Running Scan Now on Selected Targets
You can run a Scan Now from pages where you have selected target endpoints or groups.
Administrators will often use the Endpoints and Groups pages, as they provide useful information such as operating system details and agent information. If an administrator decides to run an antivirus scan on one or more groups or endpoints, the Virus and Malware Scan Wizard can be launched from these pages to run the scan.
Running Scan Now on an Endpoint
You can use the Virus and Malware Scan Wizard to run an antivirus scan on endpoints that are selected on the Endpoints page.
This wizard is similar to the Virus and Malware Scan Wizard available on the Discover menu, except that it does not have a Targets page.
- Select Manage > Endpoints.
The Endpoints page opens. - Select the Antivirus tab.
- Select one or more endpoints to be scanned.
- Click Scan Now.
- [Optional] Type a new name in the Scan Name field.
- Schedule the scan using one of the following methods:
- Select the Run scan at option.
- Type the start date in the Start date field. You can also select the start date by clicking the Calendar icon.
- Type the start time in the Start time field using a hh:mm format followed by AM or PM. This field supports both 12- and 24-hour time. Alternatively, you can select the start time by clicking the Clock icon.
- Click Next.
The Scan Options page opens.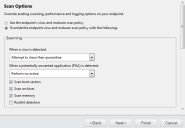
- From the drop-down list, select the action that occurs when a virus is detected.
- To clean an infected file means to completely remove the malicious code so that the file is safe to use. It is not always possible to remove the malicious code, however. When this happens, you can either delete the file or quarantine it. To quarantine means to move it to a safe place on the endpoint where it can be kept for further examination.
In certain cases (such as when the malware is a Trojan) the entire file is malicious. Such a file cannot be cleaned, so the only options are to quarantine or delete it. - Virus detection actions are not used for memory scans.
- From the drop-down list, select the action to be taken when a potentially unwanted application (PUA) is detected:
-
Set the Scanning options:
-
Perform no action - the boot sector is left as it is and an alert is sent to the Virus and Malware Event Alerts page.
-
Clean/Delete/Quarantine - the boot sector is automatically repaired.
- If the scan detects a virus/malware in memory, it will report the event. It will not clean, delete, or quarantine the virus/ malware.
- Exclusions are not applied to memory scans.
- Set the CPU utilization % threshold to control the level of impact the scan is to have on endpoint performance:
- Set the logging options:
- Exclude files or paths, using one of the following methods:
- Click Add.
A blank entry is added to the exclusions list. - Select an exclusion type from the Type field.
The types are File and Folder. - Enter the path to the item you want to exclude in the Path field.
- Click
 to add the exclusion to the list.
to add the exclusion to the list.
Repeat this procedure for all files and folders you want to exclude from the scan. - When you are satisfied with all settings made on the Virus and Malware Scan Wizard, click Finish.
The Virus and Malware Scan Wizard closes. After the scan job completes, you can see the results on the Virus and Malware Scan Results page.
If you do not select any endpoints before clicking Scan Now, all the endpoints are selected by default. You will then see the following dialog: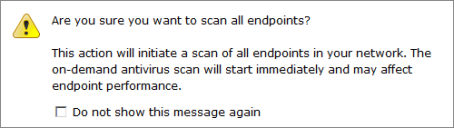
Click Yes to scan all endpoints, or click No to return to the list and select particular endpoints.
The Scan Now - Virus and Malware Scan wizard opens to the Scan Name and Scheduling page.
By default, new virus scans are named New Virus and Malware Scan, followed by the server's date and time, which is formatted according to your browser's locale setting.
|
Method |
Steps |
|---|---|
|
To schedule an immediate scan: |
Select the Run scan immediately option. |
|
To schedule a later scan: |
The purpose of the deferred scan feature is to enable you to schedule the scan at a time that will not adversely affect network or endpoint performance. |
|
Setting |
Result |
|---|---|
|
Perform no action |
Does nothing with the infected file, but sends an alert to the server. |
|
Attempt to clean then quarantine
|
Attempts to clean the infected file. If this is not possible, the file is quarantined. An alert is sent to the server. |
|
Attempt to clean then delete |
Attempts to clean the infected file. If this is not possible, the file is deleted. An alert is sent to the server. |
|
Attempt to clean then quarantine then delete |
Attempts to clean the infected file. If this is not possible, the file is quarantined. If it is not possible to quarantine it, it is deleted. An alert is sent to the server. |
Note:
|
Setting |
Result |
|---|---|
|
Perform no action
|
The system ignores the potentially unwanted application. |
|
Send alert only |
An alert is sent to the server only. |
|
Alert and action (treat as malware) |
An alert is sent to the server and the file is cleaned, quarantined, or deleted, according to the action you selected in the When a virus is detected drop down. |
|
Setting |
Result |
|---|---|
|
Scan boot sectors |
The virus scan will be more thorough if you scan boot sectors in addition to program and data files. Note: If malware is detected in a boot sector, the action taken depends on the virus detection option selected: |
|
Scan archives |
The virus scan will be more thorough if you scan archive files such as .zip and .cab files. Infected .rar files can be quarantined and deleted, but can't be cleaned. |
|
Scan memory |
The virus scan will be more thorough if you scan the memory in addition to the disk(s). Note: |
|
Rootkit detection |
A rootkit, similar to a hack tool, enables attackers to gain administrator access to a system. They hide the attacker's presence and give them full control of a server or client endpoint without being noticed. |
|
Setting |
Result |
|---|---|
|
High |
Quicker scanning but may noticeably impact endpoint performance. |
|
Medium |
Balances scan speed with endpoint performance impact (default option). |
|
Low |
Slower scanning but has the lowest impact on endpoint performance. |
As logging information is kept on the endpoint, the option you choose will not affect the loggings sent to the server.
|
Setting |
Result |
|---|---|
|
Do not log scanning results |
No scan log is generated. |
|
Normal logging level (includes results summary) |
A standard scan log is generated. |
|
Detailed logging level (includes results summary, name, time and status for each scanned file) |
A detailed scan log is generated. Caution: Logging detailed virus scan results typically generates large amounts of data, especially when recurring scans run frequently. |
Masks and system variables can be used to exclude files and paths, see Exclusion Rules.
|
Method |
Steps |
|---|---|
|
Manually exclude specific files and folders from the scan. |
Click Remove ( |
|
Import an XML file containing a formatted list of file and folder exclusions. |
Running a Custom Scan Now on an Endpoint Using the Agent Control Panel
An endpoint user can manually initiate an on-demand virus and malware scan that targets specific drives, folders, and files.
Prerequisites:
- You must be on an endpoint hosting a Ivanti Endpoint Security Agent.
- No Scan Now or Recurring Virus and Malware Scan in progress.
- Ensure the endpoint has the latest version of the AntiVirus Engine and Definition file.
- Connect any removable media you want to scan to the endpoint (for example, a USB drive).
The ability to narrow scan scope enables you to use a custom Scan Now to:
- Target suspicious sections of media (for example, folders where content is frequently modified and accessed).
- Discover infected files before you use them.
- Scan only specific removable media (for example, a USB drive or DVD).
- Immediately scan files downloaded from the Internet or received by e-mail.
The scan settings used for a custom Scan Now to control performance and manage detected viruses are:
- Scan boot sectors: Off
- Scan archives: On
- Scan memory: Off
- Rootkit detection: On (supported on endpoints running Windows versions from Vista onwards)
- CPU utilization %: Resolved by the endpoint's resultant policy (default of "Medium" where no Recurring Virus and Malware Scan Policy is assigned).
- Virus detection actions: Resolved by the endpoint's resultant policy. Default of “Attempt to clean then quarantine then delete” where no Real-time Monitoring Policy is assigned.
- Potentially Unwanted Application (PUA) detection action: Resolved by the endpoint's resultant policy. Default of "Alert and action (treat as malware)" where no Real-time Monitoring Policy is assigned.
- File and Path Exclusions: Off
When you target a drive or folder, all files and folders it contains (including hidden) are scanned and permissions overruled.
You can view the resultant policy assigned to an endpoint on the Endpoints details page.
- On the endpoint, select Start > Control Panel
- Double-click Agent Control Panel.
The Agent Control Panel. - From the main menu, click AntiVirus > Scan Now & Events.
The Scan Now & Events panel displays. - Click Custom Scan.
- Select the drives, folders, and files you want to scan, and then click OK.
A custom Scan Now commences on the endpoint and "Scan In Progress" displays at the top of the panel. Viruses and malware detected during the scan appear on the Virus and Malware Event Alerts page in the Ivanti Endpoint Security Management Console.
The Custom Scan button is disabled when a Scan Now or Recurring Virus and Malware Scan is in progress on the endpoint.
A dialog box that enables you to select files and folders displays.
After Completing This Task:
On completion of scanning, you can:
- View the Scan Now log file on the endpoint in <INSTALL_DIR>\LMAgent\logs\AV.
- Manage detected threats in quarantine.
- Report threats as false positives to Ivanti.
Running a Full Scan Now on an Endpoint Using The Agent Control Panel
An endpoint user can quickly initiate a thorough local on-demand virus and malware scan that targets all drives, folders, and files without the need to manually configure scan settings.
Prerequisites:
- You must be on an endpoint hosting a Ivanti Endpoint Security Agent.
- No Scan Now or Recurring Virus and Malware Scan in progress.
- Ensure you have the latest version of the AntiVirus Engine and Definition file.
- Connect any removable media you want to scan to the endpoint (for example, a USB drive).
Use a full Scan Now in the following situations:
- Odd behavior observed on the endpoint.
- Virus outbreak in the network.
- After considerable Internet use and downloading activity.
- Long duration between scheduled Virus and Malware scans.
Scan settings configure automatically based on the endpoint's resultant policy. The default settings when no Recurring Virus and Malware Scan Policy is assigned are:
- Scan boot sectors: On
- Scan archives: On
- Scan memory: On
- Rootkit detection: On (supported on endpoints running Windows versions from Vista onwards)
- CPU utilization %: Medium
- Virus detection actions: Attempt to clean then quarantine then delete
- Potentially Unwanted Application (PUA) detection action: Alert and action (treat as malware)
- File and Path Exclusions: None
All files and folders (including hidden) are scanned and permissions overruled.
You can view the resultant policy assigned to an endpoint on the Endpoints details page.
- On the endpoint, select Start > Control Panel
- Double-click Agent Control Panel.
The Agent Control Panel opens. - From the main menu, click AntiVirus > Scan Now & Events.
The Scan Now & Events panel displays. - Click Full Scan.
The Full Scan button is disabled when a Scan Now or Recurring Virus and Malware Scan is in progress on the endpoint.
A full Scan Now commences on the endpoint and "Scan In Progress" displays at the top of the panel. Viruses and malware detected during the scan appear on the Virus and Malware Event Alerts page in the Ivanti Endpoint Security Management Console.
After Completing This Task:
On completion of scanning, you can:
- View the Scan Now log file on the endpoint in <INSTALL_DIR>\LMAgent\logs\AV.
- Manage detected threats in quarantine.
- Report threats as false positives to Ivanti.
Running Scan Now on a Group
You can use the Virus and Malware Scan Wizard to run a virus scan on groups that have been selected on the Groups page.
This wizard is similar to the Virus and Malware Scan Wizard available on the Discover menu, except that it does not have a Targets page.
- Select Manage > Groups.
The Groups page opens. - Use the Group Browser to select one or more groups to be scanned.
- Select Virus and Malware Event Alerts from the View list.
- Click Scan Now.
The Virus and Malware Scan Wizard opens to the Scan Name and Scheduling page. - [Optional] Type a new name in the Scan Name field.
- Schedule the scan using one of the following methods:
- Select the Run scan at option.
- Type the start date in the Start date field. You can also select the start date by clicking the Calendar icon.
- Type the start time in the Start time field using a hh:mm format followed by AM or PM. This field supports both 12- and 24-hour time. Alternatively, you can select the start time by clicking the Clock icon.
- Click Next.
The Scan Options page opens. - Select the scan policy option:
- From the drop-down list, select the action that occurs when a virus is detected.
- To clean an infected file means to completely remove the malicious code so that the file is safe to use. It is not always possible to remove the malicious code, however. When this happens, you can either delete the file or quarantine it. To quarantine means to move it to a safe place on the endpoint where it can be kept for further examination.
In certain cases (such as when the malware is a Trojan) the entire file is malicious. Such a file cannot be cleaned, so the only options are to quarantine or delete it. - Virus detection actions are not used for memory scans.
- Set the Scanning options:
-
Perform no action - the boot sector is left as it is and an alert is sent to the Virus and Malware Event Alerts page.
-
Clean/Delete/Quarantine - the boot sector is automatically repaired.
- If the scan detects a virus/malware in memory, it will report the event. It will not clean, delete, or quarantine the virus/ malware.
- Exclusions are not applied to memory scans.
- From the drop-down list, select the action to be taken when a potentially unwanted application (PUA) is detected:
- Set the CPU utilization % threshold to control the level of impact the scan is to have on endpoint performance:
- Set the logging options:
- Exclude files and folders, using one of the following methods:
- Click Add.
A blank entry is added to the exclusions list. - Select an exclusion type from the Type field.
The types are File and Folder. - Enter the path to the item you want to exclude in the Path field.
- Click
 to add the exclusion to the list.
to add the exclusion to the list.
Repeat this procedure for all files and folders you want to exclude from the scan. - When you are satisfied with all settings made on the Virus and Malware Scan Wizard, click Finish.
The Virus and Malware Scan Wizard closes. After the scan job completes, you can see the results on the Virus and Malware Scan Results page.
By default, new virus scans are named New virus and malware scan, followed by the server's date and time, which is formatted according to your browser's locale setting.
|
Method |
Steps |
|---|---|
|
To schedule an immediate scan: |
Select the Run scan immediately option. |
|
To schedule a later scan: |
The purpose of the deferred scan feature is to enable you to schedule the scan at a time that will not adversely affect network or endpoint performance. |
|
Setting |
Result |
|---|---|
|
Use the endpoint's virus and malware scan policy |
The scanning, performance, and logging options of the endpoint's policies will be used. You can click Finish to start the scan. |
|
Override the endpoint virus and malware scan policy with the following: |
Enables the Scanning, CPU utilization %, and Logging level controls. Important: Ensure you have a clear understanding of the scan options before overriding the default settings. |
|
Setting |
Result |
|---|---|
|
Perform no action |
Does nothing with the infected file, but sends an alert to the server. |
|
Attempt to clean then quarantine
|
Attempts to clean the infected file. If this is not possible, the file is quarantined. An alert is sent to the server. |
|
Attempt to clean then delete |
Attempts to clean the infected file. If this is not possible, the file is deleted. An alert is sent to the server. |
|
Attempt to clean then quarantine then delete |
Attempts to clean the infected file. If this is not possible, the file is quarantined. If it is not possible to quarantine it, it is deleted. An alert is sent to the server. |
Note:
|
Setting |
Result |
|---|---|
|
Scan boot sectors |
The virus scan will be more thorough if you scan boot sectors in addition to program and data files. Note: If malware is detected in a boot sector, the action taken depends on the virus detection option selected: |
|
Scan archives |
The virus scan will be more thorough if you scan archive files such as .zip and .cab files. Infected .rar files can be quarantined and deleted, but can't be cleaned. |
|
Scan memory |
The virus scan will be more thorough if you scan the memory in addition to the disk(s). Note: |
|
Rootkit detection |
A rootkit, similar to a hack tool, enables attackers to gain administrator access to a system. They hide the attacker's presence and give them full control of a server or client endpoint without being noticed. |
|
Setting |
Result |
|---|---|
|
Perform no action
|
The system ignores the potentially unwanted application. |
|
Send alert only |
An alert is sent to the server only. |
|
Alert and action (treat as malware) |
An alert is sent to the server and the file is cleaned, quarantined, or deleted, according to the action you selected in the When a virus is detected drop down. |
|
Setting |
Result |
|---|---|
|
High |
Quicker scanning but may noticeably impact endpoint performance. |
|
Medium |
Balances scan speed with endpoint performance impact (default option). |
|
Low |
Slower scanning but has the lowest impact on endpoint performance. |
As logging information is kept on the endpoint, the option you choose will not affect the loggings sent to the server.
|
Setting |
Result |
|---|---|
|
Do not log scanning results |
No scan log is generated. |
|
Normal logging level (includes results summary) |
A standard scan log is generated. |
|
Detailed logging level (includes results summary, name, time and status for each scanned file) |
A detailed scan log is generated. Caution: Logging detailed virus scan results typically generates large amounts of data, especially when recurring scans run frequently. |
Masks and system variables can be used to exclude files and paths, see Exclusion Rules.
|
Method |
Steps |
|---|---|
|
Manually exclude specific files and folders from the scan. |
Click Remove ( |
|
Import an XML file containing a formatted list of file and folder exclusions. |