Audit Log
Purpose
The Audit Log documents the actions of all administrators. This includes, for example, administrator logins, creating new administrators, adding and deleting applications, updating cluster slaves as well as committing and activating rulesets. This means that all changes made to the system can be tracked in full, complete with when and by whom. The last actions carried out are at the top of the table.
For a detailed list of all log file entries possible, please refer to Entries in the Default Error Log.
If you need a printable version of the Audit Log, you can also create a report (see Reports). A daily Audit Log is included there, too.
Opening
To open the Audit Log, select the menu item .
You can select the time range, and you can sort and filter the table (see Monitoring Attacks, Statistics, Log Files, Reports for a description of the log files).
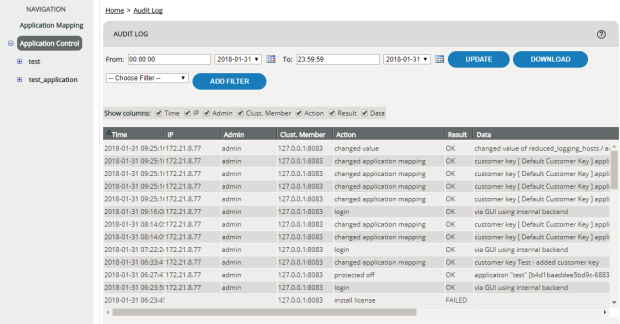
Data displayed
| Column | Meaning |
|---|---|
|
Time |
Date (YYYY-MM-DD) and time at which the action was carried out. |
|
Admin |
Administrator who carried out the action. |
|
What |
The action carried out (see Entries in the Audit Log). |
|
Data |
Specific data held on the action carried out. |