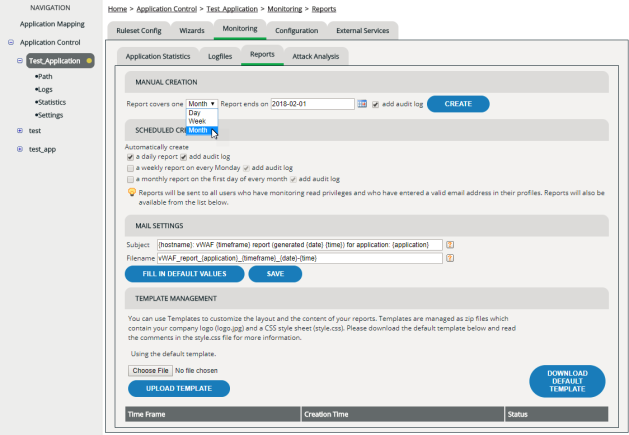
Reports
Purpose
Reports provide a printable summary of the current configuration and of the most recent events in PDF format.
You can use reports, for example, if you require printed documentation of your protective measures, or if you need to present to other people what has recently happened and been configured. Also vWAF can send you daily, weekly or monthly reports by email, which keep you informed at regular time intervals about the most important developments.
Each report covers one specific application. Therefore, if you manage more than one application in vWAF, you need to create a separate report for each one.
Creating and downloading a report manually
To create a report:
Scheduling reports sent by email
You can configure vWAF so that it sends reports automatically by email at regular time intervals.
Reports are sent to all users who have read access for monitoring the application. Make sure that valid email addresses have been entered for all users who are to receive reports.
To schedule automatic reports:
- In the navigation area, select the application for which you want to create the reports.
- Activate the Monitoring | Reports tab.
- In the section
Scheduled Creation, select the desired time frames:
- daily: A report is created and emailed once a day, at 0:00 a.m.
- weekly: A report is created and emailed once a week, Monday morning at 0:00 a.m.
- monthly: A report is created and emailed once a month, first day of month at 0:00 a.m.
- By default, reports contain an Audit Log relating to the time-frame of the report. If you want a brief report without the Audit Log, clear the corresponding add auditlog check box. On the Status Display the message report creation schedule changed appears.
Contents of a report
A report always relates to one specific application. It comprises:
- basic configuration parameters:
version of the detection ruleset, version of the protection ruleset, list of application administrators;
in weekly and monthly reports also: complete list of all ruleset definitions
- a list of the hosts of the application
- a consolidated log file analysis for each host of the application, listing:
- denied requests by IP, denied requests by URI
- requests by handler name, requests by IP
- requests by URI
(only lists the 10 most frequently affected IPs, URIs, and handlers; for a full analysis, you need to analyze your log files manually (see Log Files)
- statistics, relating to the time-frame of the report (see Application Statistics)
- optional: an Audit Log, relating to the time-frame of the report (see Audit Log)