Configuring Kerberos-Based Authentication
Kerberos-based authentication is supported on iOS devices at v7.0 or later.
Kerberos-based authentication is configured by the administrator using the Single Sign On workspace properties for a policy, see Single Sign On.
To configure Kerberos-based authentication:
1.Log in to Pulse One admin console.
2.Select the Workspaces menu, and then select Policies.
3.Create a new policy (if required), see Creating a Policy.
4.Select the required policy.
5.Select the Properties tab.
6.Expand the Single Sign On category and configure the following properties:
•Account Name – The name for the account.
•Authentication Realm – The Kerberos realm name. This value is case sensitive.
•Enabled – Set this to Yes to enable Kerberos authentication.
•Package names allowed to use Kerberos Auth – (Optional) A list of application identifiers that are allowed to use this login. Each line of the property represents a single app. For example:
com.microsoft.outlook
com.google.mail.
If this field not specified, all app identifiers match automatically.
•Principal Name – Set this to the macro string value <USER_USERNAME>.
This macro value is automatically replaced with the user’s name when connecting to a device.
•URL Prefix Matches to use Kerberos Auth – A list of URLs prefixes that must be matched to use this account for Kerberos authentication over HTTP. Each line of this property represents a URL. For example:
http://demo.pwskerb.example1
http://demo.pwskerb.example2
Kerberos authentication for the user will be performed manually once, on the first match of any of the listed URLs. For all subsequent uses of any URL, Kerberos authentication will be performed automatically.
7.Click Publish to push the updated policy to all affected devices.
Any new iOS devices (BYOD or corporate) that use the policy will receive all settings automatically when they are onboarded.
8.(Optional) To confirm the presence of Kerberos authentication on an individual device:
•On the iOS device, access Settings > General > Device Management > Pulse Secure Profile > More Details.
•Under Single Sign On Account, a Kerberos entry will be present. The name of the entry is the Account policy property. For example:
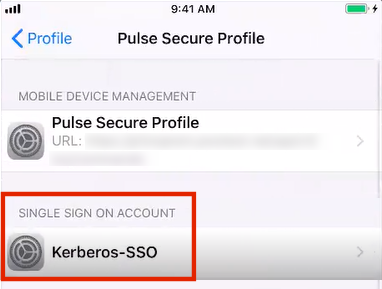
•Tap the Kerberos entry to view its details. For example:
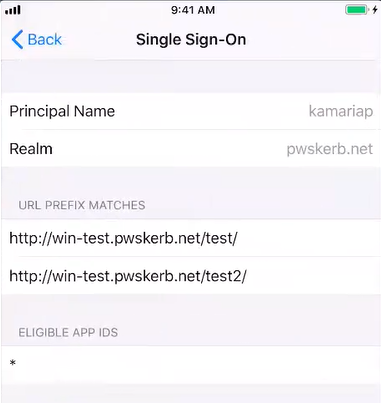
In this example:
•The Principal Name, which has the macro value <USER_USERNAME> in the workspace properties for the policy, is replaced by the specific user name.
•There are two configured URL Prefix Matches.
•There are no configured Eligible App IDs (app identifiers). As a result, a wildcard asterisk (*) setting ensures that all app identifiers match.
•When the user accesses a matching resource for the first time using Kerberos authentication, a Kerberos login page appears. After a valid login is used, the login page will no longer appear for any attempts to access a matching resource.