Distributed Environment Management
Security Controls provides a number of features to allow for management of an environment.
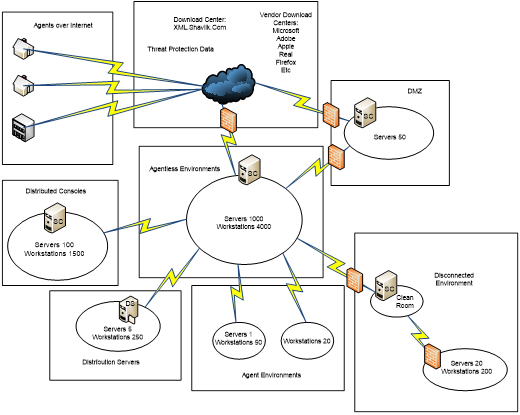
Agentless Environments
Security Controls can be rapidly configured to support large numbers of machines agentlessly. By creating a machine group from hostnames, domains, IP addresses/ranges or OUs, you can identify machines you want to scan and specify administrative credentials for the machines.
Distributed Consoles
Multiple Security Controls consoles can be configured to distribute workload across large numbers of machines and across WANs to distribute management of the enterprise. Data can then be rolled up to a central console for reporting purposes.
Distribution Servers
To reduce WAN traffic a distribution server can be setup at a remote site to distribute data, engines, patches, and service packs to a remote site, reducing data transfer.
Disconnected Environments
Security Controls can be configured to pull data, engines, patches, and service packs from an internal source.
- For partially disconnected environments you can use these features to download from an Internet-connected machine. You then move the files to a clean room and from there into the disconnected environment.
- In a fully disconnected environment the connected console would download everything. You then use a manual or “sneaker net” process to move the files from one console to another.
Agents
Security Controls also includes agents. With the agent, administrators are able to work around many obstacles and reach machines where agentless scans may not gain total coverage. Low bandwidth WAN links, laptops that typically leave the environment, and secure environments such as DMZs are cases where an agent may be ideal.
Demilitarized Zone (DMZ)
Security Controls can be configured in a number of ways to support demilitarized zones (DMZs). The option to use agentless scans by IP address or IP ranges allows administrators to work around name resolution if it is not available in the DMZ. A distributed console can be configured in the DMZ if IP rules on the firewall are not acceptable to support agentless scanning from the network into the DMZ.
Related Topics
- Console Software and Hardware Recommendations
- Port Requirements and Firewall Configuration
- Agentless Patch Management
- Best Approach for Applying Patches in an Agentless Environment
- Automating Patch Management in an Agentless Environment
- Agent-Based Patch Management
- Agent Rollout Options
- Installing and Supporting Agents on Internet-Based Machines
- Agent-Based Product Level and Patch Deployment Process
- Guide to Surviving Patch Tuesday
- Microsoft SQL Server Database Maintenance
- Performing Patching in a Disconnected Environment