User Experience
From the user perspective, Pulse Client presents a clean, uncomplicated interface. The user can enter credentials, select a realm, save settings, and accept or reject the server certificate. When you configure the client, you can specify whether to permit end users to modify settings, such as by adding connections.
Security Assertion Markup Language (SAML) Authentication
Pulse Client facilitates SAML authentication for Single Sign-on (SSO) in the following two ways:
•The Pulse Client user sees an embedded browser (see figure) - if Enable embedded browser for authentication is enabled in “Pulse Client Connection Set Options” on page 136.
Pulse Client will close the embedded browser, once the SAML authentication is done.
If user resizes the Embedded browser window, size will remain same even if user reconnects to Pulse Client. Embedded browser window size will remain as pre-selected size which was set by the user for the first time, until user resizes it again.
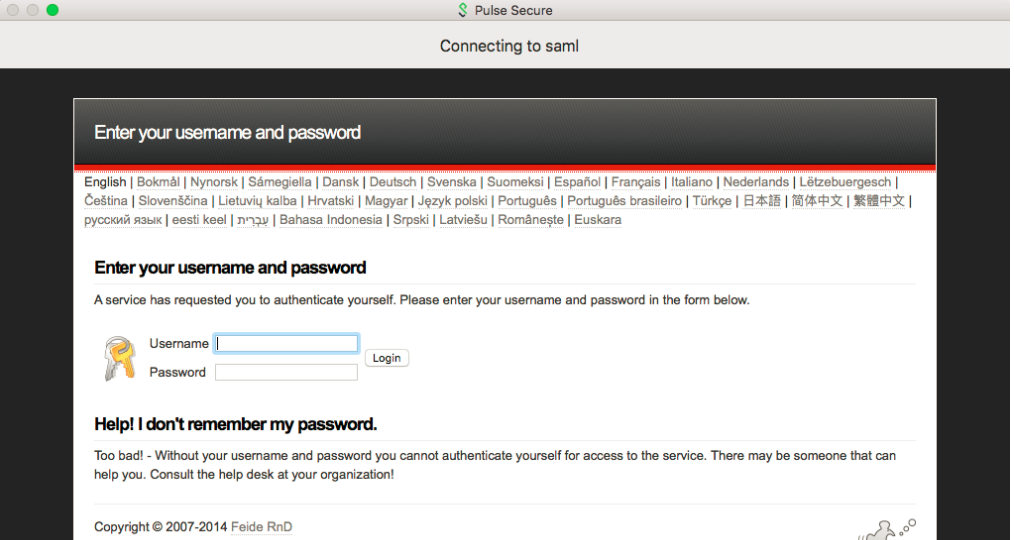
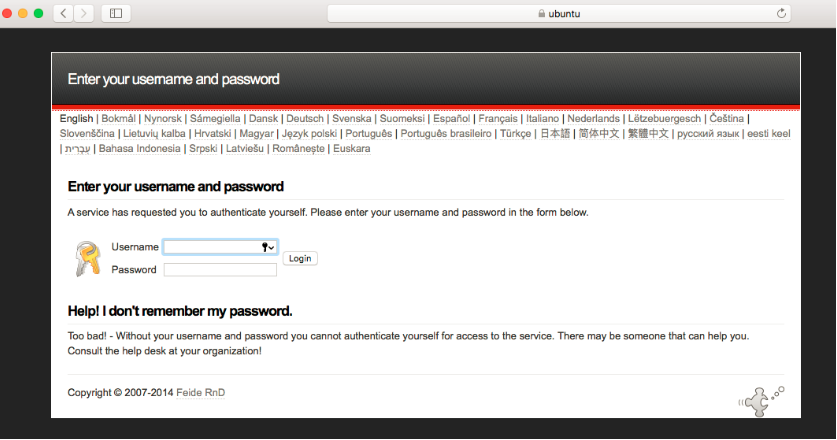
•The Pulse Client user sees an external browser (see figure). if Enable embedded browser for authentication is disabled in “Pulse Client Connection Set Options” on page 136.
Single Logout
Single logout is a mechanism provided by SAML for logging out a particular user from all the sessions created by the identity provider.
Pulse client supports Single Logout only when embedded browser is enabled.
Select this option if the system must receive and send a single logout request for the peer SAML identity provider. If you use the metadata option, the Single Logout Service URL setting can be completed by selecting the SLO service URL from the list. The list is populated by the identity provider entities defined in metadata files added to the System > Configuration > SAML page. The system sends Single Logout requests to this URL. In addition, if you use the metadata option, the Single Logout Response URL setting is completed based on your selection for Single Logout Service URL.
If the identity provider has left this setting empty in its metadata file, the system sends the Single Logout response to the SLO service URL. If you complete these settings manually, ask the SAML identity provider administrator for guidance. The Support Single Logout service for the identity provider must present a valid certificate.
Custom Sign-in Page in Embedded browser
To upload a custom sign-In page in Pulse Client, admin needs to perform the following steps:
1.Log into Pulse Connect Secure/Pulse Policy Secure as admin.
2.Go to Authentication > Signing-In > Sign-In Pages > Upload Custom Sign-In Pages.
3.Select the option Use Custom Page for the Pulse Desktop Client Logon.
4.Click Browse and select the custom sign-in page file and click Upload Custom Pages.
5.Go to Signing In > Sign-In Policies > New Sign-In Policy to create the new Sign-In policy.
6.Under Sign-In page, select the uploaded custom page from the drop-down box to associate custom Sign-In page with the Sign-In Policy.
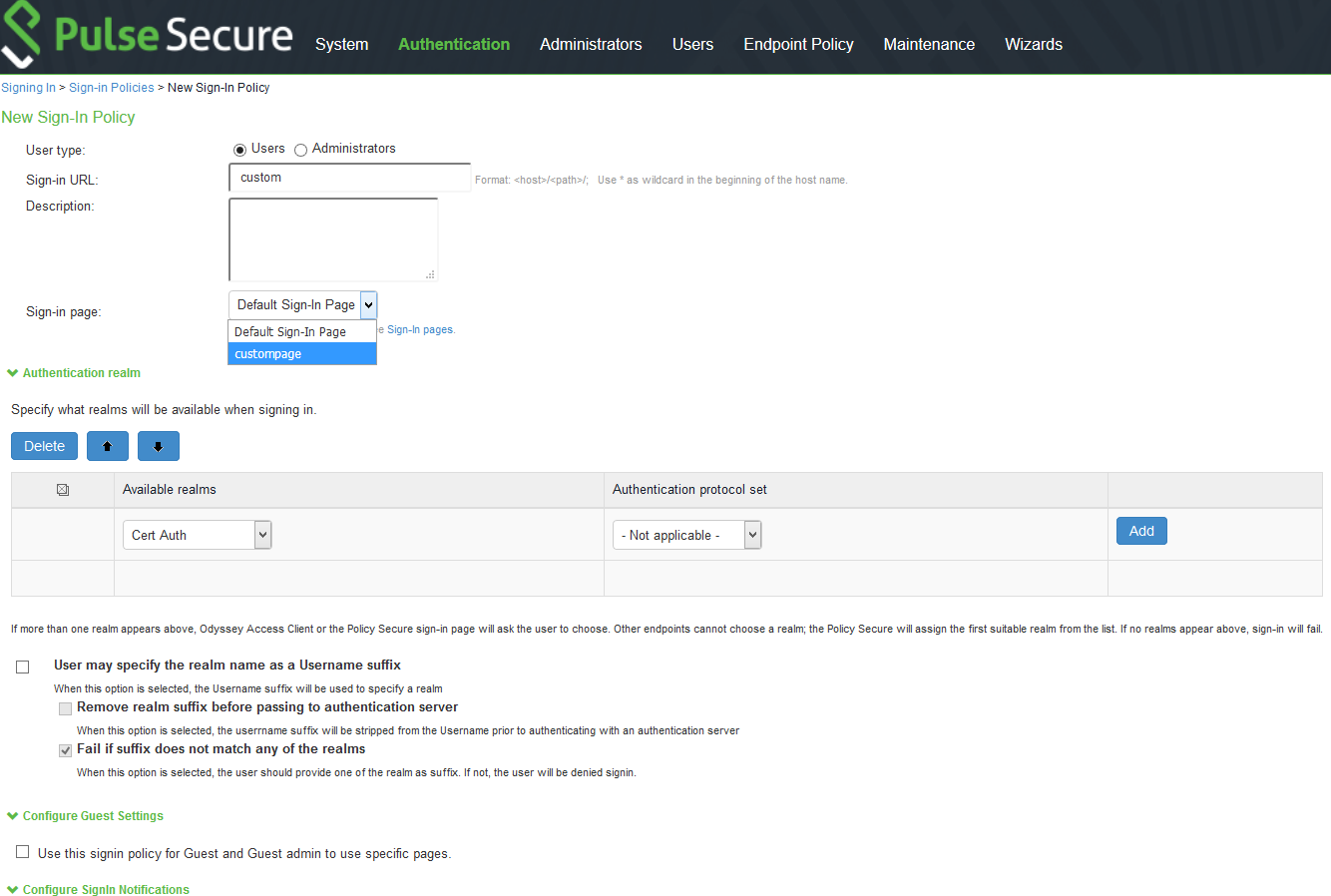
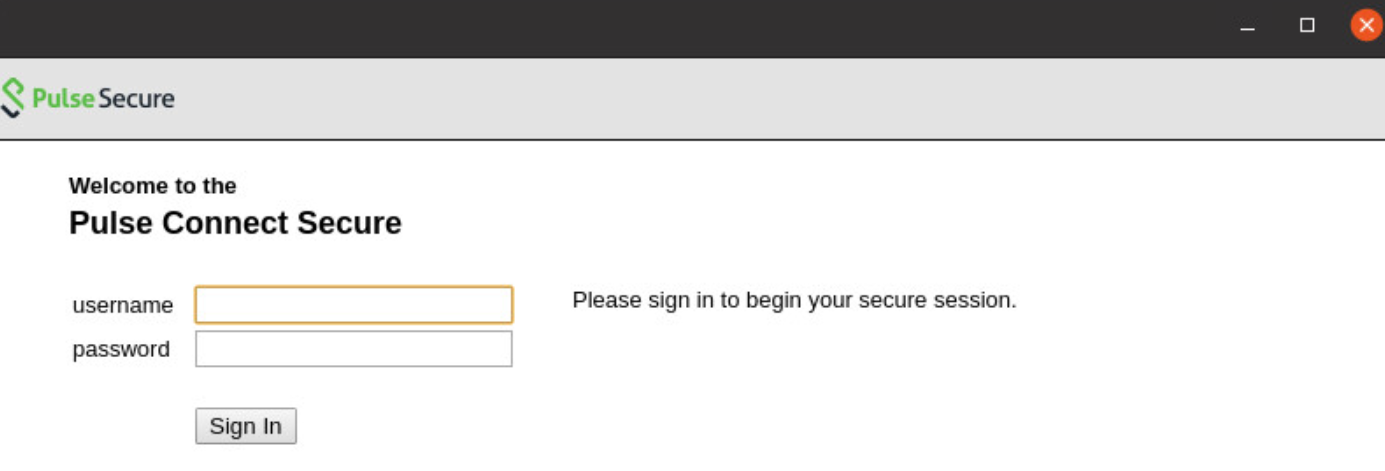
Pulse Client can open a custom sign-In page in the following two ways:
•A Pulse Client user sees an embedded browser (see figure) if Enable embedded browser for authentication is enabled.
Pulse Client closes the embedded browser once the authentication is done.
Whenever user logs into the custom sign-in URL from Pulse Client, embedded browser will be launched with custom sign-in pages uploaded into it.
L3 and Pulse SAM Coexistence
L3 and Pulse SAM coexistence (supported on Windows only) enables the user to establish Layer 3 connection to Pulse Connect Secure and Pulse SAM connection simultaneously (refer to ). This feature is available from 9.0R3 onwards.
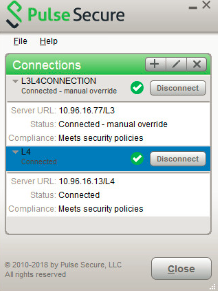
To achieve, L3 and PSAM coexistence, Pulse Client should have minimum two Pulse Connect Secure connections, each for L3 and PSAM. Also, maximum three active user connections are allowed at once.
Limitation for L3 and Pulse SAM coexistence:
•At any given point, for any user only one L3 and one L4 is supported.
With L3 and PSAM coexistence, the way the packet is tunneled, depends on how the L3 and PSAM tunnel are configured. It can be done in following two ways:
Following are the 2 scenarios, where L3 and PSAM coexistence is supported.
Scenario-1: PSAM is behind L3
PCS1 has L3 tunnel configuration and PCS2 is behind PCS1.
If specific set of resources is not accessible on PCS1 server and needs to access from PCS2 server, which is accessible through PCS1 server, then additional authentication is needed to access PCS2 server. As access to PCS2 server is possible only after making connection to PCS1 server, it is the case of PSAM tunnel inside L3 tunnel.
Scenario-2: L3 and PSAM are independent
PCS1 has L3 tunnel configuration and PCS2 has Pulse SAM configuration.
L3 Connection for Pulse Connect Secure is established, split tunneling should be enabled and exclude the PCS2 IP from the spilt tunneling networks.
If single user needs to access two different set of resources available on PCS1 and PCS2, then one specific set of resources is under PCS1 and another set of resources is under PCS2.
As PCS1 and PCS2 are at different locations and user can not establish two L3 connections to access both set of resources on PCS1 and PCS2, so PSAM can provide the secure access to set of resources on PCS2.
L3 based FQDN Split Tunneling feature with PSAM coexistence is not supported.
HVCI Compatibility
Pulse Client for Windows is compatible with Microsoft Windows 10 HVCI settings. Windows 10 HVCI settings are part of Windows Device Guard security features for mitigating cybersecurity threats. When HVCI is enabled, Windows OS performs code integrity checks and allows only secured applications. Pulse Client for Windows is compatible with these settings which would help customers adopt the latest security features of Windows.
Pulse SAM IPv6 Support
Pulse SAM IPv6 support is available for Windows 8.1 and later.
Internet Protocol Version 6 (IPv6) is the protocol designed to succeed Internet Protocol Version 4 (IPv4). From 9.1R1 release onwards, Pulse SAM (PSAM) will support IPv6 Pulse SAM tunneling along with IPv4 Pulse SAM tunneling with the help of new option for internet traffic filtering, Windows Filtering Platform (WFP) driver.
WFP driver supports both IPv6 and IPv4, however TDI driver supports only IPv4. WFP driver allows the user to provide a deeper inspection and control of packets by modifying or examining TCP/IP traffic at any TCP/IP stack layer.
Administrator can switch from WFP driver (supporting both IPv6 and IPv4) to classic TDI driver (supporting IPv4 only) with fallback mechanism, in case of any issue due to WFP driver installation.
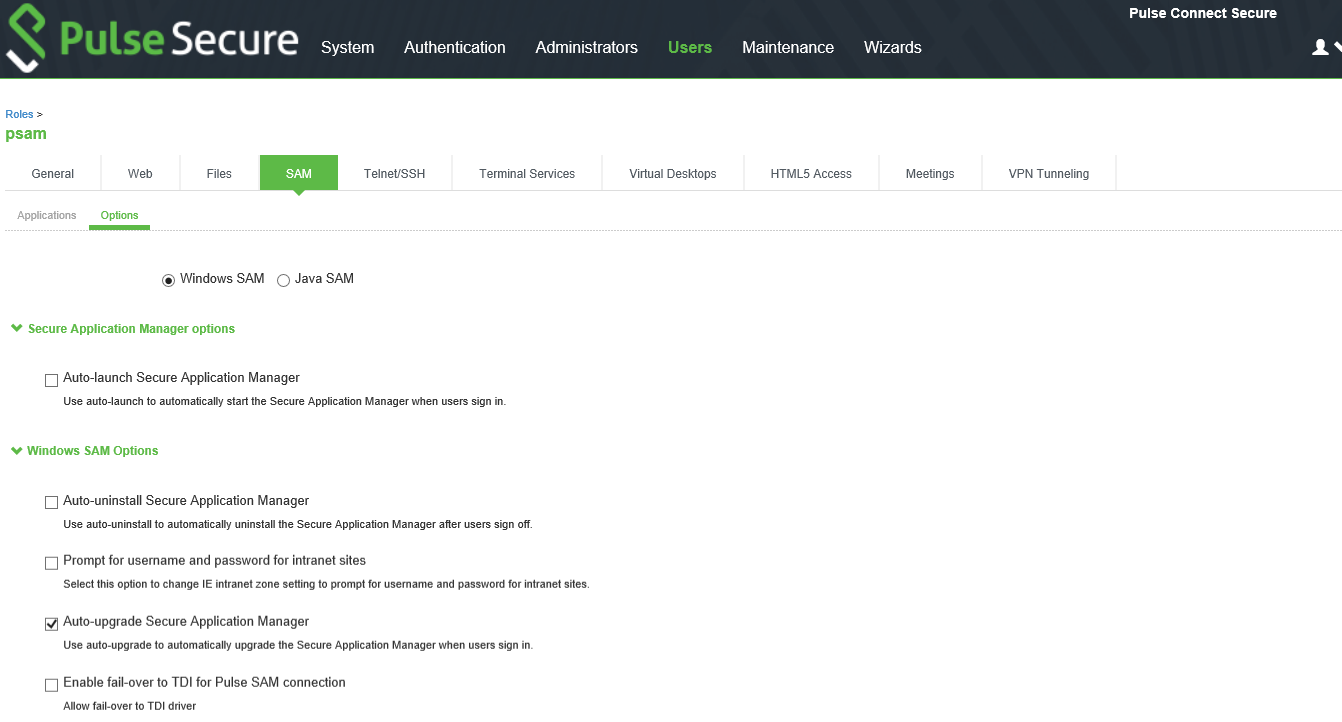
Following are the steps to switch from WFP to TDI:
1.Go to Users > User Role.
2.Select the role.
3.Go to SAM > Options. The screen in figure appears.
4.Select Enable fail-over to TDI for Pulse SAM connection.
Benefits
Following are the benefits of this feature:
•PSAM will be able to filter the traffic from Windows 10 and Windows 8.1 Metro Mode Applications.
•PSAM will be able to filter the traffic from Internet Explorer 11 with Enhanced Protected mode.
•PSAM will support Dual Stack (both IPv6 and IPv4).
Deployment Scenarios
The following table summarizes the IPv6 in IPv6, IPv4 in IPv6 and IPv6 in IPv4 scenarios:
|
PDC |
Endpoint |
PCS External Interface |
PCS Internal Interface |
Tunnel |
Description of the Connection |
|
Dual Stack or IPv6 only |
Dual Stack (IPv6 and IPv4) or IPv6 only |
IPv6 |
Dual Stack or IPv6 only |
IPv6-in-IPv6 |
IPv6 resource on IPv6 PSAM session. |
|
Dual Stack or IPv6 only |
Dual Stack (IPv6 and IPv4) or IPv6 only |
IPv6 |
IPv4 |
IPv4-in-IPv6 |
IPv4 resource on IPv6 PSAM session. |
|
Dual Stack or IPv4 only |
Dual Stack (IPv6 and IPv4) or IPv6 only |
IPv4 |
Dual Stack or IPv4 |
IPv6-in-IPv4 |
IPv6 resource on IPv4 PSAM session. |
Pulse Client 9.0R1 Pulse SAM connection fails with Pulse Connect Secure 9.1R1 version. For more details, refer to 9.1R1 Pulse Secure Desktop Client Release Notes document on the Pulse Secure website (www.pulsesecure.net).
Location Awareness
The location awareness feature enables you to define connections that are activated automatically based on the location of the endpoint. Pulse Client determines the location of the endpoint by evaluating rules that you define. For example, you can define rules to enable Pulse Client to automatically establish a secure tunnel to the corporate network through Pulse Connect Secure when the user is at home, and to establish a Pulse Policy Secure connection when the user is in the office and connected to the corporate network over the LAN. Pulse Client does not re-establish a VPN tunnel when the endpoint re-enters the trusted/corporate network. Location awareness rules are based on the client's IP address and network interface information.
Centralized Pulse Client Configuration Management
Centralized configuration management is a key feature of Pulse Client. Pulse Client connection sets (the configurations that define how and when a Pulse Client connects), are bound to a particular Pulse Secure server. The binding server is the one that provides the initial configuration to the Pulse Client. For example, if you create a Pulse Client connection set on Server A, and then distribute those connections to endpoints, those clients are bound to Server A.
A bound client is managed by its particular Pulse Secure server. The Pulse Secure administrator defines Pulse Client connections and software components that are installed on the endpoint. When Pulse Client connects to the Pulse Secure server that is managing it, the server automatically provisions configuration and software component updates. The administrator can permit the user to add, remove, and modify connections. The administrator can also allow dynamic connections (connections that are added by Pulse Secure servers when the user logs into the server using a browser). A dynamic connection enables a bound client to add connections from Pulse Secure servers other than the one the client is bound to. Dynamic connections are created as manual rather than automatic connections, which means that they are run only when the user initiates the connection or the user browses to a Pulse Secure server and launches Pulse Client from the server's Web interface. Dynamic connections create the connection with the minimum configuration required to make the connection, which means that the URL used to install or launch Pulse Client from the Pulse Secure server's Web interface is used as the Connection URL and connection name. Binding Pulse Clients to a particular server ensures that the client does not receive different configurations when it accesses other Pulse Secure servers. A bound endpoint receives connection set options and connections from its binding server, but it can have its Pulse Client software upgraded from any Pulse Secure server that has the automatic upgrade option enabled. (SRX gateways do not support Pulse Client software updates.)
Pulse Client can be bound to only one Pulse Secure server connection set at a time. Pulse Client can receive updates and changes to that bound connection set from other Pulse Secure servers only if the connection set is exported from the Pulse Secure server and then imported to another Pulse Secure server.
Pulse Client does not need to be bound to a Pulse Secure server. An unbound client is managed by its user. If Pulse Client software is installed without any connections, the user must add connections manually. Dynamic connections can be added by visiting the Web portals of Pulse Secure servers. An unbound client does not accept configuration updates from any Pulse Secure server.
Session Migration
If you configure your access environment to support the Pulse Client session migration feature, users can log in once through a Pulse Secure server on the network, and then securely access additional Pulse Secure servers without needing re-authentication. For example, a user can connect from home through Pulse Connect Secure, and then arrive at work and connect through Pulse Policy Secure without having to log in again. Session migration also enables users to access different resources within the network without repeatedly providing credentials. IF-MAP Federation is required to enable session migration for users.
Smart Connections - List of URLs
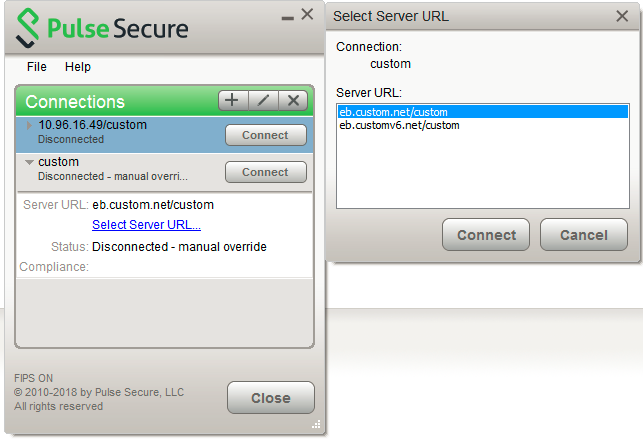
Each Pulse Client connection that connects to Pulse Policy Secure or Pulse Connect Secure can be configured with a list of Pulse Secure servers. Pulse Client attempts to connect to each of the servers in the URL list until it succeeds. You can choose different modes to control the behavior of a Pulse Client connection that is starting from a disconnected state, start at the top of the list, start with the most recently connected URL, or choose randomly. The random option helps distribute the connection load across different Pulse Secure servers. If a Pulse Client connection that is already established gets disconnected, for example, the wireless connection is interrupted, Pulse Client always tries to connect to the most recently connected URL. If that connection fails, Pulse Client uses the server list. The Pulse Client user can also choose a connection from the list as shown in figure.
Security Certificates
Users cannot add CA servers or manage the server list. Pulse Client handles certificates in the same way that a browser handles certificates. If the Pulse Client dynamic certificate trust option is enabled for a connection, the user can accept or reject the certificate that is presented if it is not from a CA that is defined in the endpoint's certificate store.
Compliance and Remediation
Pulse Client supports the Host Checker application to assess endpoint health and update critical software. Host Checker is a client-side agent that is based on Trusted Network Connect standards. You configure rules in Host Checker policies for Pulse Connect Secure and Pulse Policy Secure to specify the minimum criteria for the security compliance of endpoints that are allowed to enter the network. Endpoints that fail can be connected through a remediation role that provides limited access.
Host Checker can be deployed from a Pulse Secure server to Pulse Clients on Windows and macOS endpoints. It will be downloaded and run when a browser is used on a Windows or macOS endpoint to connect to the Pulse Secure server Web portal. You can use Host Checker policies at the realm or role level.
Host Checker is not supported in the use case where the user employs a browser on the mobile device to connect to the Pulse Secure server Web portal.
For Windows and OS X clients, you can use Host Checker to perform the following:
•Virus signature monitoring
You can configure Host Checker to monitor and verify that the virus signatures, operating systems, and software versions installed on client computers are up to date. You can configure automatic remediation for those endpoints that do not meet the specified criteria.
•Patch management information monitoring and patch deployment
You can configure Host Checker policies that check for Windows endpoints' operating system service pack, software version, or desktop application patch version compliance.
•Patch verification remediation options
Pulse Client and Host Checker support endpoint remediation through Microsoft System Management Server or Microsoft System Center Configuration Manager (SMS/SCCM). With SMS/SCCM, Pulse Client triggers a preinstalled SMS/SCCM client to get patches from a pre-configured server.
•Endpoint configuration
You can configure custom rules to allow Host Checker to check for third-party applications, files, process, ports, registry keys, and custom DLLs.
Pulse Mobile Client supports a set of Host Checker functions that vary from one OS to the next. For complete information on Host Checker for mobile clients.
Two Factor Authentication
Pulse Client supports RSA SecurID authentication through soft token, hard token, and smart card authenticators. The SecurID software (RSA client 4.1 and later) must already be installed on the client machine.
Captive Portal Detection
Public WiFi locations often deploy a captive portal that requires the user to enter authentication information or to accept terms of service before network access is granted. Pulse Client detects the presence of captive portals and does not initiate a connection to a Pulse Connect Secure or Policy Secure server until internet access is granted. Pulse Client displays appropriate status information to enable the user to establish the portal and network connections.
Captive portal detection notes:
•Captive portal detection is supported on Pulse Client for both Windows and Mac. Captive portal detection is not supported on Windows In-Box Pulse Client or Pulse Secure Client for Mobile Devices.
•If Pulse Client connects through a proxy in Captive Portal scenario, the captive portal detection algorithm is disabled and Pulse Client tries connecting directly to PCS.
•SRX connections do not support captive portal detection.
Pulse Collaboration Suite Integration
Pulse Collaboration Suite is accessible through the Pulse Client interface on Windows, macOS, and Linux clients. Pulse Collaboration Suite enables users to schedule and attend secure online meetings. In meetings, users can share their desktops and applications with one another over a secure connection. Meeting attendees can collaborate by enabling remote control of their desktops and through text chatting.
Sign In Notifications
The notifications feature on Pulse Connect Secure and Pulse Policy Secure allows the network administrator to display notifications to Pulse Client users prior to the user logging in and after the user has already logged in. For example, you could display a legal statement or a message stating who is allowed to connect to the server before you display the Pulse Client credentials dialog. After the user has connected, you could display a message that notifies the user of scheduled network or server maintenance or of an upcoming company meeting.
Automatic Software Updates
After you deploy Pulse Client software to endpoints, software updates occur automatically. If you upgrade the Pulse Client configuration on the server, updated software components are pushed to a client the next time it connects. You can disable this automatic upgrade feature.
The automatic update feature is supported on Pulse Connect Secure and Pulse Policy Secure servers only. SRX gateways do not support automatic Pulse Client software updates.
If you configure Pulse Client to make 802.1X-based connections, a reboot might be required on Windows endpoints.
Pulse Client Customization and Rebranding
The Pulse Client customization tool (BrandPackager) enables you to customize the appearance of Pulse Client for Windows and Pulse Client for Apple OS X. You can add your own identity graphic to the Pulse Client splash screen, to the program interface, and to Windows credential provider tiles. User Experience shows graphic customizations applied to the Pulse Client for Windows. You can also customize error and informational message text, the text that appears in dialog boxes and on buttons, and make limited changes to Pulse Client online Help. For example, you might want to add your help desk phone number to Pulse Client error messages and the Pulse Client online Help.
BrandPackager is available for download from the Pulse Secure website (www.pulsesecure.net).
