The Roles Tab
This tab lets you create new roles and manage existing roles. It also lists information about each existing role.
Additionally, you can use this tab to edit roles or remove roles.
About Roles
Roles define the functions and pages that are available to a user and include general access rights, group access rights, and endpoint access rights within the Ivanti Endpoint Security. Roles can be customized and assigned to users.
The Ivanti Endpoint Security contains two types of roles:
System Roles: These roles are included with the default Ivanti Endpoint Security installation. These roles are predefined with access rights appropriate for various user types. System roles cannot be edited or disabled, and by default can access all system groups and endpoints.
Custom Roles These roles are created after Ivanti Endpoint Security installation by users with the Manage Users access right. Custom roles let you grant users unique sets of access rights. Additionally, these roles let you define specific endpoints and groups that can be accessed and managed.
The following table describes role attributes.
|
Role Attribute |
Description |
|---|---|
|
Access Rights |
Define the pages and functions available to the user. |
|
Accessible Groups |
Define the specific endpoint groups accessible to the user. |
|
Accessible Endpoints |
Define the specific endpoints accessible to the user. |
Predefined System Roles
Predefined system roles are the default roles offered by Ivanti Endpoint Security. The commonly used access rights selected for these roles are usually adequate for most networks and their users. Additionally, these roles can access and manage all groups and endpoints.
Predefined system roles have the following benefits:
- These roles types and their commonly used access rights are usually adequate for most networks and their users.
- A user assigned a predefined system role has access to all endpoints and groups.
- Users with the Manage Users access rights can assign predefined system roles to users.
- A predefined system role can be used as a template for creating a custom role. The following table describes each predefined system role.
|
Role |
Icon |
Description |
|---|---|---|
|
Administrator |
|
Users with this role have full access to all Ivanti Endpoint Security pages and functions. The Administrators role allows you to assign endpoints to other roles. Important: At least one user must be assigned the administrator role at all times. |
|
Guest |
|
Users can access pages, but cannot use their functions; this role allows read-only access. |
|
Manager |
|
Users can access pages and functions. |
|
Operator |
|
Users can perform all routine functions (detect, export, and so on). Operators usually perform typical daily functions. |
A user assigned a system role has access to all endpoints and groups.
Custom Roles
Custom roles are created after Ivanti Endpoint Security installation. Custom roles let you grant users unique sets of access rights. Additionally, this role lets you define specific endpoints and groups that can be accessed and managed.
Custom roles have the following benefits:
- You can configure a custom role to restrict access to endpoints and groups.
- You can configure a custom role to restrict access to Ivanti Endpoint Security pages and functions.
- Unlike system roles (which cannot be disabled or deleted), you can disable or delete a custom role at any time.
- When creating new custom roles you may use preexisting roles as templates to aid you.
- Custom roles are denoted by the Wool Hat icon.
Custom roles are created by users with the Manage Users access right.
Defining Access Rights
Access rights are individual privileges that define whether a user can access a system feature. These rights control availability for every Ivanti Endpoint Security page, feature, function, and action. The pages and features available to users are based on the access rights associated with the role assigned to them. The system roles are assigned a default set of access rights. Users inherit the access rights of the role they are assigned.
Access rights begin with read-only access to system pages and permission to export data. At the administrative level, users can be assigned rights to fully manage the various system pages and functions.
New access rights are added when you install new modules.
|
Access Right |
Description |
Access |
|---|---|---|
|
All |
|
|
|
Dashboard |
||
|
View Dashboard |
Access to view the home page dashboard. |
|
|
View Current Status |
Access to view the status of the server. |
|
|
Jobs |
||
|
View Discovery Scan Jobs |
Access to view discovery scan jobs. |
|
|
Create Discovery Scan Jobs |
Access to create and copy discovery scan jobs |
|
|
View Agent Management Jobs |
Access to view agent management jobs. |
|
|
Create Agent Management Jobs |
Access to create and copy agent management jobs. |
|
|
Manage Modules via Jobs |
Access to install or uninstall agent modules using agent management jobs. |
|
|
Manage Jobs |
Cancel, pause, resume, delete or merge all jobs the user has access to. |
|
|
Export Jobs |
Export the jobs list. |
|
|
View AV Centralized Quarantine |
Access to view AntiVirus Centralized Quarantine page |
|
|
Manage AV Centralized Quarantine |
Access to delete and restore files from Centralized Quarantine |
|
|
Endpoints |
||
|
View Endpoints |
Access the manage endpoints all tab. |
|
|
Manage All Tab |
Enable and disable agents, delete endpoints, manage agent modules, and wake endpoints. |
|
|
Export All Tab |
Export the all tab endpoints list. |
|
|
Manage Remotely |
Access the remote management options available. |
|
|
Download Agent Installers |
Access to the Download Agent Installers page. |
|
|
Manage Agent Version |
Access to the Manage Agent Version dialog. |
|
|
Groups |
||
|
View Groups |
Access the groups. |
|
|
Manage Groups |
Add, edit, enable, disable, and delete groups. |
|
|
Export Groups |
Export the groups list. |
|
|
Users |
||
|
View Users |
Access the user groups. |
|
|
Manage Users |
Add or remove users from individual user policies. |
|
|
Export Users |
Export the user groups list. |
|
|
Deployments and Tasks |
||
|
Create Deployments |
Ability to create new deployments. |
|
|
View My Deployments and Tasks |
Access the deployments and tasks that this user has created. |
|
|
View All Deployments |
Access the deployments that all users have created. |
|
|
Manage Deployments and Tasks |
Deploy, enable, disable, abort, and delete deployments and tasks that this user has access to. |
|
|
Export Deployments and Tasks |
Export the deployments and tasks in the list that this user has access to. |
|
|
Agent Policy Sets |
||
|
View All Agent Policy Sets |
Access the agent policy sets. |
|
|
Manage All Agent Policy Sets |
Create, edit and delete agent policy sets. |
|
|
Export All Agent Policy Sets |
Export the agent policy sets list. |
|
|
Reports |
||
|
Reports Administer |
Generate reports regardless of access rights for groups and endpoints. |
|
|
View My Core Reports |
Generate core reports only for those items this user has access to. |
|
|
Export Reports |
Export the generated reports. |
|
|
Configure Enterprise Reporting (ER) |
Configure settings to manage Configure Enterprise Reporting (ER) |
|
|
Users/Roles |
||
|
View Users |
Access the users and roles list view. |
|
|
Manage Users |
Create, delete, enable, and disable users and roles. |
|
|
Export Users |
Export the users and roles list. |
|
|
Change Password |
Ability to change the password for users other than themselves. |
|
|
Manage Server Modules |
||
|
Installation Manager |
Access the Installation Manager to install, update and uninstall server modules. |
|
|
Subscriptions |
||
|
View Subscription |
Access the subscription service information. |
|
|
Manage Subscription |
Edit or update subscription service updates. |
|
|
Export Subscription |
Export the subscription service information. |
|
|
Directory/Computer Synchronization |
||
|
View Directory Sync Schedule |
Access to view the active directory sync schedule page. |
|
|
Manage Directory Sync Schedule |
Create, edit, delete, enable, disable directory syncs. |
|
|
Export Directory Sync Schedule |
Export the directory sync schedule lists. |
|
|
Email notifications |
||
|
View Email Notifications |
Access the email notifications page. |
|
|
Manage Email Notifications |
Create and edit email notifications and settings for core feature. Note: All types of notifications may be deleted with this right. |
|
|
Export Email Notifications |
Export the emails notifications list. |
|
|
Options |
||
|
View Options |
Access to general, agent and deployment default server options. |
|
|
Manage Options |
Set and edit general, agent and deployment default server options. |
|
|
Export Options |
Export the options list. |
|
|
Technical Support |
||
|
View Technical Support |
Access the technical product support information. |
|
|
Export Technical Support |
Export the technical product support information. |
|
|
Licenses |
||
|
View Licenses |
Access the product licenses. |
|
|
Manage Licenses |
Update product licenses. |
|
|
Export Licenses |
Export the product license information. |
|
Defining Accessible Groups
Accessible groups are specific groups of endpoints that a particular role can access and manage. Use this feature for granularity when assigning roles to users.
Accessible groups are only applicable to custom user roles.
The Accessible Groups feature is disabled when working with a predefined system role. System roles can access all groups and endpoints within the system.
This feature allows you to restrict a user to specified groups. For example, a user assigned the access right to manage deployments can be limited to managing deployments for select groups.
The Accessible Groups feature is defined on the Groups tab in both the Create Role dialog and the Edit Role dialog.
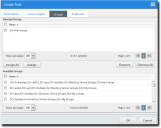
The Groups tab contains the following lists, which are used to control what groups are associated with a particular role:
|
List |
Description |
|---|---|
|
Selected Groups |
Lists the groups assigned to the role. |
|
Available Groups |
Lists the available groups that can be assigned to the role. |
Defining Accessible Endpoints
Accessible Endpoints are specific endpoints that a particular role can access and manage. This feature is similar to the Accessible Groups feature; it allows for granularity when assigning roles to system users.
Accessible endpoints are only applicable to custom user roles.
The Accessible Endpoints feature is disabled when working with predefined system roles. System roles can access all groups and endpoints within the system.
As mentioned, this feature lets you define specific endpoints that users associated with the role can access and manage. For example, you can limit a user assigned the Manage Endpoints access right to management of a single endpoint.
This feature is are defined on the Endpoints tab in both the Create Role dialog and the Edit Role dialog.
The Endpoints tab contains the following lists, which are used to control which endpoints are associated with a role:
|
List |
Description |
|---|---|
|
Selected Endpoints |
Lists the endpoints assigned to the role. |
|
Available Endpoints |
Lists the available endpoints that can be assigned to the role. |
The Roles Tab Toolbar
This toolbar contains buttons that let you create and manage user roles. The following table describes the function of each Roles tab toolbar button.
|
Button Name |
Function |
|---|---|
|
Enable |
Enables the selected disabled custom role. For additional information, refer to Enabling User Roles. |
|
Disable |
Disables the selected custom role. For additional information, refer to Disabling User RolesDisabling User Roles. |
|
Delete |
Deletes the selected custom role. For additional information, refer to Deleting User RolesDeleting User Roles. |
|
Create... |
Creates a new user role. For additional information, refer to Creating User Roles. |
|
Export |
Exports the page data to a comma-separated value (.csv) file. For additional information, refer to Exporting Data. Important: The Enhanced Security Configuration feature for Internet Explorer suppresses export functionality and must be disabled to export data successfully. Pop-up blockers in Internet Explorer or other supported browsers may also suppress export functionality and should be disabled. |
|
Options (menu) |
Opens the Options menu. For additional information, refer to The Options Menu. |
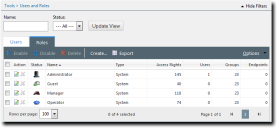
The Roles Tab List
This list displays all user roles that exist within Ivanti Endpoint Security. Use the action icons to manage roles. Additionally, this list can be filtered to display only specified roles.
The following table describes each Roles tab list column.
|
Column |
Description |
|---|---|
|
Action |
Contains Edit and Delete icons. Use these icons to edit or delete the associated role. For addition information, refer to one of the following topics: |
|
Status |
Contains an icon that indicates the type of role. For additional information, refer to one of the following topics: |
|
Name |
The name of the user role. |
|
Type |
The type of user role (System or Custom). |
|
Access Rights |
The number of access rights assigned to the role. |
|
Users |
The number of users assigned to the role. |
|
Groups |
The number of accessible groups assigned to the role. |
|
Endpoints |
The number of accessible endpoints assigned to the role. |