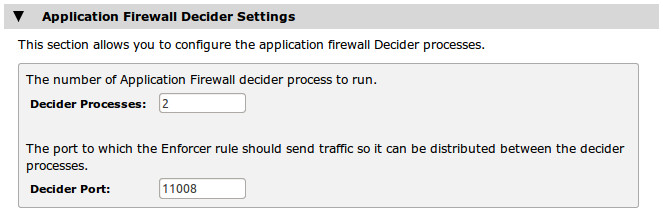
The factory default port is suitable for the majority of deployments, but you can specify a different value if this port is unavailable on your system. The vWAF restarts automatically if you change the settings on this page.
Use the "Decider Processes" setting to tune the performance of the vWAF according to the number of CPU cores available on your system. To handle more traffic and thus improve the performance of your system, increase this value to instantiate additional Decider processes, up to a maximum of 64. However, running more processes than there are free resources can inhibit performance and degrade the service. In these circumstances, reduce the number of processes to help increase overall system performance.
Ivanti recommends that you set the number of decider processes to be the same as the number of CPU cores available on the server with the fewest CPU cores in your Traffic Manager cluster. For example, if you have two Traffic Managers in your cluster, one with four CPU cores and one with two CPU cores, set the number of decider processes to 2.
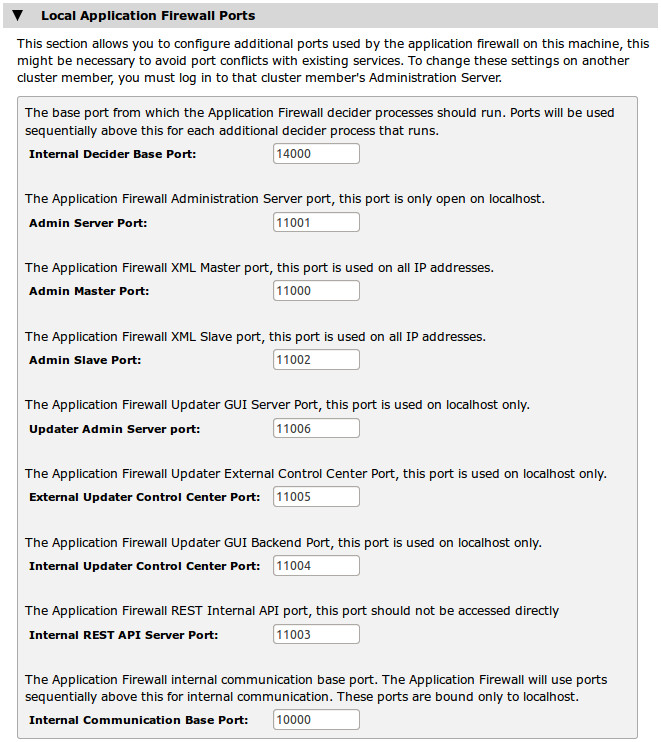
The vWAF requires a number of other ports for internal communication purposes. Under normal circumstances, you do not need to modify these default values. However, to resolve port number clashes, change the required port settings to alternative values on this page.
The Enforcer and Decider
The Traffic Manager’s Enforcer TrafficScript rule forwards requests to the default local port 11008 for inspection by the Decider service. The Decider returns a "Permit" or "Deny" decision and the Enforcer rule applies the decision.
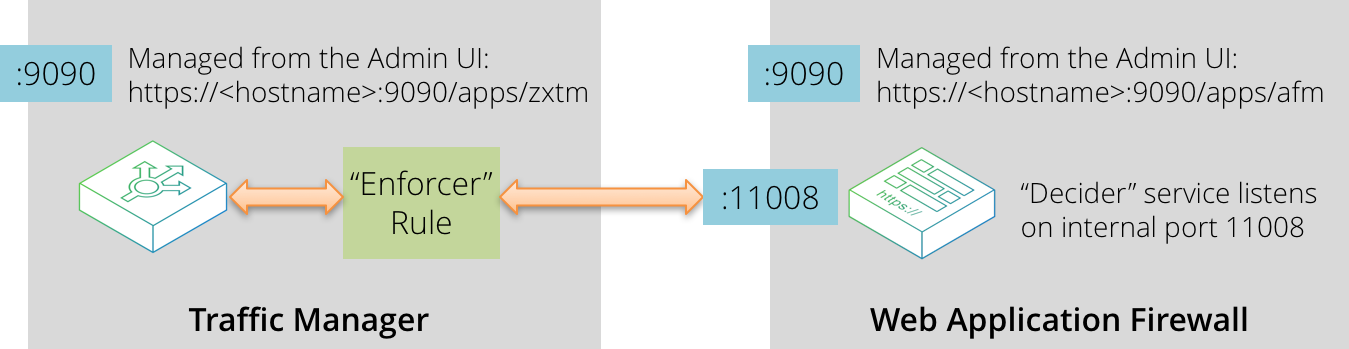
The “Enforcer” is a built-in TrafficScript rule (entitled "Application Firewall Enforcer") that enables communication between the Traffic Manager and the vWAF. It captures all HTTP requests and responses and forwards them to the “Decider” service running on the vWAF for further consideration.
The Decider uses a set of rules stored in a configuration database to evaluate HTTP requests and to make decisions on the actions to be carried out. The Enforcer then implements these decisions whereby each request or response is accepted, modified or denied as appropriate.
For more information on the Enforcer rule, see The Enforcer Rule.
The Enforcer Rule
The Traffic Manager communicates with the vWAF via the TrafficScript rule system, applying certain logic to the requests and responses generated by traffic to and from your Web applica When you enable the vWAF, a special rule entitled "Application Firewall Enforcer" (the Enforcer) is created to instruct the Traffic Manager to forward HTTP traffic to the Decider service. To attach this rule to your virtual servers, enable the Web Application Firewall setting on the Virtual Server > Edit page.
You cannot enable, disable, remove, or edit the Enforcer rule in the same way as other rules, but you can move it to alter the TrafficScript rule execution order. This is useful if you need to process requests or responses first. For example, you might have an additional rule that whitelists certain requests ahead of executing the Enforcer, as per the following TrafficScript:
connection.data.set( "enforcer.whitelist", 1 );
Like other rules, the Enforcer resides in the Rules Catalog. While you cannot delete the Enforcer rule, you can use the Save As functionality to create a copy.
Such copies look like, and provide the same options as, the original Enforcer rule. However, you should use them like traditional rules. In other words, you assign them to virtual servers, pools and rules in the normal way. Only the original Enforcer rule is assigned using a virtual server’s Web Application Firewall setting.
You can also set a number of configurable data items for the Enforcer. Click the rule name, or the Edit link, to access its settings page. The actual TrafficScript text is not immediately visible - click the Rule text link to display it. Note that it is in a binary format and is only partially human-readable.
The top of the rule text shows a number of configurable parameters. The Traffic Manager automatically updates the rule text with any modifications you make:
•allowonerror: Set to 1 to allow all traffic if the Decider is un-contactable. (default: 0)
•backend_timeout: The number of seconds to wait for the Decider before timing-out. (default: 5)
•bypass_enforcer_max: Set to 0 to block requests larger than enforcer_max_body_size from bypassing the vWAF. (default: 1)
•bypass_file_types: A space separated list of file extensions to exempt from the vWAF. (default: "css js png jpg gif")
•debug: Set to 1 to enable debugging mode. Use this option to provide a more verbose error output to assist in tracking down problems. (default: 0)
•discard_on_reject: Set to 1 to close rejected connections without sending an error message.
•enforcer_max_body_size: The maximum body size, in bytes, that the vWAF processes. Requests larger than this limit are blocked or bypassed depending on the setting of bypass_enforcer_max. (default: 2097152)
You should not normally need to modify these settings. Doing so may inhibit the ability of the rule to function correctly, so only proceed if you are fully aware of the consequences.
User Management
The Traffic Manager maintains user and group access with the vWAF. It creates a new vWAF user with the same level of authorization as a member of the “admin” group in the Traffic Manager Admin UI1. Performing usual administrative tasks does not require additional access privileges or login processing. Click Logout in either UI to log the user out of both applications.
ATTENTION
If you delete a user from the Traffic Manager, it is not automatically removed from the vWAF. An administrator must perform this step manually.
Members of other user groups in the Traffic Manager, such as “Demo” or “Monitoring”, only gain access to the various vWAF UI features if the correct permission settings exist on the System > Users > Groups > Edit Group page. The Traffic Manager provides settings in the System section for this purpose:
•Application Firewall: Controls access to the System > Web Application Firewall page in the Traffic Manager Admin UI.
•Application Firewall > Administration: Controls access to the vWAF Admin UI (through the toolbar button shown earlier).
You can override the automatic admin user creation mechanism by pre-defining user accounts in the vWAF Admin UI (if, for example, you want to specify limited access, or use a non-admin group). A user with the same name on the Traffic Manager will then have only the desired access in the vWAF Admin UI.
Updating Your Software
The vWAF includes a capability known as the Updater that is responsible for handling updates to the vWAF software component. You can access the Updater through the Administration > Cluster Management tab of the vWAF Admin UI. See the Pulse Secure Virtual Web Application Firewall: User Guide and on-line help for more information.