Using a RADIUS Server
This topic describes integration with the RADIUS server.
RADIUS Server Overview
This section describes support for using an external RADIUS server.
Understanding RADIUS Server
A Remote Authentication Dial-In User Service (RADIUS) server is a type of server that allows you to centralize authentication and accounting for users.
The following authentication schemes are supported:
•Access-Request–The user enters the username and password to request access to RADIUS server.
•Access-Accept–The user is authenticated.
•Access-Reject–The user is not authenticated and is prompted to reenter the username and password, or access is denied.
•Access-Challenge–A challenge is issued by the RADIUS server. The challenge collects additional data from the user.
Feature Support
Pulse Secure access management framework supports the following RADIUS features:
•RADIUS attributes that can be used in role mapping.
•RADIUS directory services to retrieve user attributes in role-mapping rules.
•RADIUS accounting to track the services and the network resources used.
•RADIUS proxy to configure your external RADIUS server as an inner or outer proxy target. When you specify RADIUS proxy, some fields in the RADIUS server configuration page are not applicable. This feature is supported only on PPS.
•RADIUS Disconnect messages.
Using Challenge Expressions
The Pulse Secure access management framework supports the RSA Authentication Manager using the RADIUS protocol and a SecurID token (available from Security Dynamics). If you use SecurID to authenticate users, they must supply a user ID and the concatenation of a PIN and a token value.
When you define a RADIUS server, the Pulse Secure access management framework allows administrators to use hard-coded (default) challenge expressions that support Defender 4.0 and some RADIUS server implementations (such as Steel-Belted RADIUS and RSA RADIUS) or to enter custom challenge expressions that allow the system to work with many different RADIUS implementations and new versions of the RADIUS server, such as Defender 5.0. The system looks for the response in the Access-Challenge packet from the server and issues an appropriate Next Token, New PIN, or Generic Passcode challenge to the user.
Using CASQUE Authentication
CASQUE authentication uses a token-based challenge/response authentication mechanism employing a CASQUE player installed on the client system. Once configured with CASQUE authentication, the RADIUS server issues a challenge with a response matching the custom challenge expression (:([0-9a-zA-Z/+=]+):). The system then generates an intermediate page that automatically launches the CASQUE player installed on the user’s system.
PassGo Defender
If you are using a PassGo Defender RADIUS server, the user sign-in process is as follows:
1.The user is prompted for and enters a username and password.
2.The username and encrypted password are sent over the network to the RADIUS server.
3.The RADIUS server sends a unique challenge string to the system. The system displays this challenge string to the user.
4.The user enters the challenge string in a Defender token and the token generates a response string.
5.The user enters the response string on the system and clicks Sign In.
Using RADIUS Attributes
Table describes the RADIUS attributes that are supported in RADIUS role-mapping.
|
Attribute |
Description |
|
ARAP-Challenge-Response |
Contains the response to the challenge of a dial-in client. Sent in an Access-Accept packet with Framed-Protocol of ARAP. |
|
ARAP-Features |
Includes password information that the network access server (NAS) must send to the user in an ARAP feature flags packet. Sent in an Access-Accept packet with Framed- Protocol of ARAP. |
|
ARAP-Password |
Appears in an Access-Request packet containing a Framed-Protocol of ARAP. Only one of User-Password, CHAP-Password, or ARAP-Password must be included in an Access-Request, or one or more EAP-Messages. |
|
ARAP-Security |
Identifies the ARAP security module to be used in an Access-Challenge packet. |
|
ARAP-Security-Data |
Contains the actual security module challenge or response, and is in Access-Challenge and Access-Request packets. |
|
ARAP-Zone-Access |
Indicates how to use the ARAP zone list for the user. |
|
Access-Accept |
Provides specific configuration information necessary to begin delivery of service to the user. |
|
Access-Challenge |
Sends the user a challenge requiring a response, and the RADIUS server must respond to the Access-Request by transmitting a packet with the Code field set to 11 (Access-Challenge). |
|
Access-Reject |
Transmits a packet with the Code field set to 3 (Access-Reject) if any value of the received Attributes is not acceptable. |
|
Access-Request |
Conveys information specifying user access to a specific NAS, and any special services requested for that user. |
|
Accounting-Request |
Conveys information used to provide accounting for a service provided to a user. |
|
Accounting-Response |
Acknowledges that the Accounting-Request has been received and recorded successfully. |
|
Acct-Authentic |
Indicates how the user was authenticated, whether by RADIUS, the NAS itself, or another remote authentication protocol. |
|
Acct-Delay-Time |
Indicates how many seconds the client has been trying to send this record. |
|
Acct-Input-Gigawords |
Indicates how many times the Acct-Input-Octets counter has wrapped around 2^32 over the course of this service being provided. |
|
Acct-Input-Octets |
Indicates how many octets have been received from the port during the current session. |
|
Acct-Input-Packets |
Indicates how many packets have been received from the port during the session provided to a Framed User. |
|
Acct-Interim-Interval |
Indicates the number of seconds between each interim update in seconds for this specific session. |
|
Acct-Link-Count |
Indicates the count of links known to have been in each multilink session at the time the accounting record is generated. |
|
Acct-Multi-Session-Id |
Indicates a unique Accounting ID to make it easy to link together multiple related sessions in a log file. |
|
Acct-Output-Gigawords |
Indicates how many times the Acct-Output-Octets counter has wrapped around 2^32 during the current session. |
|
Acct-Output-Octets |
Indicates how many octets have been sent to the port during this session. |
|
Acct-Output-Packets |
Indicates how many packets have been sent to the port during this session to a Framed User. |
|
Acct-Session-Id |
Indicates a unique Accounting ID to make it easy to match start and stop records in a log file. |
|
Acct-Session-Time |
Indicates how many seconds the user has received service. |
|
Acct-Status-Type |
Indicates whether this Accounting-Request marks the beginning of the user service (Start) or the end (Stop). |
|
Acct-Terminate-Cause |
Indicates how the session was terminated. |
|
Acct-Tunnel-Connection |
Indicates the identifier assigned to the tunnel session. |
|
Acct-Tunnel-Packets-Lost |
Indicates the number of packets lost on a given link. |
|
CHAP-Challenge |
Contains the Challenge Handshake Authentication Protocol (CHAP) challenge sent by the NAS to a PPP CHAP user. |
|
CHAP-Password |
Indicates the response value provided by a PPP CHAP user in response to the challenge. |
|
Callback-Id |
Indicates the name of a location to be called, to be interpreted by the NAS. |
|
Callback-Number |
The dialing string to be used for callback. |
|
Called-Station-Id |
Allows the NAS to send the phone number that the user called, using Dialed Number Identification Service (DNIS) or similar technology. |
|
Calling-Station-Id |
Allows the NAS to send the phone number that the call came from, using Automatic Number Identification (ANI) or similar technology. |
|
Class |
Sent by the server to the client in an Access-Accept and then sent unmodified by the client to the accounting server as part of the Accounting-Request packet, if accounting is supported. |
|
Configuration-Token |
Used in large distributed authentication networks based on proxy. |
|
Connect-Info |
Sent from the NAS to indicate the nature of the user's connection. |
|
EAP-Message |
Encapsulates Extended Access Protocol [3] packets to allow the NAS to authenticate dial-in users by means of EAP without having to understand the EAP protocol. |
|
Event-Timestamp |
Records the time that this event occurred on the NAS, in seconds since January 1, 1970 00:00 UTC. |
|
Egress -VLAN-ID |
The Egress-VLANID attribute represents an allowed Egress VLANID for this port, indicating if the VLANID is allowed for tagged or untagged frames as well as the VLANID. |
|
Egress-VLAN-Name |
The Egress-VLAN-Name attribute represents an allowed VLAN for this port. It is similar to the Egress-VLANID attribute, except that the VLAN-ID itself is not specified or known; rather, the VLAN name is used to identify the VLAN within the system. |
|
Filter-Id |
Indicates the name of the filter list for this user. |
|
Framed-AppleTalk-Link |
Indicates the AppleTalk network number used for the serial link to the user, which is another AppleTalk router. |
|
Framed-AppleTalk-Network |
Indicates the AppleTalk Network number which the NAS can probe to allocate an AppleTalk node for the user. |
|
Framed-AppleTalk-Zone |
Indicates the AppleTalk Default Zone to be used for this user. |
|
Framed-Compression |
Indicates the compression protocol to be used for the link. |
|
Framed-IP-Address |
Indicates the address to be configured for the user. |
|
Framed-IP-Netmask |
Indicates the IP netmask to be configured for the user when the user is a router to a network. |
|
Framed-IPv6-Pool |
Contains the name of an assigned pool used to assign an IPv6 prefix for the user. |
|
Framed-IPv6-Prefix |
Indicates an IPv6 prefix (and corresponding route) to be configured for the user. |
|
Framed-IPv6-Route |
Indicates the routing information to be configured for the user on the NAS. |
|
Framed-IPv6 Address |
Indicates an IPv6 address assigned to NAS interface of the host. |
|
Framed-Interface-Id |
Indicates the IPv6 interface identifier to be configured for the user. |
|
Framed-IPX-Network |
Indicates the IPX Network number to be configured for the user. |
|
Framed-MTU |
Indicates the maximum transmission unit to be configured for the user, when it is not negotiated by some other means (such as PPP). |
|
Framed-Pool |
Indicates the name of an assigned address pool used to assign an address for the user. |
|
Framed-Protocol |
Indicates the framing to be used for framed access. |
|
Framed-Route |
Indicates the routing information to be configured for the user on the NAS. |
|
Framed-Routing |
Indicates the routing method for the user, when the user is a router to a network. |
|
Idle-Timeout |
Sets the maximum number of consecutive seconds of idle connection allowed to the user before termination of the session or prompt. |
|
Ingress-Filters |
The Ingress-Filters attribute corresponds to the Ingress Filter per-port variable. Supports the following values: Disabled=2 Enabled= 1 When the attribute has the value "Enabled", the set of VLANs that are allowed to ingress a port must match the set of VLANs that are allowed to egress a port. |
|
Keep-Alives |
Uses SNMP instead of keepalives. |
|
Login-IP-Host |
Indicates the system with which to connect the user when the Login-Service Attribute is included. |
|
Login-IPv6-Host |
Indicates the system with which to connect the user when the Login-Service Attribute is included. |
|
Login-LAT-Group |
Contains a string identifying the LAT group codes that this user is authorized to use. |
|
Login-LAT-Node |
Indicates the node with which the user is to be automatically connected by LAT. |
|
Login-LAT-Port |
Indicates the port with which the user is to be connected by LAT. |
|
Login-LAT-Service |
Indicates the system with which the user is to be connected by LAT. |
|
Login-Service |
Indicates the service to use to connect the user to the log in host. |
|
Login-TCP-Port |
Indicates the TCP port with which the user is to be connected when the Login-Service Attribute is also present. |
|
MS-ARAP-Challenge |
Only present in an Access-Request packet containing a Framed-Protocol Attribute with the value 3 (ARAP). |
|
MS-ARAP-Password-Change-Reason |
Indicates the reason for a server-initiated password change. |
|
MS-Acct-Auth-Type |
Represents the method used to authenticate the dial-up user. |
|
MS-Acct-EAP-Type |
Represents the Extensible Authentication Protocol (EAP) type used to authenticate the dial-up user. |
|
MS-BAP-Usage |
Describes whether the use of BAP is allowed, disallowed, or required on new multilink calls. |
|
MS-CHAP-CPW-1 |
Allows the user to change password if it has expired. |
|
MS-CHAP-CPW-2 |
Allows the user to change password if it has expired. |
|
MS-CHAP-Challenge |
Contains the challenge sent by a NAS to a MS-CHAP user. |
|
MS-CHAP-Domain |
Indicates the Windows NT domain in which the user was authenticated. |
|
MS-CHAP-Error |
Contains error data related to the preceding MS-CHAP exchange. |
|
MS-CHAP-LM-Enc-PW |
Contains the new Windows NT password encrypted with the old LAN Manager password hash. |
|
MS-CHAP-MPPE-Keys |
Contains two session keys for use by the Microsoft Point-to-Point Encryption (MPPE). |
|
MS-CHAP-NT-Enc-PW |
Contains the new Windows NT password encrypted with the old Windows NT password hash. |
|
MS-CHAP-Response |
Contains the response value provided by a PPP MS-CHAP user in response to the challenge. |
|
MS-CHAP2-CPW |
Allows the user to change password if it has expired. |
|
MS-CHAP2-Response |
Contains the response value provided by an MS- CHAP-V2 peer in response to the challenge. |
|
MS-CHAP2-Success |
Contains a 42-octet authenticator response string. |
|
MS-Filter |
Transmits traffic filters. |
|
MS-Link-Drop-Time-Limit |
Indicates the length of time (in seconds) that a link must be underutilized before it is dropped. |
|
MS-Link-Utilization-Threshold |
Represents the percentage of available bandwidth utilization below which the link must fall before the link is eligible for termination. |
|
MS-MPPE-Encryption-Policy |
Signifies whether the use of encryption is allowed or required. |
|
MS-MPPE-Encryption-Types |
Signifies the types of encryption available for use with MPPE. |
|
MS-MPPE-Recv-Key |
Contains a session key for use by the MPPE. |
|
MS-MPPE-Send-Key |
Contains a session key for use by the MPPE. |
|
MS-New-ARAP-Password |
Transmits the new ARAP password during an ARAP password change operation. |
|
MS-Old-ARAP-Password |
Transmits the old ARAP password during an ARAP password change operation. |
|
MS-Primary-DNS-Server |
Indicates the address of the primary domain name server (DNS) server to be used by the PPP peer. |
|
MS-Primary-NBNS-Server |
Indicates the address of the primary NetBIOS name server (NBNS) server to be used by the PPP peer. |
|
MS-RAS-Vendor |
Indicates the manufacturer of the RADIUS client machine. |
|
MS-RAS-Version |
Indicates the version of the RADIUS client software. |
|
MS-Secondary-DNS-Server |
Indicates the address of the secondary DNS server to be used by the PPP peer. |
|
MS-Secondary-NBNS-Server |
Indicates the address of the secondary DNS server to be used by the PPP peer. |
|
Message-Authenticator |
Signs Access-Requests to prevent spoofing Access-Requests using CHAP, ARAP, or EAP authentication methods. |
|
NAS-IP-Address |
Indicates the identifying IP address of the NAS that is requesting authentication of the user, and must be unique to the NAS within the scope of the RADIUS server. |
|
NAS-IPv6-Address |
Indicates the identifying IPv6 Address of the NAS that is requesting authentication of the user, and must be unique to the NAS within the scope of the RADIUS server. |
|
NAS-Identifier |
Contains a string identifying the NAS originating the Access-Request. |
|
NAS-Port |
Indicates the physical port number of the NAS that is authenticating the user. |
|
NAS-Port-Id |
Contains a text string that identifies the port of the NAS that is authenticating the user. |
|
NAS-Port-Type |
Indicates the type of the physical port of the NAS that is authenticating the user. |
|
Password-Retry |
Indicates how many authentication attempts a user is allowed to attempt before being disconnected. |
|
Port-Limit |
Sets the maximum number of ports to be provided to the user by the NAS. |
|
Prompt |
Indicates to the NAS whether it should echo the user's response as it is entered, or not echo it. |
|
Proxy-State |
Indicates that a proxy server can send this attribute to another server when forwarding an Access-Request. The attribute must be returned unmodified in the Access-Accept, Access-Reject or Access-Challenge. |
|
Reply-Message |
Indicates that the text that can be displayed to the user. |
|
Service-Type |
Indicates the type of service the user has requested, or the type of service to be provided. |
|
Session-Timeout |
Sets the maximum number of seconds of service to be provided to the user before termination of the session or prompt. |
|
State |
Indicates that the packet must have only zero or one State Attribute. Usage of the State Attribute is implementation dependent. |
|
Telephone-number |
Using the Calling-Station-Id and Called-Station-Id RADIUS attributes, authorization and subsequent tunnel attributes can be based on the phone number originating the call, or the number being called. |
|
Termination-Action |
Indicates the action the NAS should take when the specified service is completed. |
|
Tunnel-Assignment-ID |
Indicates to the tunnel initiator the particular tunnel to which a session is to be assigned. |
|
Tunnel-Client-Auth-ID |
Specifies the name used by the tunnel initiator during the authentication phase of tunnel establishment. |
|
Tunnel-Client-Endpoint |
Contains the address of the initiator end of the tunnel. |
|
Tunnel-Link-Reject |
Indicates the rejection of the establishment of a new link in an existing tunnel. |
|
Tunnel-Link-Start |
Marks the creation of a tunnel link. |
|
Tunnel-Link-Stop |
Marks the destruction of a tunnel link. |
|
Tunnel-Medium-Type |
Indicates the transport medium to use when creating a tunnel for those protocols (such as L2TP) that can operate over multiple transports. |
|
Tunnel-Medium-Type |
Indicates the transport medium to use when creating a tunnel for those protocols (such as L2TP) that can operate over multiple transports. |
|
Tunnel-Password |
Specifies a password used to access a remote server. |
|
Tunnel-Preference |
Indicates that if RADIUS server returns more than one set of tunneling attributes to the tunnel initiator, you should include this attribute in each set to indicate the relative preference assigned to each tunnel. |
|
Tunnel-Private-Group-ID |
Indicates the group ID for a particular tunneled session. |
|
Tunnel-Reject |
Marks the rejection of the establishment of a tunnel with another node. |
|
Tunnel-Server-Auth-ID |
Specifies the name used by the tunnel terminator during the authentication phase of tunnel establishment. |
|
Tunnel-Server-Endpoint |
Indicates the address of the server end of the tunnel. |
|
Tunnel-Start |
Marks the establishment of a tunnel with another node. |
|
Tunnel-Stop |
Marks the destruction of a tunnel to or from another node. |
|
Tunnel-Type |
Indicates the tunneling protocol(s) to be used (in the case of a tunnel initiator) or the tunneling protocol in use (in the case of a tunnel terminator). |
|
User-Name |
Indicates the name of the user to be authenticated. |
|
User-Password |
Indicates the password of the user to be authenticated, or the user's input following an Access-Challenge. |
Understanding RADIUS Accounting
You can configure the device to send session start and stop messages to a RADIUS accounting server. The device sends a user-session start message after the user successfully signs in and the device maps to a role.
Whenever a user session is terminated, the device sends a user-session stop message to the accounting server. A user session is terminated whenever the user:
•Manually signs out
•Times out because of either inactivity or exceeding the maximum session length
•Is denied access because of Host Checker role-level restrictions
•Is manually forced out by an administrator as a result of dynamic policy evaluation
If users are signed into a device cluster, the RADIUS accounting messages might show the users signing in to one node and signing out of another.
Table describes the attributes that are common to start and stop messages.
|
Attribute |
Description |
|
User-Name (1) |
Specifies the string that the device administrator specifies during RADIUS server configuration. |
|
NAS-IP-Address (4) |
Specifies the device’s IP address. |
|
NAS-Port (5) |
The device sets this attribute to 0 if the user signed in using an internal port, or 1 if an external port is used. |
|
Framed-IP-Address (8) |
Specifies the user’s source IP address. |
|
NAS-Identifier (32) |
Specifies the configured name for the device client under the RADIUS server configuration. |
|
Acct-Status-Type (40) |
The device sets this attribute to 1 for a start message, or 2 for a stop message in a user-session or a subsession. |
|
Acct-Session-Id (44) |
Specifies the unique accounting ID that matches start and stop messages corresponding to a user-session or to a subsession. |
|
Acct-Multi-Session-Id (50) |
Specifies the unique accounting ID that you can use to link together multiple related sessions. Each linked session must have a unique Acct-Session-Id and the same Acct-Multi-Session-Id. |
|
Acct-Link-Count (51) |
Specifies the count of links in a multilink session at the time the system generates the accounting record. |
|
Attribute |
Description |
|
Acct-Authentic (45) |
The device sets this attribute to: •RADIUS—if the user is authenticated to a RADIUS server. •Local—if the user is authenticated to a local authentication server. •Remote—if the user is authenticated through any other RADIUS server. |
|
Attribute |
Description |
|
Acct-Session-Time (46) |
Specifies the duration of the user-session or the subsession. |
|
Acct-Terminate-Cause (49) |
The device uses one of the following values to specify the event that caused the termination of a user session or a subsession: •User Request (1) – User manually signs out. •Idle Timeout (4) – User is Idle and times out. •Session Timeout (5) – User’s maximum session times out. •Admin Reset (6) – User is forced out from active user’s page. |
Interoperability Requirements and Limitations
You must configure the third-party RADIUS server to communicate with the Pulse Secure access management framework.
On the RADIUS server, configure the following settings:
•Hostname.
•Network IP address.
•Client type, if applicable. If this option is available, select Single Transaction Server or its equivalent.
•Type of encryption for authenticating client communication. This choice should correspond to the client type.
•Shared secret.
The following are the requirements and limitations for Interim update feature:
•If you want a server to receive interim accounting messages, you can statically configure an interim value on the client, in which case, the locally configured value overrides any value that might be included in the RADIUS Access-Accept message.
•The octet count reported in the accounting messages is the cumulative total since the beginning of the user session.
•The interim update byte count is only supported based on a user session, not on SAM or NC sessions.
Configuring Authentication with a RADIUS Server
To configure authentication with the RADIUS server:
1.Select Authentication > Auth. Servers.
2.Select RADIUS Server and click New Server to display the configuration page.
3.Complete the configuration as described below.
4.Save the configuration.
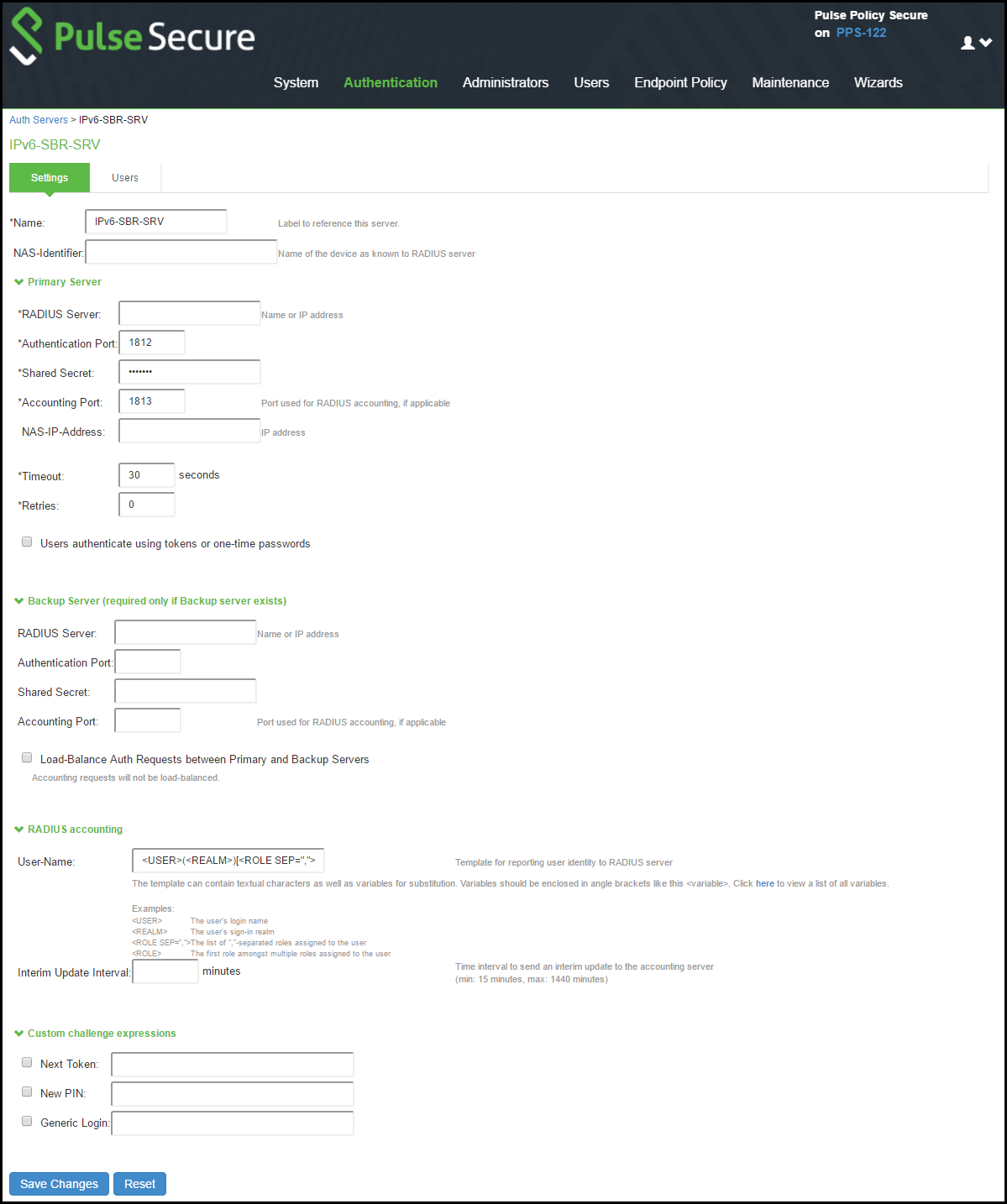
|
Settings |
Guidelines |
|
Name |
Specify a name to identify the server within the system. |
|
NAS-Identifier |
Specify the name that identifies the Network Access Server (NAS) client to the RADIUS server. - If you do not specify the NAS identifier, the value specified in the Hostname field on the System > Network > Overview page of the administrator console is used. |
|
Primary Server |
|
|
Radius Server |
Specify the name or IPv4/IPv6 address of the RADIUS server. |
|
Authentication Port |
Specify the authentication port value for the RADIUS server. Default port number: 1812, 1645 (legacy servers) |
|
NAS-IP-Address |
Specify the NAS IP address. - If you leave this field empty, the internal IP address is passed to RADIUS requests. |
|
Timeout (seconds) |
Specify the interval of time to wait for a response from the RADIUS server before timing out the connection. |
|
Retries |
Specify the number of times to try to make a connection after the first attempt fails. |
|
Users authenticate using tokens or one-time passwords. |
Select this option to prompt the user for a token instead of a password. For example, you can use this option to dynamically prompt for a password or token based on sign-in policies by configuring two instances of the same authentication server. You can use one instance for wireless users with this option enabled and that prompts the user for a token, and another instance for wired users with this option disabled and that prompts the user for a password. If you are using RADIUS proxy feature, this option is not used. |
|
Backup Server (required only if Backup server exists) |
|
|
Radius Server |
Specify the secondary RADIUS server. The authentication request is first routed to the primary RADIUS server, then to the specified backup server if the primary server is unreachable. Accounting messages are sent to the RADIUS server by each cluster node without consolidation. RADIUS accounting follows these assumptions: •If the cluster is active/passive, all users are connected to one node at a time. •If the cluster is active/active and does not use a balancer, users are connected to different nodes but are static. •If the cluster is active/active and uses a balancer, the balancer usually enforces a persistent source IP. In this case, users are always connected to the same node. RADIUS does not support load balancing. |
|
Authentication Port |
Specify the authentication port. |
|
Shared Secret |
Specify the shared secret. |
|
Accounting Port |
Specify the accounting port. |
|
Radius Accounting |
|
|
User-Name |
Specify the user information to the RADIUS accounting server. You can enter any of the applicable session variables. Applicable variables include those that are set the time after the user signs in and maps to a role. The default variables for this field are as follows: •USER: Logs the username to the accounting server. •REALM: Logs the realm to the accounting server. •ROLE SEP=”,”: Logs the list of comma-separated roles assigned to the user. •ROLE: Logs the role to the accounting server. If you assign the user to more than one role, the system separates them with commas. |
|
Interim Update Interval (minutes) |
Select this option to achieve more precise billing for long-lived session clients and during network failure. - If you are using the RADIUS proxy feature, the fields in this section are not used. |
|
Custom challenge expressions |
|
|
(Optional) Three types of challenge expressions exist with each automatically set to its pre-populated default. The custom option allows the administrator to configure the actual string pattern to match for any of the three modes. To add a custom expression, select the check box for the appropriate challenge expression type, and add a custom expression in the associated text box. - If you use SecureID to authenticate users, then provide the user ID and the concatenation of PIN and the token value. |
|
|
Next Token |
Specify the appropriate Next Token. |
|
New PIN |
Specify the New PIN. |
|
Generic Login |
Specify the Generic Login challenge to the user. |