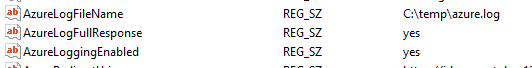Synchronizing Azure Domain
You can perform a fresh deployment of the SXS Server without requiring Active Directory by using the Workstation\Administrator account in the test environment during the SXS server installation, and later synchronize the Azure domain using the Azure Domain Synchronization feature in Ivanti Device and Application Control for seamless integration.
By default, the Azure Domain Synchronization feature is disabled in the Ivanti Device and Application Control Server after you upgrade the SXS installer and upgrade the SMC installer operations. DB upgrade is not required for Ivanti Device and Application Control.
Prerequisites
Below are the prerequisites.
Ivanti Device and Application Control SXS Application Server
-
Firewall ports
Ensure the following ports are appropriately opened as per the Ivanti Device and Application Control administrator policy. - 65229 (TLS port)
- 514 (Logging port)
- Internet Connectivity
The IDAC Server SXS machine must have internet connectivity to the Microsoft Azure cloud to validate Azure-related information.
- Azure Credentials
The creation of the following Azure credentials should be done by the Microsoft Entra ID Administrator:
For more information on API scopes, refer section Configuring Graph API in Microsoft Azure.
Ivanti Device and Application Control SXS Azure configuration
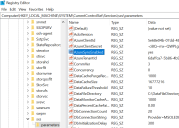
The following registry parameters must be configured at the specified path where SMC is installed. Please create registry folders if they are not present.
- [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\sxs\parameters]
- AzureTenantId=6daffca7-5b86-4b91-a38f-1ce1571694c1
- AzureClientId=5e68e04b-07dd-48e3-b151-4365b7864742
- AzureClientSecret=-ci8Q~mx~QWPLgYltlzJVTT-gPxMhHT1qrl-Dc4b
- AzureRedirectUri= https://idacazuretoken1234.blob.core.windows.net/web/Index.html
This is a demonstration URL. Please set up your static website in Azure. - AzureAdminUnitObjectIDs=3532db60-7495-4e5e-ae56-cbe59187db33
- AzureUsersAdminUnitObjectIDs=3532db60-7495-4e5e-ae56-cbe59187db33
- AzureDevicesAdminUnitObjectIDs=1f8cf098-9501-406d-aff4-65ed53332241
-
AzureAllowNonEntpAdminSync=yes/no
Important:
- The information provided above is for example purposes only. Please update the values to match the appropriate Azure-related information for your organization’s tenant portal.
- All registry parameters related to Entra ID sync are, by default, created under SXS‑Parameter registry on the SXS server machine and will be used as per the configuration. If the customer’s deployment involves placing the SMC console and SXS server on separate machines, all registry parameters related to Entra ID sync should be manually created in the SMC registry on the SMC console machine.
-
The AzureRedirectUri registry entry must only be configured if you plan to use Delegated type Microsoft Graph API permissions.
If you are using Application type Microsoft Graph API permissions, this entry can be left blank.- To configure Static Website in Azure https://learn.microsoft.com/en-us/azure/storage/blobs/storage-blob-static-website
- To download the link:
https://rm-csm-asia.s3.ap-southeast-2.amazonaws.com/UEM/HEATEndpointSecurity/StaticWebSiteForAzureEntraID.zip
- By default, the Entra ID sync feature is designed for users with the Enterprise Administrator role. If you want to use it for users with the Administrator role as well, then you need to set the value of the parameter AzureAllowNonEntpAdminSync to yes.
The default value of parameter AzureAllowNonEntpAdminSync is no.
The parameters AzureAdminUnitObjectIDs, AzureUsersAdminUnitObjectIDs, and AzureDevicesAdminUnitObjectIDs should only be configured if synchronization of data from administrative units is required.
-
AzureAdminUnitObjectIDs
This parameter will sync both users and devices from the specified administrative unit, represented by the object ID, with the Ivanti Device and Application Control database. -
AzureUsersAdminUnitObjectIDs
This parameter will only sync users from the specified administrative unit, represented by the object ID, with the Ivanti Device and Application Control database. -
AzureDevicesAdminUnitObjectIDs
This parameter will only sync devices from the specified administrative unit, represented by the object ID, with the Ivanti Device and Application Control database.
If all three registry parameters are configured, the synchronized data will be a union of all three administrative units, ensuring there are no duplicate entries.
Performing Azure Domain Synchronization
You can synchronize Ivanti Device and Application Control with Azure Domain using two methods:
-
Synchronization across the domain
-
Synchronization across administrative units
The steps for both synchronization methods are the same. The main difference is that, for synchronization across administrative units, you need to configure the following SXS registry parameters:
- AzureAdminUnitObjectIDs
- AzureUsersAdminUnitObjectIDs
- AzureDevicesAdminUnitObjectIDs
If the registry parameters for the administrative unit are empty, synchronization will occur across the domain represented by the tenant ID.
Step 1: Enabling Azure Domain Synchronization Functionality
To enable the Azure Domain Synchronization functionality, set the registry key value to yes for the AzureSyncEnabled parameter in the SXS registry key at the following location:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\sxs\parameters]
AzureSyncEnabled = yes
Step 2: Accessing the Azure Domain Synchronization Feature
To access the Azure Domain Synchronization feature, launch the Ivanti SMC console and follow these steps:
-
Click on Tools, then select Azure Domain Synchronization and follow the prompts as directed.
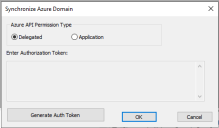
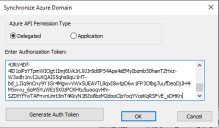
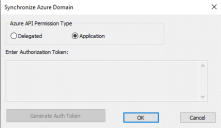
By default, Delegated type Graph API permissions are selected. Users can also choose to use Application type Graph API permissions, provided that these permissions have been configured through the Azure portal.
Delegated Type Permissions Workflow
For Delegated type Graph API permissions to function properly, it is necessary to first generate the authorization token.
-
Select the Delegated radio button if it is not already selected.
-
Click on the Generate Auth Token button.
-
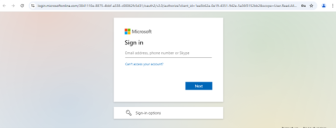
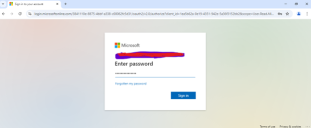
A web page will open, prompting for Azure Global Administrator account authorization, as shown below.
-
Enter the Azure Global Administrator account credentials that have permission to authorize Delegated Graph API permissions.
-
Enter the password for the account to proceed with the authorization.
-
Now approve the sign in request using the Microsoft Authenticator app.
-
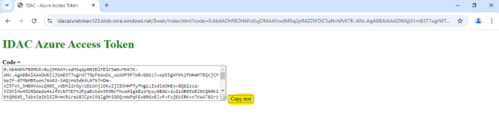
A new authorization token will get generated.
-
Click on Copy Text button and paste in authorization token edit box as shown below.
-
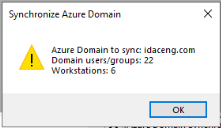
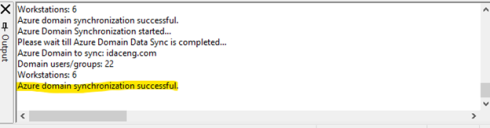
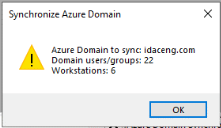
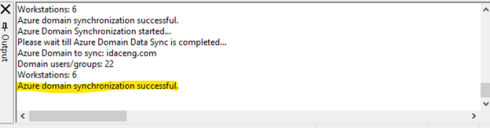
Click OK. If the authorization token is valid, you will receive a message indicating successful synchronization of Azure users, groups, and devices, as shown below.
-
Clicking OK will complete the synchronization process to the Ivanti Device and Application Control database, and a success message will appear, as shown below.
Application Type Permissions Workflow
For Application type Graph API permissions to function properly, follow the steps below:
-
The following permissions must be configured in the Azure portal for the Application type Graph API permissions:
- User.Read.All
- Device.Read.All
- GroupMember.Read.All
Once configured in the Azure portal, no additional authorization steps are needed.
-
Click on the OK button.
-
If the access token is valid and the Azure Tenant ID, Client ID, and Client Secret are correctly configured in the SXS registry, you will receive a synchronization message for Azure users, groups, and devices as shown below.
-
Clicking OK should complete the synchronization process to the Ivanti Device and Application Control database, and a success message will appear below.
It is important to close and restart the Azure Domain Synchronization Dialog from the Tools menu whenever there is any change in the registry. Otherwise, the new registry values will not be used during Microsoft Graph API requests.
Enabling Logging
Follow the steps below to enable logging:
-
To enable logging of Azure HTTP responses and buffer metadata for upload into the SX database, the following three registry parameters must be set:
-
AzureLoggingEnabled = yes
-
AzureLogFileName = C:\temp\azure.log
-
By default, the AzureLoggingEnabled and AzureLogFullResponse values are set to no, and AzureLogFileName is set to NULL. If you configure the logging parameters as follows:
-
AzureLoggingEnabled = yes
-
AzureLogFileName = C:\temp\azure.log
-
AzureLogFullResponse = no
The azure.log file will contain only the buffer metadata, without including the Azure HTTP responses.
-
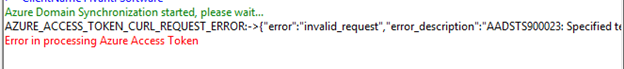
Failure of any Graph API requests used internally will be displayed directly on the SMC console, and there's no need to set AzureLoggingEnabled to yes to view Graph API failures. Below is an example of what occurs if the AzureTenantId value is not configured correctly in the registry.
Below is an example if we don’t configure AzureTenantId value correctly in registry.
Ivanti Device and Application Control Client prerequisites
The following prerequisites related to the Ivanti Device and Application Control Client are required:
-
An endpoint Microsoft Entra ID joined machine view as shown below.
-
The CDT package created using the Ivanti Client Deployment Tool (CDT) should be manually copied to the target system, and silent installation should be triggered from an elevated administrator command prompt using the following command:
Client.exe /exenoui /noprereqs /qn TRANSFORMS=Client.x64.mst /L*v %TMP%/setupcltsu.log - After the successful deployment of the IDAC client in TLS mode using wildcard-based machine certificates on AAD endpoints (e.g., *.idaceng.com), the CertGeneration=no setting should be updated in the SCOMC parameters. This update should be performed after the successful silent deployment and reboot of the AzureAD client machines.
The above step is not necessary for non-TLS mode of Ivanti Device and Application Control deployment.