Global policy
Set restrictions on platform, IP address, timeout and login attempts that apply to all your users.
In the Admin console, select Policy > Global and click Edit. When all required changes have been made, click Save.
In this section:
- Client Access
- IP Address Login Restrictions (2020.3 and earlier)
- Failed Login Attempts
- File Sharing (2020.2 and earlier)
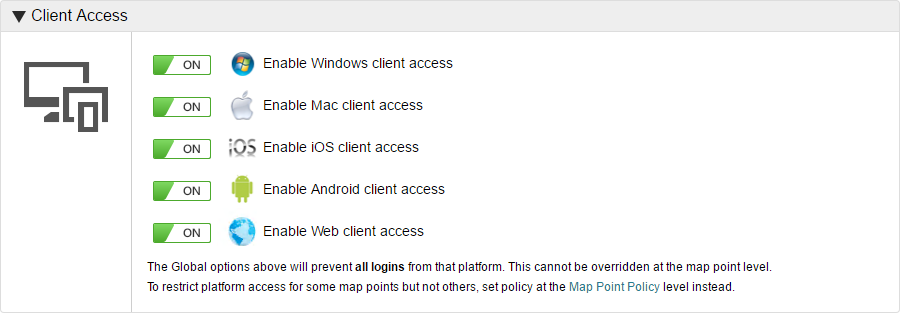
Client access
Specify which platforms can log on to File Director on your server. Click Edit and toggle the policy for each platform to On or Off as required. When complete, click Save.
Platform restrictions can also be set for individually for each Map Point. Global restrictions take precedence over those set at Map Point level - if you disable a platform at the global level, it is disabled for all users regardless of the setting on their Map Point.
The table below illustrates this behavior.
| Platform | Global | Map Point | Effect |
|---|---|---|---|
| Windows | On | On | Users for that Map Point can access the File Director server through Windows. |
| Mac | On | Off | Users for that Map Point cannot access your server on a Mac as the Global setting is overridden. |
| iOS | Off | Off | Users cannot access your server on an iOS device regardless of their Map Point. |
| Android | Off | On | Users cannot access your server on an Android device regardless of their Map Point as the Map Point setting is overridden. |
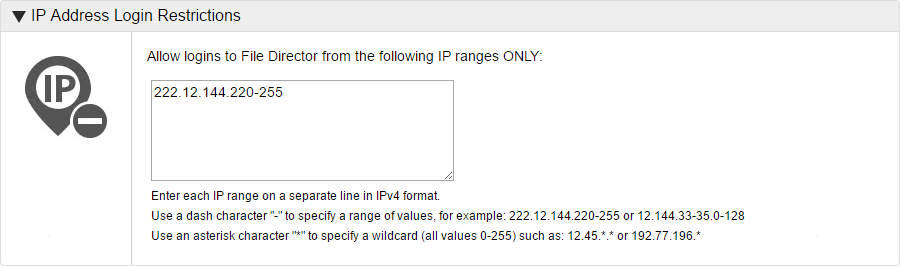
IP address login restrictions (2020.3 and earlier)
The following section applies to File Director 2020.3 and earlier.
Click Edit and specify which IP addresses can access your File Director server using the following formats:
- Enter each IP address on a separate line in IPv4 format.
- Specify a range of values using a dash. For example, 222.12.144.220-255.
- Use an asterisk to specify denote a wildcard - any value between 0 and 255. For example, 222.12.144.*
When complete, click Save.
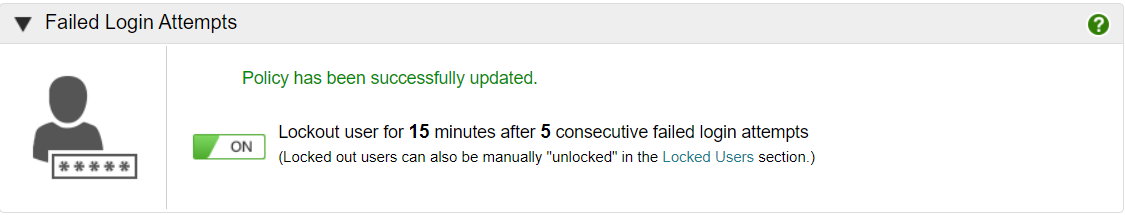
Failed login attempts
The 2021.1 release of removes the requirement for an external SQL database resulting in a simplified policy for handling failed login attempts.
This policy allows you to set the number of consecutive failed login attempts before a user is locked out for the specified time period.
Click Edit and set the number of consecutive failed login attempts before a user is locked out for the specified time period.
- Enter a minutes value between 1-60
- Enter login attempts value between 1-99
When complete, click Save.
If the policy is exceeded the lockout status is persisted only for the duration specified or until the administrator manually unlocks the user account. See Locked Users.
Any locked status is automatically removed if the cluster fails to exist - such as when applying a patch that requires all nodes within the cluster to be rebooted.
Set the number of consecutive failed login attempts before a user is locked out for the specified time period.
You can also specify the number of consecutive failed login attempts before locally stored data is wiped from the desktop or device.
If an account is wiped in this way, the user is put on the Remote Wipe list for the web platform which prevents the user from all web login attempts.
It is therefore recommended that you do not set the failed login attempts before wiping data at a very low figure (less than five).
This policy works differently for mobile devices where the PIN check occurs on the local device, not the server. There is no lockout for PIN attempts but if the Remote Wipe setting does apply - if the number of PIN attempts exceeds the Remote Wipe Failed Login Attempts number, the local device is wiped of all data and stored login credentials, including the PIN.
File Sharing
File Director 2020.2 and earlier included policy options to allow file sharing.
The following link opens an earlier version of the user help for File sharing.