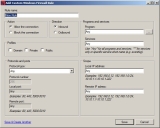
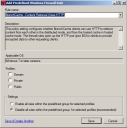
The Windows Firewall Wizard
The Ivanti Software Windows Firewall Wizard (Windows Firewall Wizard) allows you to create system management policy content that enforces Windows Firewall policy on managed devices within your network. The Windows Firewall Wizard allows you to use predefined policies or create custom Windows Firewall policies.
Once created, the Windows Firewall policies can provide administrators the ability to define Windows Firewall policies for Windows Vista and higher operating systems.
Ivanti Software recommends using the Windows Firewall Wizard to create a single policy to enforce your Windows Firewall policy settings.
Creating multiple firewall patches can cause overlapping policy rules, which may cause conflicting or inadequate Windows Firewall policy settings within your network.
To create Windows Firewall policies using the Windows Firewall Wizard, refer to Creating a Windows Firewall Rule.
Important: The Windows Firewall Wizard cannot override any firewall changes made by Group Policy Objects (GPOs). For additional information on Windows Firewall and GPOs, refer to Managing Windows Firewall with Advanced Security by Using Group Policy (https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc753955(v=ws.10)).
After creating the single policy, it can be found in the Ivanti Endpoint Security database.
Refer to Viewing Packages in the Ivanti Endpoint Security User Guide (https://www.ivanti.com/support/product-documentation) for instruction in finding created patch packages.
As part of a complete package for administrators to define Windows Firewall policies, Ivanti Software provides a patch, that when deployed to applicable endpoints will remove any custom Windows Firewall rules and allow you to restore Windows Firewall settings to system defaults. Refer to Restoring Windows Firewall Defaults for additional information.
Creating a Windows Firewall Rule
Create a Windows Firewall rule that enforces Windows Firewall policy using the Ivanti Software Windows Firewall Wizard.
Prerequisites:
Log in to the Ivanti Endpoint Security server from the Ivanti Content Wizard.
- Select Tools > Windows Firewall Wizard.
The Windows Firewall Policy Details page opens.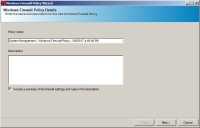
- Type a unique name for the policy in the Policy Name field.
- Type a description of the policy in the Description field.
- Ensure the Include a summary of the firewall settings and rules in the description check box is selected.
This will append to the patch description a summary of the firewall settings and rules. - Click Next.
The Network Profile Settings page opens.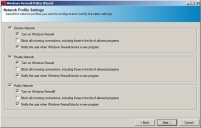
- All network profiles are checked.
- Turn on Windows Firewall is checked under each profile.
- Block all incoming connections, including those in the list of allowed programs is not checked under each profile.
- Notify the user when Windows Firewall blocks a new program is checked under each profile.
- Click Next.
The Windows Firewall Rules page opens.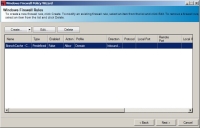
- Based on the type of Windows Firewall policy you require, select a menu item from the Create menu.
- If your choice displays the Add Custom Windows Firewall Rule page, complete the applicable steps.
- Type the name of the custom rule in the Rule name field.
- Select the applicable Action option.
The following table describes each option. - Select the applicable Direction option. The following table describes each option.
- Select the Profiles option(s) as required by your Windows Firewall needs.
The following table describes each option. - Define the Protocols and ports options:
- Select the protocol that you want from the Protocol type drop-down list.
Refer to Understanding Protocol Types for a description of each protocol type. - Type the applicable port number in the Local port field.
- Type the applicable port number in the Remote port field.
The Protocol number field is pre-populated with the appropriate number and is read-only.
- Select the protocol that you want from the Protocol type drop-down list.
- Define the Program and services needed.
This option is used to specify how Windows Firewall will match criteria based on which program or service on the endpoint is sending the packets to the server.
The following table describes each property. - Type the applicable Scope addresses. The following table describes each field.
- 192.168.0.12
- 192.168.0.12, 192.168.0.13
- 192.168.0.0/24
- 192.170.1.1-192.170.1.222
- 192.168.0.12
- 192.168.0.12, 192.168.0.13
- 192.168.0.0/24
- 192.170.1.1-192.170.1.222
- Click Save.
The Custom Windows Firewall Rule page closes and the rule is displayed in the Windows Firewall Rules page window. - If your choice displays the Add Predefined Windows Firewall Rule page, complete the applicable steps.
- Select a rule from the Rule name drop-down list of predefined rules.
The description, applicable OS, and default options within the Add Predefined Windows Firewall Rule page reflect the item choice. - [Optional] Select or change the Profiles setting based on your Windows Firewall requirements. The following table describes each option.
- [Optional] Change the Settings option, if applicable. The following table describes each option.
- Click Save.
The Predefined Windows Firewall Rule page closes and the rule is displayed in the Windows Firewall Rules page window. - If your choice displays the Delete Windows Firewall Rule page, complete the applicable steps.
- Type the name of the rule in the Rule name field.
The rule will delete all firewall rules that use the specified rule name. - Click Save.
The Delete Windows Firewall Rule page closes and the rule is displayed in the Windows Firewall Rules page window.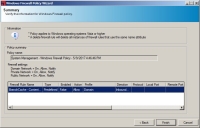
The Save & Create Another link creates the rule and adds it to the Windows Firewall Rules page window. The page refreshes to allow the user to create another rule.
- Type the name of the rule in the Rule name field.
- The rule displayed in the Windows Firewall Rules page window reflects the type of Windows Firewall option created.
- Use the Windows Firewall Rules toolbar options to modify the applicable firewall rule as needed.
The following table describes each toolbar option. -
Edit Custom Windows Firewall Rule page. Refer to Custom Windows Firewall Rule Options for additional information.
-
Edit Predefined Windows Firewall Rule page. Refer to Predefined Windows Firewall Rule Options for additional information.
-
Edit Delete Windows Firewall Rule page. Allows you to change the name of the rule in the Rule name field.
- Review your rules within the Windows Firewall Rules page.
- Click Next.
The Summary page opens displaying information concerning the Windows Firewall policy. - Once you have verified the summary information, click Finish.
The Summary page closes and the Patch Properties page displays. - [Optional] The Patch Properties page displays properties associated with the selected patch.
Review and edit the patch properties as needed. - SelectFile > Save.
The patch is stored within the Ivanti Endpoint Security server.
A default name is created automatically and is set to System Management – Windows Firewall Policy MM/DD/YYYY HH:MM:SS TT.
Note: The default values are the following:
Important: If the Domain Network check box is not selected, the patch will not deploy to endpoints within your network.
|
Menu Item |
Step |
|---|---|
|
Custom rule |
Select Create > Custom rule. |
|
Predefined rule |
Select Create > Defined rule. |
|
Delete firewall rule |
Select Create > Delete firewall rule. |
If you choose to not select a Windows Firewall policy option, your policy content will be based on the settings in the Network Profile Settings page.
|
Option |
Description |
|---|---|
|
Allow the connection (radio button) |
Allows the connection to be inbound or outbound for communication. |
|
Block the connection (radio button) |
Blocks the connection for inbound or outbound communication. |
|
Option |
Description |
|---|---|
|
Inbound (radio button) |
Inbound communication connection. |
|
Outbound (radio button) |
Outbound communication connection. |
|
Option |
Description |
|---|---|
|
Domain (check box) |
A policy setting that controls the Windows Firewall whenever the computer is connected to domain networks such as a workplace domain. |
|
Private (check box) |
A policy setting that controls the Windows Firewall whenever the computer is connected to trusted networks such as a home or small office network. |
|
Public (check box) |
A policy setting that controls the Windows Firewall whenever the computer is connected to untrusted networks at a public place such as at coffee shops, hotels, or airports. |
At least one profile type is required. However, you may select multiple profiles as dictated by your Windows Firewall requirements.
|
Option |
Description |
|---|---|
|
Program (field and/or button) |
You may type the full path to the executable (.exe) file or select the ellipses button (...), which opens the windows explorer browser window to allow a user to locate a file on the local system. The default is Any. Important: If content is deployed to multiple endpoints, using the browse feature will only work if all of your endpoints contain the program under the same exact path specified. |
|
Services (field) |
You may type the name of the service. The default is Any. Tip: A system service that runs within its own unique .exe file and is not hosted by a service container is considered to be a program and can be added. Refer to Microsoft Knowledge Base Article 211362 (http://support.microsoft.com/kb/271362) on how to find short names for installed Windows services. |
|
Option |
Description |
|---|---|
|
Local IP address |
The IP address of the network interface on which the connection is made. Type a single IP address, multiple single IP addresses, or an IP address range using a single IP address using CIDR modifiers such as commas, slashes (/), or dashes (-). Examples: Due to a Microsoft bug, you cannot use CIDR modifiers when entering multiple IP addresses. As a workaround, use two IP address ranges instead of two IP addresses with a CIDR modifier. |
|
Remote IP address (field) |
This is the IP address of the remote computer to which the connection is made. Type a single IP address, multiple single IP addresses, or an IP address range using a single IP address using CIDR modifiers such as commas, slashes (/), or dashes (-). Examples: Due to a Microsoft bug, you cannot use CIDR modifiers when entering multiple IP addresses. As a workaround, use two IP address ranges instead of two IP addresses with a CIDR modifier. |
The Save & Create Another link creates the rule and adds it to the Windows Firewall Rules page window. The page refreshes to allow the user to create another rule.
The Rule name drop-down list contains well known services and programs available on endpoints running a Windows operating system.
|
Option |
Description |
|---|---|
|
Domain |
A policy setting that controls the Windows Firewall whenever the computer is connected to domain networks such as a workplace domain. |
|
Private |
A policy setting that controls the Windows Firewall whenever the computer is connected to trusted networks such as a home or small office network. |
|
Public |
A policy setting that controls the Windows Firewall whenever the computer is connected to untrusted networks at a public place such as at coffee shops, hotels, or airports. |
At least one profile type is required. However, you may select multiple profiles as dictated by your Windows Firewall requirements.
|
Option |
Description |
|---|---|
|
Enable all rules within the predefined group for selected profiles |
This will enable all rules for the predefined group based on the Profiles option(s) selected. |
|
Disable all rules within the predefined group for selected profiles (recommended) |
This will disable all rules for the predefined group based on the Profiles option(s) selected. |
The Save & Create Another link creates the rule and adds it to the Windows Firewall Rules page window. The page refreshes to allow the user to create another rule.
|
Name |
Description |
|---|---|
|
Create (menu) |
Opens the Create menu. |
|
Custom rule (Create menu item) |
Opens the Add Custom Windows Firewall Rule page. Repeat step 8 to add an additional custom Windows Firewall rule. |
|
Predefined rule (Create menu item) |
Opens Add Predefined Windows Firewall Rule page. Repeat step 9 to add an additional predefined Windows Firewall rule. |
|
Delete rule (Create menu item) |
Opens the Delete Windows Firewall Rule page. Repeat step 10 to add an additional delete Windows Firewall rule. |
|
Edit |
Opens one of the following pages based on the rule type selected. |
|
Deletes |
Deletes the selected rule in the Windows Firewall Rules page. Caution: The firewall rule is deleted automatically. No dialog displays warning you of a pending deletion of the rule. |
Tip: Select the Back button to go back to the Windows Firewall Rules page.
For information on Patch Properties, refer to The Patch Properties Page.
The new custom rule for your Windows Firewall policy is created and ready to use.
Refer to Viewing Packages in the Ivanti Endpoint Security User Guide (https://www.ivanti.com/support/product-documentation) for instruction in finding created packages.
Understanding Protocol Types
There are various protocol types used to help filter network traffic. Each protocol type uses a currently assigned IP protocol number.
Protocol types are available as a drop-down list within the Add Custom Windows Firewall Rule page in the Ivanti Software Windows Firewall Wizard.
The Protocol number field is pre-populated with the appropriate number and is read-only.
Refer to Creating a Windows Firewall Rule for more information on using the Ivanti Software Windows Firewall Wizard.
The following table describes each option.
|
Name (Full Name) |
Number |
Description |
|---|---|---|
|
Any |
256 |
Used for rule settings that apply to any protocol (even those not listed). |
|
HOPOPT (IPv6 Hop-by-Hop Option) |
0 |
Used to alert routers that an IP datagram contains control data that the router will need to handle. When this option is set in the header, the router performs additional parsing on the packets. |
|
ICMPv4 (Internet Control Message Protocol version 4) |
1 |
Used to send errors and other messages that are used to analyze networks. |
|
IGMP (Internet Group Management Protocol) |
2 |
Used by IP hosts and multicast routers to establish and manage the membership of IP multicast groups. |
|
TCP (Transmission Control Protocol) |
6 |
Provides a reliable, connection-oriented packet delivery service and is based on point-to-point communication between two network hosts. TCP guarantees delivery and verifies sequencing for any datagrams. |
|
UDP (User Datagram Protocol) |
17 |
Provides a fast reliable way to send and receive data between TCP/IP hosts. Unlike TCP, UDP does not guarantee delivery or verify sequencing for any datagrams. |
|
IPv6 (Internet Protocol version 6) |
41 |
This improves on Internet Protocol version 4 (IPv4) by vastly increasing the number of available addresses and by enabling more efficient routing, simpler configuration, built-in IP security, and better support for real-time data delivery. |
|
IPv6-Route |
43 |
This is the Routing Header for IPv6. |
|
IPv6-Frag |
44 |
This is the Fragment Header for IPv6. |
|
GRE (Generic Route Encapsulation) |
47 |
Used to encapsulate a variety of generic network layer packets. The protocol is designed to be stateless. |
|
ICMPv6 (Internet Control Message Protocol version 6) |
58 |
This is to send errors and other messages used to analyze networks. |
|
IPv6-NoNxt (No Next Header for IPv6) |
59 |
Used to communicate that there are no additional headers to process. |
|
IPv6-Opts (Destination Options for IPv6) |
60 |
Used to indicate that the next header is the Destination Options header, which is used to specify processing or delivery parameters to either intermediate or final destinations. |
|
VRRP (Virtual Router Redundancy Protocol) |
112 |
Used to increase the availability of the default gateway for hosts on a subnet. |
|
PGM (Pragmatic General Multicast) |
113 |
Used to improve the reliability of a data stream to multiple network recipients. |
|
L2TP (Layer 2 Tunneling Protocol) |
115 |
Used to facilitate virtual private network (VPN) connections. |
Custom Windows Firewall Rule Options
You may create or edit a custom Windows Firewall rule using the Windows Firewall Policy Wizard.
The Custom rule option is designed so that you create a firewall rule based on criteria not covered by the other types of firewall rules. If your rule requires common Windows programs or services, choose the Predefined rule option within the Windows Firewall Policy Wizard to select a rule from a predefined list based on the Windows operating system.
In addition to the Custom rule option, the Windows Firewall Policy Wizard allows you to create a deletion rule that will delete a rule based on the rule name.
Refer to Creating a Windows Firewall Rule for instruction on creating or editing a predefined, custom, or delete firewall rule.
The Add Custom Windows Firewall Rule page contains a number of settings that allow you to create a custom Windows firewall rule to address your Windows Firewall requirements.
The following table describes the fields and options.
|
Options |
Description |
|---|---|
|
Rule name |
The name of the custom rule. |
|
Action |
|
|
Allow the connection (option) |
Allows the connection to be inbound or outbound for communication. |
|
Block the connection (option) |
Blocks the connection to inbound or outbound communication. |
|
Direction |
|
|
Inbound (option) |
Inbound communication connection. |
|
Outbound (option) |
Outbound communication connection. |
|
Profiles (required field) At least one profile type is required. However, you may select multiple profiles as dictated by your Windows Firewall needs. |
|
|
Domain (check box) |
A policy setting that controls the Windows Firewall whenever the computer is connected to domain networks such as a workplace domain. |
|
Private (check box) |
A policy setting that controls the Windows Firewall whenever the computer is connected to trusted networks such as a home or small office network. |
|
Public (check box) |
A policy setting that controls the Windows Firewall whenever the computer is connected to untrusted networks at a public place such as at coffee shops, hotels, or airports. |
|
Protocols and ports |
|
|
Protocol type (drop-down list) |
This is a predefined list of protocols whose network traffic you want to filter with a firewall rule. The selection defines the default settings within the protocol and port area. Refer to Understanding Protocol Types. |
|
Protocol number |
The number of the designated protocol. The Protocol number field is pre-populated with the appropriate number based on the protocol type selected and is read-only. |
|
Local port |
The local port number of the designated protocol. The field is pre-populated with the appropriate port number and is read-only with the exception of the TCP and UDP protocol. If TCP or UDP is required, then multiple port numbers may be entered. You may separate specific ports with commas and/or specify a range of ports by using a dash (-). |
|
Remote port |
The port of the remote used by the designated protocol. The field is pre-populated with the appropriate port number and is read-only with the exception of the TCP and UDP protocol. IfTCP and UDP is required, then multiple port numbers may be entered. You may separate specific ports with commas and/or specify a range of ports by using a dash (-). |
|
Programs and services |
|
|
Program |
To add a program to a firewall rule, you must specify the full path to the executable (.exe) file used by the program. The ellipses button (...) opens the windows explorer browser window to allow a user to locate a file on the local system. Tip: Type Any for all programs. Important: If content is deployed to multiple endpoints, using the browse feature will only work if all of your endpoints contain the program under the same exact path specified. |
|
Services |
A system service that runs within its own unique .exe file and is not hosted by a service container is considered to be a program and can be added. The default is Any. You may type the name of the service. Tip: Type Any for all services. Refer to Microsoft Knowledge Base Article 211362 (http://support.microsoft.com/kb/271362) on how to find short names for installed Windows services. |
|
Scope |
|
|
Local IP address |
The IP address of the network interface on which the connection is made. Type a single IP address, multiple single IP addresses, or an IP address range using a single IP address using CIDR modifiers such as commas, slashes (/), or dashes (-). Examples:
Note:
|
|
Remote IP address |
The IP address of the remote computer on which the connection is made. Type a single IP address, multiple single IP addresses, or an IP address range using a single IP address using CIDR modifiers such as commas, slashes (/), or dashes (-). Examples:
Due to a Microsoft bug, you cannot use CIDR modifiers when entering multiple IP addresses. As a workaround, use two IP address ranges instead of two IP addresses with a CIDR modifier. |
|
Links |
|
|
Save & Create Another |
This link creates the rule and adds it to the Windows Firewall Rules page window. The page refreshes to allow a user to create another rule. |
|
Button |
|
|
Save |
This creates the predefined rule, closes the dialog, and adds the new rule to the Windows Firewall Rules list |
|
Cancel |
This closes the wizard dialog without making any changes |
Predefined Windows Firewall Rule Options
You may create or edit a predefined Windows Firewall rule using the Windows Firewall Policy Wizard.
The Predefined rule option allows you to select programs or services from a predefined list. Most well-known services and programs available on devices running a version of a Windows operating system appears in the list. The Predefined rule option allows you to enable or disable these rules for your selected profile(s).
If your rule requires additional requirements not found in the Predefined rule option, then select the Custom rule option. The Custom rule option is designed so that you may create a firewall rule based on criteria not covered by the other types of firewall rules.
In addition to the Custom rule option, the Windows Firewall Policy Wizard allows you to create a deletion rule that will delete a package based on the rule name.
Refer to Creating a Windows Firewall Rule for instruction on creating or editing a predefined, custom, or delete firewall rule.
The Add Predefined Windows Firewall Rule page contains a number of settings that allow you to create a predefined Windows Firewall rule to address your Windows Firewall requirements.
The following table describes the fields and options.
|
Options |
Description |
|---|---|
|
Rule name (drop-down list) |
The name of the predefined rule. The rules list well known services and programs available on devices running a Windows operating system. |
|
Description |
The description of the policy setting configuration setting. The description information matches the predefined rule name. The field is read-only. |
|
Applicable OS |
The applicable operating system the rule applies to. The field is read-only. |
|
Profiles At least one profile type is required. However, you may select multiple profiles as dictated by your Windows Firewall requirements. |
|
|
Domain (check box) |
A policy setting that controls the Windows Firewall whenever the device is connected to domain networks such as a workplace domain. |
|
Private (check box) |
A policy setting that controls the Windows Firewall whenever the device is connected to trusted networks such as a home or small office network. |
|
Public (check box) |
A policy setting that controls the Windows Firewall whenever the device is connected to untrusted networks at a public place such as at coffee shops, hotels, or airports. |
|
Settings |
|
|
Enable all rules within the predefined group for selected profiles (radio button) |
A policy setting that enables all rules for the predefined group for the profile type(s) selected. |
|
Disable all rules within the predefined group for selected profiles (recommended) (radio button) |
A policy setting that will disable all rules for the predefined group for the profile type(s) selected. |
|
Links |
|
|
Save & Create Another |
This link creates the rule and adds it to the Windows Firewall Rules page window. The page refreshes to allow a user to create another rule. |
|
Button |
|
|
Save |
This creates the predefined rule, closes the dialog, and adds the new rule to the Windows Firewall Rules list. |
|
Cancel |
This closes the wizard dialog without making any changes. |