Create a Memory Injection Detection Events Log Query
Create a daily All Memory Injection Detection Events log query so that you can see if reflective memory injection (RMI) events are occurring on your endpoints. Such events could indicate malicious activity or could be a result of legitimate application behavior. In either case, the log query acts as the trigger to investigate RMI activity.
Create the Memory Injection Detection Events Log Query
-
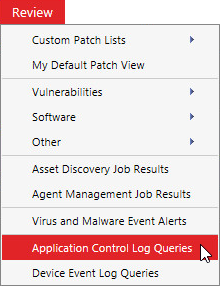
From the Endpoint Security Console, select Review > Application Control Log Queries.
-
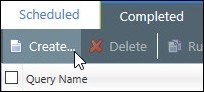
On the Application Control Log Queries page, click Create.
The Application Control Log Query wizard opens.
-
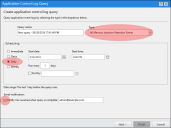
Complete the following in the wizard:
-
Type a name for the new query in the Query Name field.
-
Under Type, select All Memory Injection Detection Events.
-
Under Scheduling, select Daily. Define a Start date and Start time.
-
Select whether to have an email sent to you when the query is complete.
We recommend you receive email notifications. These act as a daily reminder to review the logs and update the policies as needed. Make sure that you have already defined your email server within Endpoint Security. See Configuring Alert Settings in the Endpoint Security Help.
-
-
Click Next and add endpoints or groups of endpoints to the query.
-
Click Finish to create the query. After the query runs, view its summary and results on the Completed tab.
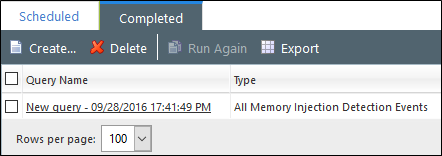
Add Exceptions for Legitimate RMI Processes
If RMI events are associated with legitimate software behavior, add exceptions to the Memory Protection policy you created in Phase 2 to prevent these applications from being terminated when enforcement is enabled.
-
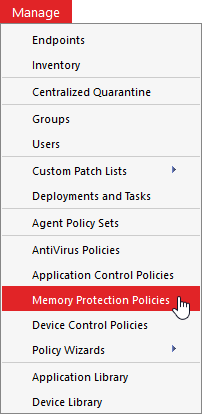
From the Endpoint Security console, select Manage > Memory Protection Policies.
-
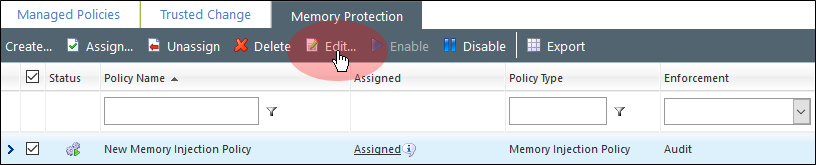
On the Memory Protection tab, select the Memory Injection policy you created and click Edit.
The Memory Injection Policy wizard opens.
-
Click Next.
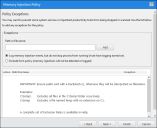
The Policy Exceptions page displays.
-
Enter the path or file name.
-
Select whether to Log memory injection events, but do not stop the process from running or Exclude from policy.
-
Click Add.
-
Repeat steps 4 through 6 to add all required paths or files as needed.
-
Click Finish.