UAC Replacement
In this section:
About UAC Replacement
UAC Replacement was introduced to Application Control release 2020.2. It complements the existing Self-Elevation functionality within Application Control and provides administrators with configurable levels of control.
Across a Windows environment executable files that require administrator privileges display a security shield icon overlay. The icon is also used in application dialogs to identify a process that requires administrator access. When such applications or processes are triggered by a standard user profile, the Windows UAC elevation prompt is displayed requiring administrator log in details.
With UAC Replacement turned on, the standard Windows UAC elevation prompt is replaced with the Application Control consent dialog. The feature applies irrespective of where or how the application is launched - such as from the Start Menu, Explorer, the Desktop, or the command prompt for example.
The UAC Replacement feature detects whether a selected application will display the Windows UAC prompt. If it does, the feature can be configured to:
-
Notify the user that elevated privileges are required and prompt for confirmation to proceed
-
Display a message box requiring users to provide a reason for elevated privileges.
Note that reasons supplied are stored as an audit event (ID 9063). Refer to Auditing for further information. -
Automatically supply the administrator access token
Note that as of Application Control 2020.3, when elevating an app using UAC Replacement, the elevation is applied to the app and its children.
There are instances where the UAC Replacement prompts will not apply. This includes when a user right-clicks on an application and selects Run as Administrator from the shortcut menu; or when a user launches an application installer.
Configure UAC Replacement
-
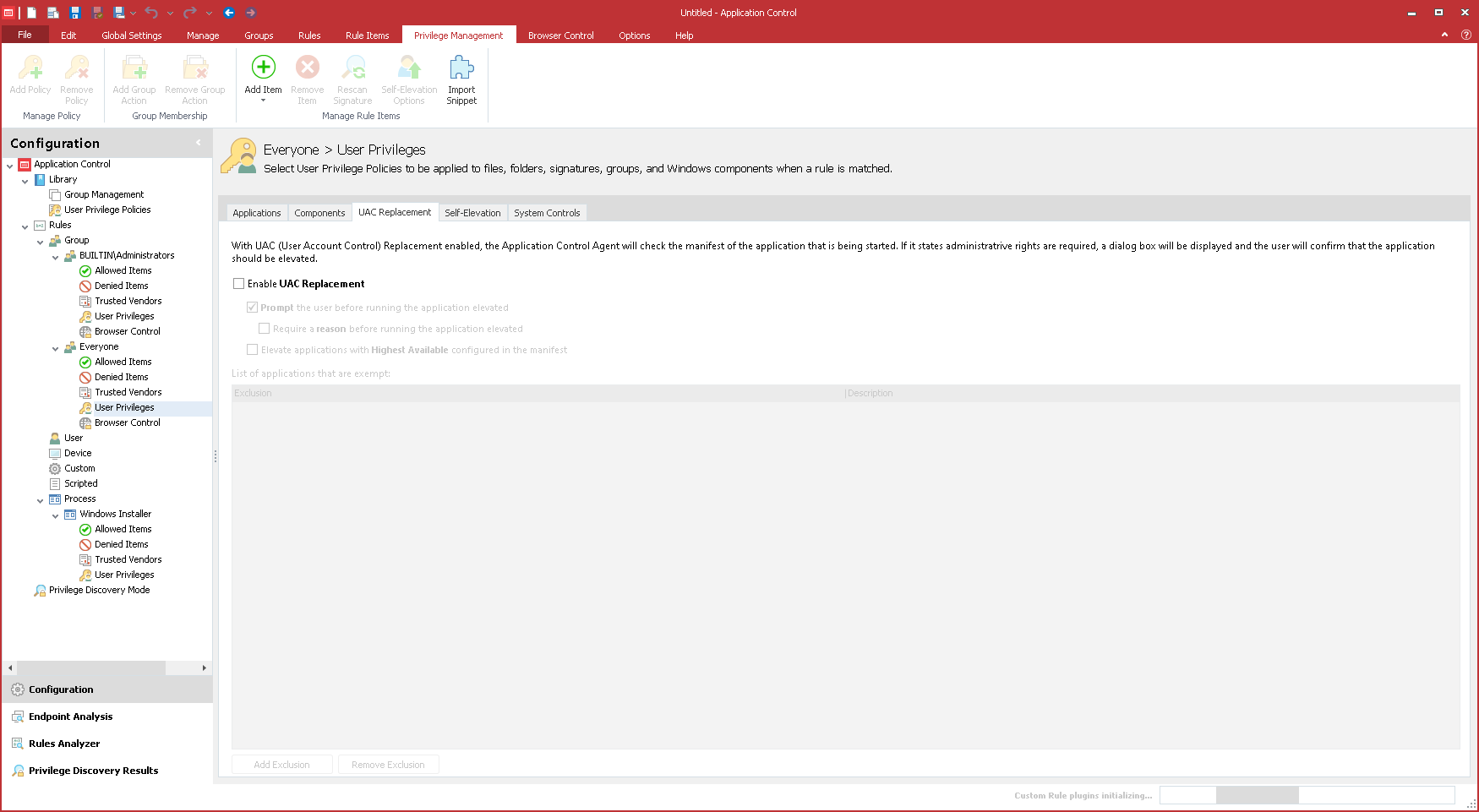
In the navigation pane click the User Privileges node for the applicable group required, then click the UAC Replacement tab.
-
Select the Enable UAC Replacement check box.
-
Select or clear the configuration options as follows:
Prompt user before running the application elevated
- With this option selected when the user attempts to open an application that would display the UAC prompt, they will be notified that elevated rights are required. The prompt allows the user to confirm they wish to continue, or cancel the action.
Note, the UAC Replacement prompt message can be configured via Message Settings. - Clear this check box to enable elevated privileges to be applied on demand without notifying or prompting the user.
Elevate applications with Highest/Available
This option affects applications that can be opened by both standard and administrator profiles but where the functionality offered to those users differs. For example, a standard user can run Regedit but the functionality offered is very limited. Users with admin rights can also run Regedit – and they will have access to much greater functionality.
-
Select this check box to apply UAC Replacement prompts for applications that will run with elevated privileges where possible.
-
Clear this check box to elevate only the applications that require administrative privileges to run.
UAC Replacement Exclusions
There may be applications that you wish to exclude from the UAC Replacement feature. For example, you may want to prevent elevated access to Regedit and other powerful applications on the grounds of security. Alternatively, you may have applications that are not compatible with this feature that you want to exclude.
Any applications that are excluded from UAC Replacement are listed in the Exclusion table. Applications can be added and removed from the table using the Add Exclusion and Remove Exclusion buttons.
Add an exclusion
-
Within the UAC Replacement tab, click the Add Exclusion button.
An editable row is inserted into the top of the Exclusion table. -
Specify the application you wish to exclude, and enter a description if required.
-
The application is specified by entering the path and file name of the executable - or a substring of it.
Note. Application Control rules engine performs a substring match on the value entered. The search is case insensitive and wildcards are not supported.
Example:
To exclude C:\windows\regedit.exe you could specify any of the following:
- C:\windows\regedit.exe
- windows\reg
- Regedit
Entering only a short substring is not recommended practice as it risks excluding many other applications unintentionally.
Remove an exclusion
-
Select the row required in the Exclusions table
-
Click Remove Exclusion.
The selected entry is removed.