What's New
This section covers new features, enhancements, improvements or compatibility updates included in Workspace Control 2021.2 (version 10.7.20.0).
User Voice Feature Requests
Thank you for your support and continued submission of Product Enhancement Requests using the Product Ideas page on the Ivanti Community. These requests are reviewed every week and form a valuable input for the Workspace Control product roadmap. Please continue to submit your ideas and vote for your favorites.
The following user requests have been addressed in this version of Workspace Control:
Authorized Owners
Authorized Owners increases the security of your Workspace Control environment by not allowing untrusted software to run. Untrusted software can include malware, video games or unlicensed software.
Authorized Owners is based on NTFS ownership and enables administrators to allow applications to be started only if the configured NTFS owner matches the file owner of the executable. Workspace Control checks executables to ensure that their ownership matches the configured authorized owners. If end-users launch an application and the NTFS file owner of the executable is not found in the list of authorized owners, then Workspace Control blocks the application from starting.
When enabling the Authorized Owners feature, the following authorized owners list is evaluated before Workspace Control allows an application to start:
-
SYSTEM
-
BUILTIN\Administrators
-
%ComputerName%\Administrator
-
NT Service\TrustedInstaller
To enable the Authorized Owners feature, open the Workspace Control Console and navigate to Security > Authorized Owners > Settings tab. Set the Authorized Owners option to Enabled and then select Save Settings from the main menu bar.
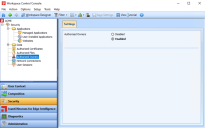
(click the image to enlarge it)
The Authorized Owners feature will be expanded with additional functionality in a future release, including adding and removing owners, adding and editing administrative notes, and configuring Workspace Containers.
More details about this User Voice Feature Request are found on Ivanti Ideas.
Export Security logs as CSV files
The log information found under the Log tab for the following Workspace Control nodes can now be exported as CSV files:
-
Security > Applications > Managed Applications
-
Security > Applications > User Installed Applications
-
Security > Applications > Websites
-
Security > Data > Removable Disks
-
Security > Data > Files and Folders
-
Security > Data > Read-Only Blanketing
-
Security > Authorized Certificates
-
Security > Network Connections
To export the information found under the Log tab as a CSV file, follow these steps:
-
Right-click on any entry and then select Export to file from the context-menu.
-
Select a location where to save the CSV file, enter an appropriate name for the file and then select Save.
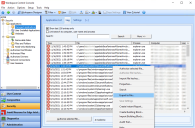
(click the image to enlarge it)
Security logs can also be exported using the pwrtech command-line option:
pwrtech.exe /exportlog /type=<Workspace Control node> /output=<output filepath> [/outputtype=csv] [/start=<start date>] [/end=<end date>]
For example:
pwrtech.exe /exportlog /type=application /output=C:\export\managed_apps.csv /outputtype=csv /start=20161130 /end=20180523
/outputtype, /start and /end are optional parameters. If /outputtype is not specified, then the security logs are exported as XML files instead of CSV files.
For more details on pwrtech.exe /exportlog, see the Workspace Control Administration Guide.
More details about this User Voice Feature Request are found on Ivanti Ideas.
New Enhancements and Improvements
The following enhancements and/or improvements are part of this version of Workspace Control:
Exclude processes from preventing session logoff
In Workspace Control sessions, Citrix published applications are started as separate full-screen sessions without a taskbar. When such applications are closed, Workspace Control also closes the session. To prevent the session from closing while sub-processes started by the application are still running, Workspace Control compares the processes running at session end against the processes running at session start. If Workspace Control finds additional running processes, the session remains opened.
When enabled, the option applies to all Workspace Control managed sessions.
To exclude processes from preventing Workspace Control to close the session, open the Workspace Control Console and then, from the main menu bar, select Setup > Advanced Setup. Select the Exclude processes from blocking the logoff sequence option. Configure the processes to be excluded and then select Save Settings from the main menu bar.
Process names must follow these rules:
-
Be up to 255 characters in length.
-
Contain only alphanumeric characters.
-
End in .exe as the extension.
For example: crss.exe.
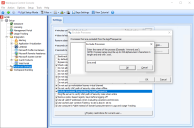
(click the image to enlarge it)
The session now ends even if the excluded processes are still running.
If the ExcludeProcesses registry setting is already configured in your Workspace Control environment, enabling the Exclude processes from blocking the logoff sequence option overrules the registry setting.
Logon Performance
The Logon Performance node displays statistics regarding Workspace Control session logons. If the feature is enabled, Workspace Control Agents send logon information to the Datastore when a Workspace Control managed session is started.
To enable the feature, open the Workspace Control Console and navigate to Diagnostics > Logon Performance > Settings tab. Set the Logon Performance option to Enabled and then select Save Settings from the main menu bar.
Every time a Workspace Control managed session is started and the logon process starts, the following information is visible in the Workspace Control Console, under the Log tab:
-
Boot time — the date and time when the machine was powered on.
-
Windows logon time — the date and time when the user logged onto the Windows operating system and the Windows session started.
-
Session start time — the date and time when the Workspace Control managed session started.
-
Computer — the machine where the Workspace Control managed session started.
-
User name — the user that started the Workspace Control managed session.
-
Logon duration — the duration of the Workspace Control logon process.
-
Desktop session — whether or not the Workspace Control managed session was started on a desktop machine.
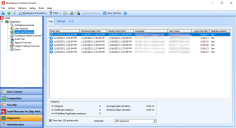
(click the image to enlarge it)
Improved proxy settings detection
The capability of Workspace Control to detect proxy settings has been improved. The improvement applies to activating Workspace Control licenses through a proxy server.