Malware detection
Purpose
In the case of a successful attack, hackers might be able to manipulate your web application so that it returns malicious code to its users. Malware detection can identify such malicious code and remove it “on the fly”. To the user, your web application continues to work as intended, until you’ve been able to resolve the problem.
How malware detection works
Malware detection works in cooperation with an external malware detection service. This service scans your web application at regular intervals. vWAF communicates with the service. If the service has found any malicious code, vWAF automatically retrieves information about this code. vWAF then internally adds an invisible handler, which dynamically filters out the malicious code from all responses of your web application. Currently, malware detection exclusively works with the HackAlert service of Armorize Technologies (https://hackalert.armorize.com).
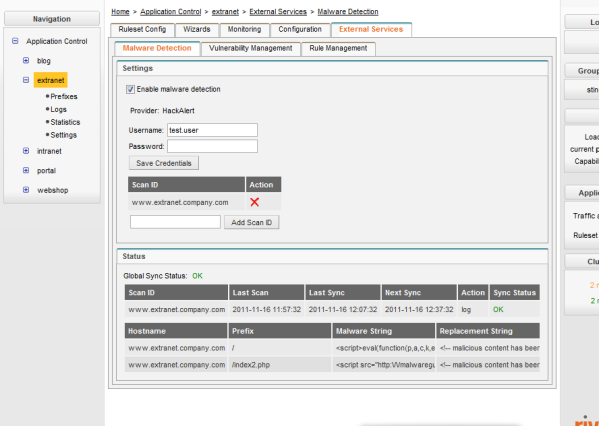
By checking the log files for the Malware Detection Handler, you can find out and document when malware detection has filtered out malicious code. The most recent replacements are also visible on the Malware Detection tab (see section on status information below).
Opening
To access the Malware Detection tab:
Enabling malware detection
To enable malware detection, activate the Enable malware detection check box.
Important: For malware detection to actually work, you must have a valid user account with one of the supported malware detection service providers, and you must enter your user account data for the used malware detection service (see following sections).
Choosing a malware detection provider
Currently, malware detection exclusively works with the HackAlert service of Armorize Technologies (https://hackalert.armorize.com).
Entering user account data
To be able to query the external malware detection service, you must specify the user data that you’ve been given by your service provider. This includes username, password, and the host names of all scanned applications (Scan IDs).
The username and password are stored in the vWAF configuration database (unencrypted). Communication with the external malware detection service provider usually uses HTTPS (depending on provider).
| Column | Meaning |
|---|---|
|
Scan ID |
ID or host name of an application. This ID has been given to you by your malware detection service provider |
|
Last Scan |
Date and time of the most recent scan that was run by the external malware detection service. |
|
Last Sync |
Date and time of the most recent synchronization between vWAF and the external malware detection service provider. |
|
Next Sync |
Date and time of the most recent synchronization between vWAF and the external malware detection service provider. |
|
Action |
It depends on the external malware detection service which actions are possible:
|
|
Sync Status |
Indicates whether or not the most recent synchronization with the external malware detection service provider has been successful (status OK). If any error has occurred, an error message informs you about the reason of failure. |
|
Hostname |
Hosts (configured in vWAF) for which malware detection has been enabled and on which the external malware detection service has detected some malware. |
|
Location |
Shows you where exactly the malware has been detected. |
|
Malware String |
Malicious code that has been found. |
|
Replace String |
String that vWAF inserted dynamically instead of the malicious code when answering the request. |