File Director
This page refers to an older version of the product.View the current version of the online Help.
OneDrive connector for home map points
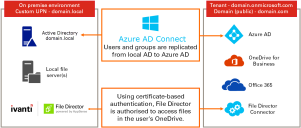
Configure Azure Active Directory (Azure AD) and the File Director admin console to use OneDrive accounts as the storage location for user's home map points. File Director can then utilize the 1TB of storage, included free of charge, with each Office 365 for Business license. Once configured, users can update files on map points using File Director and OneDrive clients. All changes are synchronized with the File Director server so the files are up-to-date, regardless of the client used to edit or view them.
You can use multiple application IDs when connecting to the SharePoint Online API, so each node in a cluster can have its own application ID, which improves the efficiency of the connector.
Prerequisites
- Your perimeter firewall must allow communication to <instancename>-my.sharepoint.com on port 443 and Microsoft supplied URLs detailed in this article.
- You are an Office 365 administrator.
- Your public domain is associated with your Azure AD instance.
- You know your Azure tenant name - typically, this takes the form of: <customer name>.onmicrosoft.com.
-
Password replication is set up on your local AD.
Note that Federated AD access is not supported - the local username UPN must match the one used to sign into Azure. -
Each user’s ‘Personal Site’ (within the SharePoint Admin Portal) should correlate with the user’s UPN – note that in SharePoint special characters are replaced with underscores (_).
Example: Username [email protected] would translate to /personal/john_doe_test_com - Users have an Office 365 license assigned to them from the Office 365 Admin Center.
-
Users have OneDrive storage provisioned.
For further information about how to pre-provision OneDrive for Business for your users, see: https://technet.microsoft.com/en-us/library/dn800987.aspx.
For further reading about integrating applications with Azure AD, see the Microsoft documentation.
Microsoft have published a list of invalid file names and file types for OneDrive. It is available here.
Step 1 - Create your Azure AD application and grant permission to access OneDrive storage
- Login to Azure AD Admin Center as Office 365 Administrator.
-
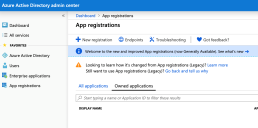
In the sidebar menu click All Services > App Registrations.
-
In the App registrations dashboard, click New registration.
-
Enter an appropriate name for the application, and accept the default supported account types: Accounts in this organizational directory only.
Click Register at the bottom of the dialog. -
An application ID is generated and displayed.
You will need to record the application ID as it is required for the next stage in the setup.
Configure permissions for the appliance
This determines what the application is allowed to do and what it can access.
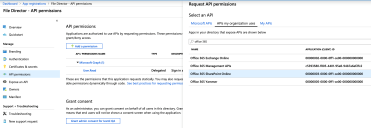
1.Click API Permissions > Add a Permission.
2.In the Request API Permissions dialog, click the APIs my organization uses tab.
Enter office 365 into the search box to find Office 365 SharePoint Online.
3.Click Office 365 SharePoint Online > Application Permissions.
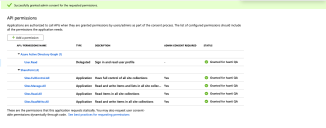
4.In the Request API permissions dialog, select the permissions required then click Add Permissions at the bottom of the dialog.
Note, the illustration shows the minimum permissions required to set up the OneDrive connector.
5.Having added the permissions, you need to provide Administrator consent for them.
In the Grant Consent section, click the button Grant admin consent for...
In the confirmation dialog displayed, click Yes.
This action permits access to OneDrive storage for your named application.
6.Confirmation of your consent is displayed:
Step 2 - Configuring File Director- Version 2019.1 SP1 or later
The next step is to go to the File Director console to generate a certificate that can be used to authenticate with OneDrive. Authentication uses public key infrastructure to generate a self-signed certificate in the server and uploads the public key to Azure.
One Drive Registration
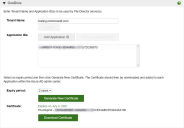
1.In the File Director web admin console, select Configuration > Cloud Connectors.
2.If required, click OneDrive to expand the OneDrive dialog.
3.Enter the Tenant Name - this is the custom domain name configured in Azure AD.
Note, to update the tenant name, enter the name required and click Update. This updates the current configuration, retaining other details configured previously.
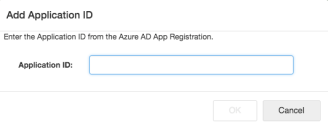
4.Click Add Application ID to display the Add Application ID dialog.
5. Enter the Application ID for the app - this is the application (client) ID you copied from Azure AD and click OK.
A new App must be created in Azure for each Application ID you want to use.
6.Repeat steps 3 and 4 until all app IDs have been added.
7.Select an Expiry period; 1 or 2 years.
8.Click Generate New Certificate.
The certificate is generated and a thumbprint is displayed.
If you have a number of certificates in use, the thumbprint can be a convenient identifier within the Azure portal and helps to ensure the correct certificate is selected.
9.Click Download Certificate.
The public certificate file is downloaded in PEM format. It will be named fdod4b_cert.pem.
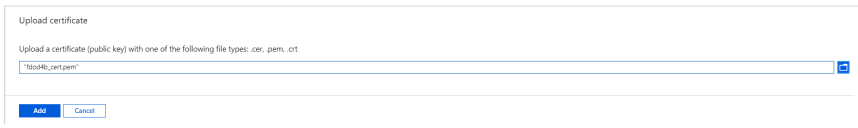
10.In Azure AD, go to click Certificates & secrets in the sidebar menu then click the Upload certificate button.
11.In the Upload certificate dialog, click the folder icon to locate and select the .pem file you created earlier, click Open, then click Add.
12.The thumbprint of the certificate is now listed in your application.
Your cloud connector for OneDrive is complete. You can now create a OneDrive home map point and then assign an access policy for users as required. See Map Point Configuration.
When configured, users access their Home folder, and will save to their OneDrive storage - there is no impact on their File Director user experience.
OneDrive will display files that have been saved to the user's File Director home map point. A folder named _filedirector_ is also created in the root of user's OneDrive storage. This folder stores creation times, modified times, and other metadata.
This uses public key infrastructure to generate a self-signed certificate in the server and upload the public key to Azure as part of a manifest.
Copy the app ID
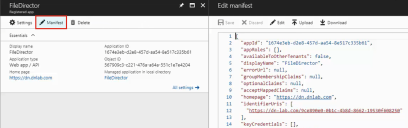
1.Click Manifest for your Azure AD application.
The manifest displays.
2.Copy the app Id from the manifest and save it to Notepad - you need this to generate data for the manifest.
One Drive Registration
- In the File Director web admin console, select Configuration > Cloud Connectors.
- Enter the Tenant Name - this is the custom domain name configured in Azure AD.
- Click Add Application ID to display the Add Application ID dialog.
- Enter the Application ID for the app - this is the app Id you copied from Azure AD and click OK.
A new App must be created in Azure for each Application ID you want to use.
- Repeat steps 3 and 4 until all app Ids have been added.
- Select an Expiry period; 1 or 2 years.
- Click Generate.
The data you need to add to the manifest is generated.
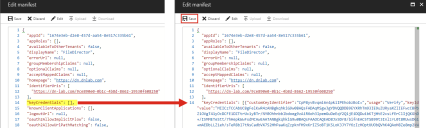
- Click Copy to copy the data to the clipboard. You can save this to a text editor if you are not going to edit the manifest immediately - if you are, just leave it on the clipboard.
In Azure AD, Locate the keyCredentials class in your manifest and paste the data you copied from the File Director web admin console between the square brackets.
- Click Save
You need to configure the AD setting. The local AD is used for authentication but must be in sync with Azure AD. For further information, see Configure the Active Directory connection.