Network Security Modes: disabled, learning, enabled
Network security can be configured on a global level or on individual application level.
Global level
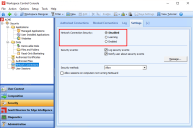
There are three modes for the global settings of the Network Security feature under the Network Connection Security option:
-
In Disabled mode, Network Security allows all network connections, and no data is logged.
-
In Learning mode, Network Security allows all network connections. However, you can choose to log these events. Use learning mode to monitor and evaluate which network connections are used without restricting users in their work.
-
In Enabled mode, Network Security is enforced: authorized network connections are allowed and unauthorized connections are blocked. You can choose to log attempts to access blocked connections.
To configure network security on a global level, open the Workspace Control Console and go to Security > Network Connections > Settings tab and select the desired option for Network Connection Security.
-
If you select the option Log security events, security events will be logged if Network security is in enabled or learning mode.
-
If you select the option Notify users about security events, users will be notified if Network security is in enabled or learning mode.
Application level
If Network Security is enabled or in learning mode, all configured Authorized Connections will be enforced to all applications. If you need to determine which network connections should be authorized for an application, you can run this application's Authorized Connections in learning mode so that it can still access unauthorized network connections, but these are logged.
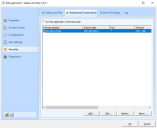
This done from the Workspace Control Console, under Security > Applications > Managed Applications. Open a managed application from the Application List. In the Edit application window navigate to Security > Authorized Connections.
Individual blocked connections
If Network Security is enabled or in learning mode, a new blocked connection is set in learning mode by default. This allows you to monitor the use of this connection, which will be allowed but also logged. If the connection should indeed be blocked, the rule must be set in blocking mode.