Alert-Based Admission Control with Fortinet Products
This chapter describes how to integrate FortiAnalyzer and FortiGate Firewall products with Ivanti Policy Secure to support Alert-based admission control in your network.
Overview of Alert-Based Admission Control with Fortinet Products
Ivanti Policy Secure integration with network security devices provide user access control based on the threats identified by the network security devices.
The network security device provides detection of threats based on the intrusion prevention system. This helps in detecting unknown threats, and also reduces the number of false alarms.
The network security device uses the syslog events mechanism to notify the other devices regarding the network threats. Ivanti Policy Secure also supports dynamically changing the access to the user based on the information received from the network security device.
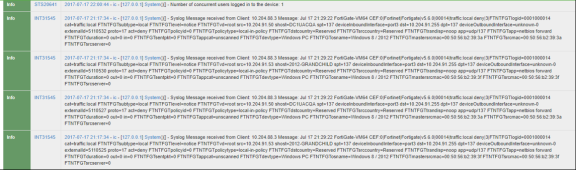
The admission control user flow is described below:
- The user connects to Ivanti Policy Secure through the Switch (or Wireless LAN Controller).
- The user session is created on the Ivanti Policy Secure.
- The user details are pushed to the Switch for enforcing user access.
- The FortiGate Firewall monitors the user traffic.
- The FortiAnalyzer generates the syslog messages for the user.
- The syslog message is sent to Ivanti Policy Secure if any suspicious traffic or activity is detected from the user.
- Ivanti Policy Secure processes the received syslog message and, based on the configured policies, actions are taken.
- New/Updated details are pushed to Switch for updating the enforcement of the user.
The enforcement of the user is also updated on the FortiGate Firewall.
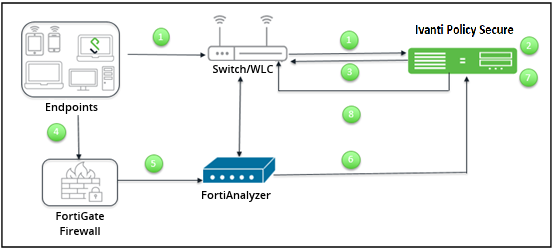
For example, a user is connected to Ivanti Policy Secure and wants to access protected resource which is behind FortiGate Firewall. Users get access to the resource, and when the firewall detects a threat from the user, the firewall sends a syslog message and user is removed from the network.
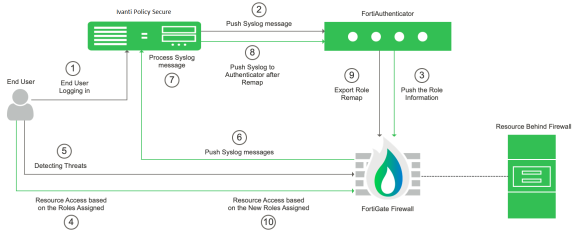
The dynamic identity enforcement using admission control user flow is described below:
- The user connects to Ivanti Policy Secure through the Switch (or Wireless LAN Controller). User is authenticated on Ivanti Policy Secure after validating the HC policy.
- The syslog sessions are exported to FortiAuthenticator.
- Identity information is parsed from the Syslog message and is used to create an IP to username mapping within FortiAuthenticator. This information is shared with FortiGate firewall in the form of a Fortinet Single Sign-On (FSSO) record.
- The firewall uses this information to either allow or block traffic based on the configured policy
- FortiGate Firewall Monitors the end user flow and activity and detects attacks/malicious activity at the end user session
- FortiGate Firewall/Analyser sends a syslog message to Ivanti Policy Secure for any suspicious traffic or activity detected from end user.
- Ivanti Policy Secure process the received syslog message and based on the configured policies, action will be taken for the end user session.
- Ivanti Policy Secure exports New Roles to the FortiAuthenticator.
- The firewall changes users Role based on the information received from Authenticator.
- User gets access to the protected resources based on the new role assigned.
Summary of Configuration
To prepare your network to use alert-based access control using Ivanti Policy Secure, FortiAuthenticator, FortiAnalyzer and FortiGate Firewall, perform the following tasks:
- Configuring Network Security Devices with Ivanti Policy Secure
- Configuring FortiGate Firewall
- Configuring FortiAnalyzer
- Confirming Syslog Forwarding
Configuring Network Security Devices with Ivanti Policy Secure
The network security devices are configured with Ivanti Policy Secure for admission access control. A high-level overview of the configuration steps needed to set up and run the integration is described below:
- The Administrator configures the required syslog clients on the Ivanti Policy Secure Admin UI. Each network security device acts as a syslog client on which syslog forwarding is enabled, and Ivanti Policy Secure receives the forwarded syslog messages.
- The Administrator then configures a set of policies that define what actions are to be taken on user sessions, based on the data in the threat events.
- The user defined templates are used to map the data and the predefined variables. The predefined variables in the template are Rule Name, Source IP Address, Source User, and Severity.
- The templates for parsing the syslog messages from Fortinet Firewall/Analyzer are available by default. The administrators can also add customised templates for integrating with other network security devices.
This section covers the following topics:
- Configuring an Admission Control Template
- Configuring Admission Control Policies
- Configuring the Admission Control Client
Configuring an Admission Control Template
The admission control template provides a list of possible events that can be received from the network security device, along with a regular expression to parse the message. The template also provides possible actions that can be taken for an event.
Only the admission control policy defines the actions to be taken on receipt of an event. The admission control template only provides possible events and possible actions for that event.
To view and add the admission control templates:
-
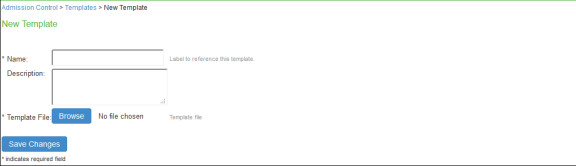
Select Endpoint Policy > Admission Control > Templates.
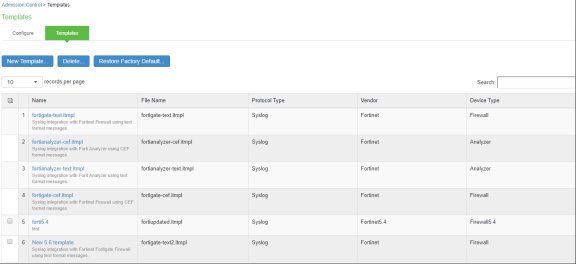
-
Click New Template.
-
Enter the template Name.
-
Enter a template Description.
-
Click Browse and select the template file.
-
Click Save Changes.
Configuring Admission Control Policies
The admission control policies define the actions that are performed on Ivanti Policy Secure for user sessions. The actions are based on the specific threat event information received from the network security device.
To view and add the new integration policy:
-
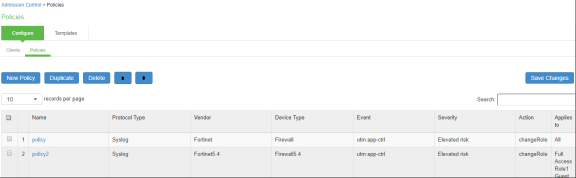
Select Endpoint Policy > Admission Control > Policies.
-
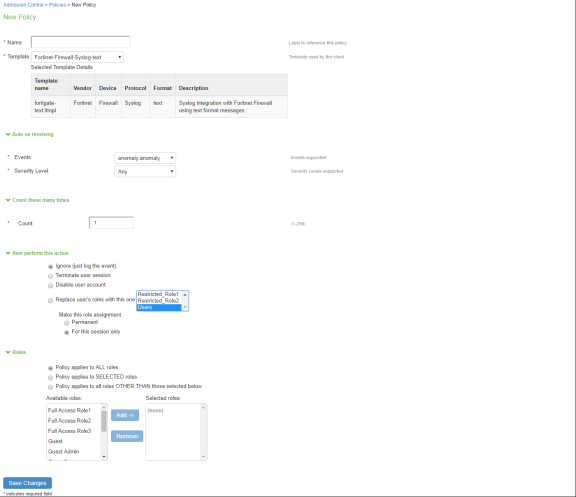
Click New Policy.
-
Enter the policy name.
-
Select the template used by the client. The following templates are available by default for Fortinet:
- Fortinet-Analyzer-Syslog-CEF
- Fortinet-Analyzer-Syslog-text
- Fortinet-Firewall-Syslog-CEF
- Fortinet-Firewall-Syslog-text
-
Under Rule on Receiving, select the event type and the severity level. The event types and the severity level are based on the selected template.
-
Under Count these many times, enter a number between 1-256.
-
Under Then perform this action, select the desired action.
- Ignore (log the event): Received syslog event details are logged on the Ivanti Policy Secure and no specific action is taken.
- Terminate user session: Terminates the user session on the Ivanti Policy Secure for the received messages.
- Disable user account: Terminates the user session and disables the user on the Ivanti Policy Secure for the received messages.
- Replace user role with this role: Changes the roles assigned to the user on Ivanti Policy Secure so that restriction/privileges for the user can be changed.
You must specify whether to apply the role assignment permanently or only for the session.
-
Under Roles, specify:
- Policy applies to ALL roles: Applies the policy to all users.
- Policy applies to SELECTED roles: Applies this policy only to users who are mapped to roles in the Selected roles list. You must add roles to this list from the Available roles list.
- Policy applies to all roles OTHER THAN those selected below: Applies this policy to all users except for those who map to the roles in the Selected roles list. You must add roles to this list from the Available roles list.
-
Click Save Changes.
Configuring the Admission Control Client
The admission control clients are the network security devices on which the syslog forwarding is enabled. The messages are received by the syslog server module running on Ivanti Policy Secure.
You must add either the FortiGate Firewall or the FortiAnalyzer as separate clients on Ivanti Policy Secure to enable it to receive the required threat information through syslogs.
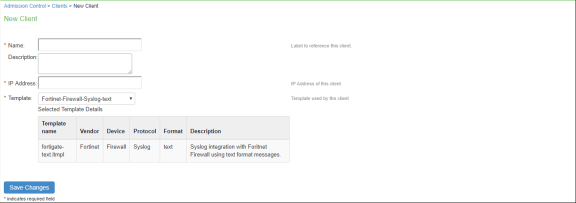
To add a client:
-
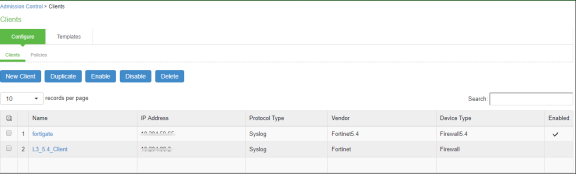
Select Endpoint Policy > Admission Control > Clients.
-
Click New Client.
-
Enter the Name of the client that will be added in the Ivanti Policy Secure.
-
Enter a Description.
-
Enter the IP Address of the client.
-
Select the Template for the client.
- Fortinet-Analyzer-Syslog-CEF
- Fortinet-Analyzer-Syslog-text
- Fortinet-Firewall-Syslog-CEF
- Fortinet-Firewall-Syslog-text
-
Click Save Changes.
Configuring FortiGate Firewall
Once you have added the FortiGate Firewall as a syslog client on Ivanti Policy Secure, the Ivanti Policy Secure must be added as a syslog server on the FortiGate Firewall.
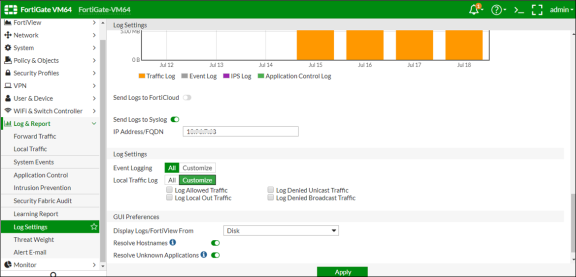
To configure FortiGate Firewall:
-
Select Log & Report > Log Settings.
-
Enable Send Logs to Syslog.
-
Enter the IP Address/FQDN of the Ivanti Policy Secure device and click Apply. The Ivanti Policy Secure is added as a syslog server.
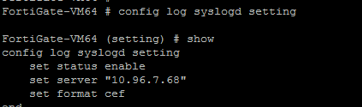
-
The default syslog format is text. You must use the following Command-Line user Interface (CLI) to change the format to CEF.
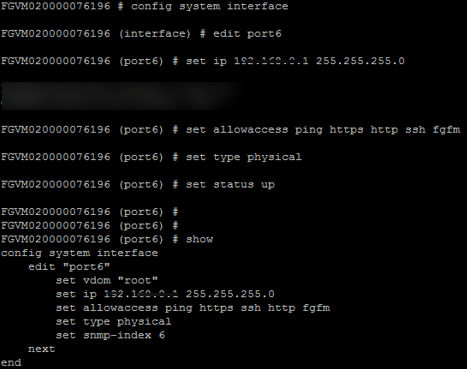
-
To access the firewall, you must configure the firewall management interface settings from the CLI.
-
Under Interfaces, configure the trust and untrust zones.
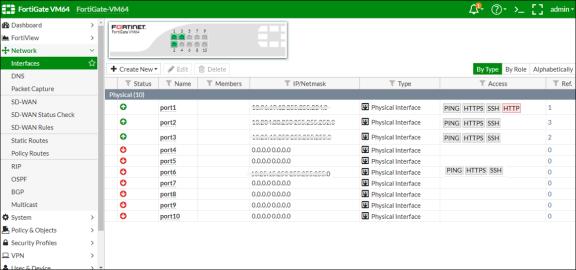
-
Under Security Profiles > Application Control, create a security profile.
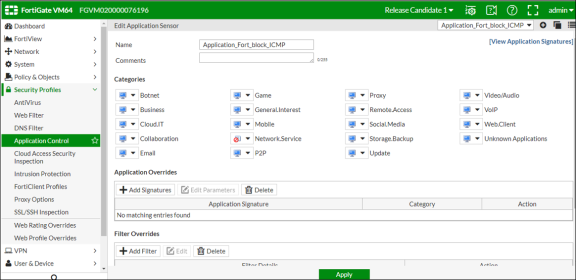
-
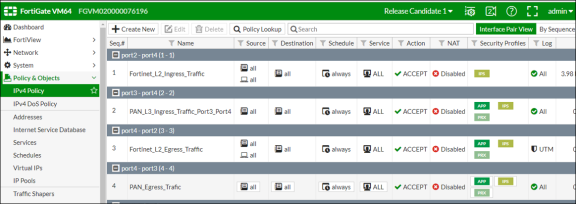
Under Policy & Objects, apply policies to desired port.
Configuring FortiAnalyzer
Once you have added the FortiAnalyzer as a syslog client on Ivanti Policy Secure , the Ivanti Policy Secure must be added as a syslog server on the FortiAnalyzer.
-
Configure the FortiAnalyzer management interface using its Command-Line user Interface (CLI).
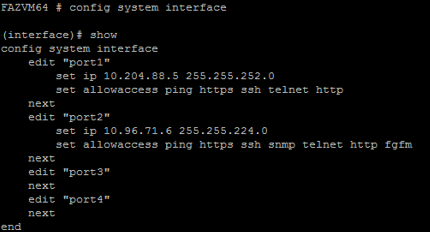
-
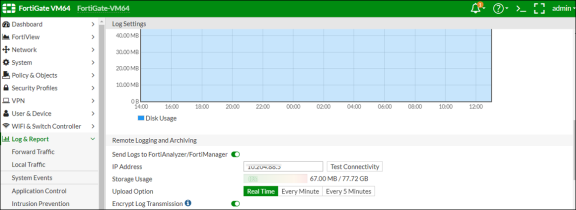
On the FortiGate Firewall, under Log & Report, enable Send Logs to FortiAnalyzer/FortiManager to forward the syslog message to FortiAnalyzer. Enter the IP Address of the FortiAnalyzer.
On FortiGate Firewall, ensure you have configured the security policy’s network trust, untrust zone and apply the policy to desired ports.
-
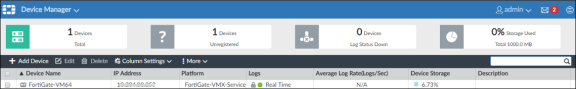
Under FortiAnalyzer > Device Manager, click Add Device to add the FortiGate Firewall.
-
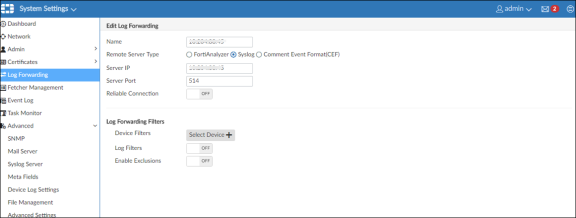
Under System Settings > Log Forwarding > Edit Log Forwarding, enter the IP address of the Ivanti Policy Secure device for log forwarding.
-
Under System Settings > Advanced > Syslog Server, enter the IP address of Ivanti Policy Secure device.
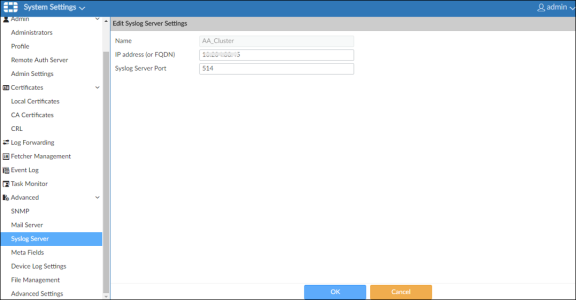
Confirming Syslog Forwarding
When the network security device detects a threat, the syslogs are forwarded to Ivanti Policy Secure. To verify the event logs have been received on Ivanti Policy Secure, select System > Log/Monitoring > Events > Log.