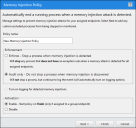
Enable Advanced Memory Protection
Application Control's Advanced Memory Protection feature protects against memory-based attacks, including buffer overflows and reflective memory injection (RMI). While RMI is generally associated with malware, some legitimate software vendors use RMI. For example, counterfeit deterrence system (CDS) software uses RMI with printers and scanners to prevent users from accessing or printing images of currency.
What is a Memory Protection Policy?
A Memory Protection policy detects and manages RMIs. The policy can operate in two modes:
-
Enforcement mode shuts down the affected process once the RMI is detected.
-
Audit mode logs the RMI without shutting down the process.
Use Audit Mode First
Apply a Memory Protection policy in audit mode to your initial group of endpoints. Review the logs over a few days to determine if any legitimate RMI is in use on your endpoints. Audit mode generates log events regardless if the RMI is malicious or legitimate.
If you see RMI detections immediately after applying the policy, determine whether the RMI is malicious or legitimate.
-
If detection occurs only on a single endpoint or with a single file, the RMI is more likely to be malicious.
-
If detection occurs on many endpoints and is easily reproducible, it is more likely that a process in your environment uses RMI legitimately.
For more information, see the Ivanti Community article Identifying Exceptions for Memory Injection Policies .
Manage Legitimate RMI Processes
If you encounter a legitimate RMI process, contact Support to confirm which application uses the RMI. Support can help you determine whether you can safely add the process as an exception to your Memory Protection policy.
When Ivanti identifies legitimate RMI processes, we add signatures for them to the Memory Protection module so that exceptions are no longer required. However, until signatures are available, you'll need to add legitimate processes as exceptions.
Extend Policy to Other Endpoints
Once you've added exceptions to your Memory Protection policy and the logs are showing no additional RMI events, extend the policy to additional endpoints in your environment. As with the initial endpoints, keep these additional endpoints in audit mode and review the logs for RMI events over a few days. When the logs show no additional RMI events, enforce the Memory Protection policy for all endpoints in your environment.
To Create a Memory Protection Policy
Use the Memory Injection Policy wizard to create a Memory Injection policy.
-
From the Endpoint Security console, select Manage > Memory Protection Policies.
-
On the Memory Protection tab, click Create.
The Memory Injection Policy wizard opens.
-
Complete the wizard. For detailed steps, see Creating a Memory Injection Policy in the Application Control Help.