About Security
CSM provides a default security design (complete with Security Groups, Roles, Teams/Workgroups, and system security settings). You can implement the default design (and just add users and customers, assigning them to other default Security Groups, Roles, and Team/Workgroups), edit it, or create a new security design.
Note: Security is configured and managed in CSM Administrator, typically by a system administrator.
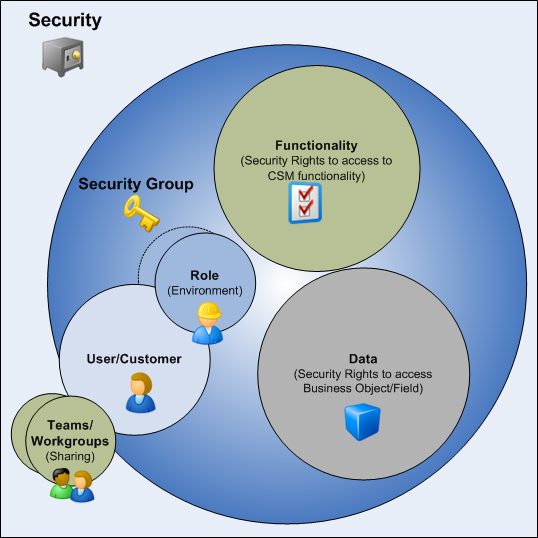
Security components include:
- Security Group: A collection of CSM security rights that controls access to CSM functionality and data (Business Objects/fields).
- Role: A user or customer's current function/responsibility in CSM, and controls how data is presented in that person's CSM environment.
- User: A service desk professional who logs in and uses CSM to manage service desk data (example: A technician, manager, designer, system administrator, etc.).
- Team: A collection of CSM users that can share CSM items (such as Dashboards), record ownership, and assignments.
- Customer: An end user, either an internal employee or an external individual, who relies on CSM to initiate/fulfill a Service or Product (example: A person reporting a lost password or requesting a new phone).
- Customer Workgroup: A collection of CSM customers who can share CSM items (such as Dashboards).