Vulnerability Management
Purpose
A source code analyzing tool or an online web application scanner can check your web application for possible vulnerabilities such as Cross-Site-Scripting (XSS) and SQL Injection. However, it then takes some time to implement a fix and to test the fixed web application before you put it back online.
Vulnerability Management helps you to bridge this gap. It automatically reads the report of the analyzing tool and creates a set of blacklist rules based on the vulnerable entry points and variables listed in the report. This provides instant protection for a vulnerable web application.
ATTENTION
Vulnerability Management wasn’t designed to guarantee long-time protection of vulnerable applications. If analysis revealed attack vectors, fix these problems as soon as possible. Use Vulnerability Management only for interim protection.
Currently, the following application scanners are supported:
- CodeProfiler from Virtual Forge GmbH (http://virtualforge.com).
- CodeSecure from Armorize Technologies, Inc. (http://www.armorize.com).
- IBM AppScan from IBM Corporation (http://www.ibm.com).
- Sentinel from WhiteHat Security, Inc. (https://www.whitehatsec.com).
Opening
To access Vulnerability Management:
Importing reports
You can import reports from either online web application scanners or offline web application scanners:
- If your web application scanner provides you with a report file, you need to upload this file to vWAF.
- If your web application scanner provides you with a username and password to download report files, you can either download these files manually and then upload them to vWAF, or you can download them directly to vWAF.
Downloads and uploads must always be triggered manually. They aren’t repeated automatically at regular intervals.
Both uploads and downloads are carried out on the Import tab.
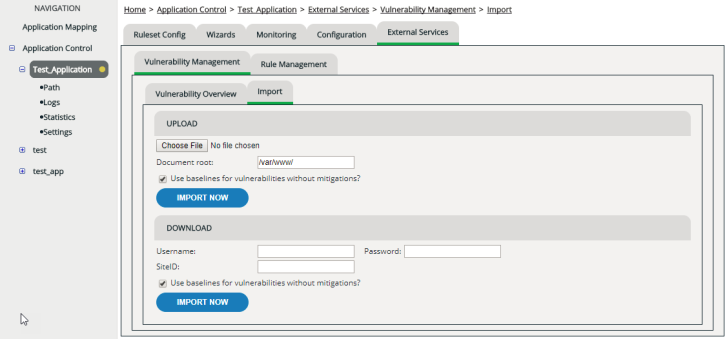
Uploading a report
To upload a report file to vWAF:
Downloading a report
To download a report from your web application scanning service provider directly to vWAF.
When you now return to the Vulnerability Overview tab, you see a listing of all vulnerabilities that were identified by the imported reports.
Important: You must click the Commit button on the bottom of the Vulnerability Overview page in order for the listed mitigation rules to become effective.
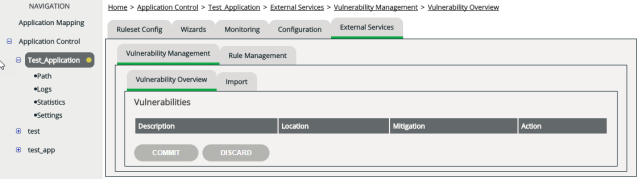
Vulnerability Overview
After you’ve imported a report, the Vulnerability Overview tab lists all vulnerabilities that have been identified by the report.
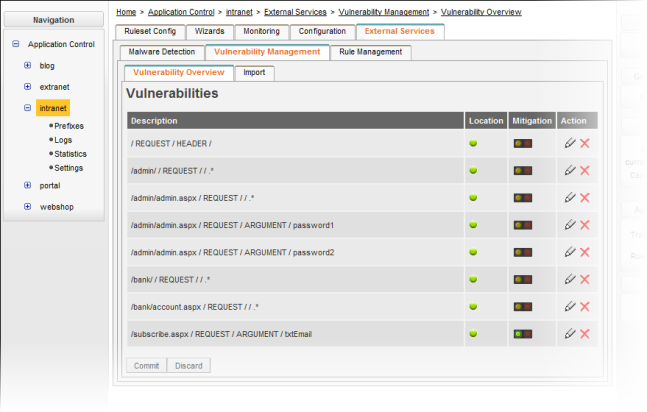
A green traffic light symbol in the Location column indicates that the location of the vulnerability could be clearly identified. If the traffic light symbol in the Location column is red, you need to edit the location manually. To do so, click the corresponding Edit icon in the Action column.
The traffic light symbols in the Mitigation column indicate whether or not your web application is currently protected against attacks that exploit the vulnerability:
- red: Mitigation is disabled.
- yellow (flashing): Mitigation is enabled, but there are no mitigation rules. Edit the vulnerability or disable mitigation by clicking the red traffic light symbol.
- green: Mitigation is enabled and running.
You can click the traffic light symbols to toggle the status.
If you don’t want to take care of a detected vulnerability — for example, because you’re absolutely sure that it is a false positive — you can click the Delete icon in the Action column to remove the vulnerability from the list.
ATTENTION
If you remove a vulnerability from the list, this also turns off and deletes all mitigation rules that are active to protect your web application from attacks that exploit this vulnerability.
ATTENTION
You must click the
Commit button on the bottom of the
Vulnerability Overview page in order for the listed mitigation rules to become effective.
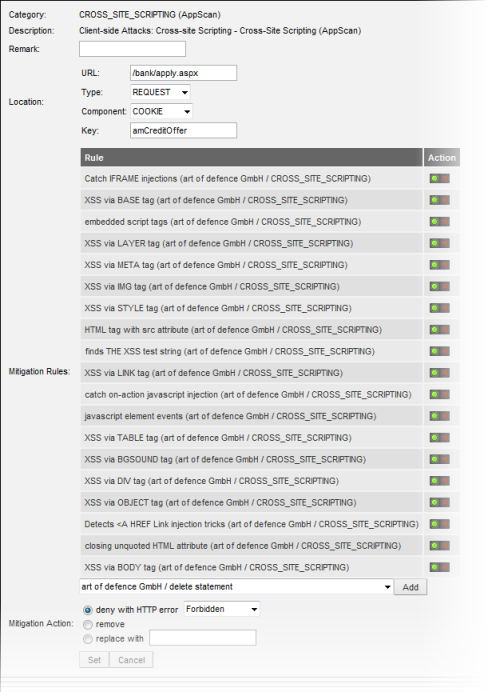
Editing a vulnerability
If necessary, you can specify the location of a detected vulnerability more closely, and you can edit which mitigation rules vWAF uses to protect your web application from attacks that exploit the vulnerability.
You must click the Commit button on the bottom of the Vulnerability Overview page in order for the listed mitigation rules to become effective.