How vWAF Works
vWAF is installed as a software plug-in on your existing web server. Therefore, you do not need to make any changes to the current network infrastructure. In addition, vWAF is located in exactly the right place to analyze data that was previously SSL-encrypted, without any additional work required.
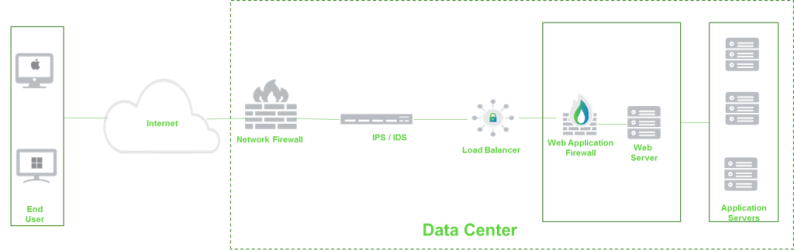
Workflow
Before a request reaches a web application, vWAF intercepts and analyzes it. In this process, an optimized combination of white/black and gray list processes, pattern detection of known attacks, and various statistical methods evaluate each request for its potential danger level. Each request is clearly assigned to one of following classes:
- Legitimate requests are forwarded to the web application.
- Obvious attacks are denied. At the same time, vWAF stores as much data as possible to identify and track the attacker.
- Requests in which the danger level can’t be fully assessed locally are denied or forwarded depending on the local evaluation and the security policy installed. In addition, vWAF logs them internally and uses them to further analyze subsequent requests.
Thanks to the continuous analysis process, over time vWAF collects important information on the behavior of your web application and can continue to optimize the protection on that basis.
In the other direction, vWAF also analyzes the responses of your web application. This means that information relating to security, such as credit card numbers, can be filtered out from the responses and doesn’t reach the outside world even in the event of a successful attack.
System Components
vWAF consists of the following key components:
- The administration interface is an easy-to-use, web-based user interface for administering the security configuration and for accessing log files and statistics.
- The administration server handles and distributes the configuration data of your individual security configuration, as well as log files and statistics.
- The Enforcer is a TrafficScript Rule that integrates Brocade Virtual Traffic Manager (Traffic Manager) with vWAF. The Traffic Manager captures every HTTP request and forwards it to the vWAF decider for further consideration. The decisions made by the decider are then implemented.
The Decider uses the set of rules that are stored in the configuration database to evaluate HTTP requests and to make decisions on the actions to be carried out. In addition, on all computers there is also an updater, which helps you to keep the vWAF installation up to date with minimum effort.
Deployment Scenarios
vWAF can either be installed on a standalone Traffic Manager, or installed on each machine in a cluster of Traffic Managers. When installed as part of a cluster, vWAF installations share their configuration with each other. Traffic, however, is processed by the decider processes belonging to the vWAF installed on the Traffic Manager that received the request or response.
The number of decider processes running on each Traffic Manager is the same and is determined by the number of CPUs on the Traffic Manager with the fewest CPUs.
Client Compatibility
On the administration side as well, you can integrate vWAF seamlessly into your existing structures. If you are operating multiple web applications in your company, you can define access authorization individually for different staff members in vWAF. Optionally, you can also set up user groups with limited permissions.
This is a common scenario. The administration of vWAF itself – in other words, its integration into the IT infrastructure, the management of the web application being protected, and relevant access authorizations – is carried out centrally, for example, by a designated staff member in the area of network security. The individual web applications are protected separately by different designated staff members. These persons only have access authorization to the security configuration of “their” web application. They are fully familiar with the special features and structures of that web application and can therefore protect it in the most effective way.