AppTunnel configuration troubleshooting display in Mobile@Work
Mobile@Work displays AppTunnel configuration information for the app that it received from MobileIron Core. This information helps troubleshoot your AppTunnel configuration when an app is not successfully tunneling URL requests to its app server. Check the display’s fields to make sure that your AppTunnel configuration has been sent to the device and is what you intended.
Some highlights of the displayed AppTunnel configuration are:
- Whether Mobile@Work has received the AppTunnel configuration from Core.
- Whether the client certificate, identifying the device user to the Standalone Sentry, has expired.
- The list of AppTunnel rules that indicate which URL requests should be tunneled.
Navigating to the AppTunnel configuration troubleshooting display
Procedure
| 1. | Open Mobile@Work on the device. |
| 2. | Tap Settings. |
| 3. | Tap Secure Apps. (Screenshots from Mobile@Work 9.1) |
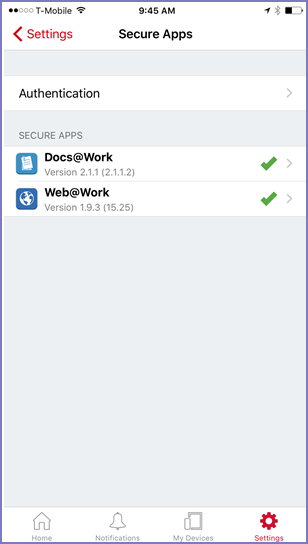
| 4. | Tap the secure app you are interested in. |
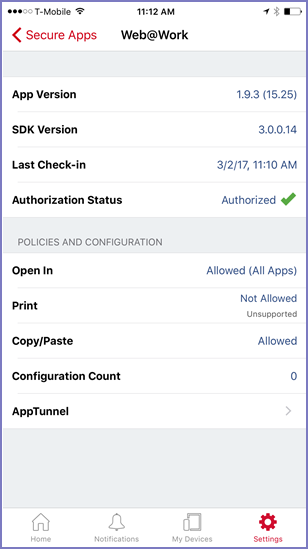
| 5. | Tap AppTunnel. |
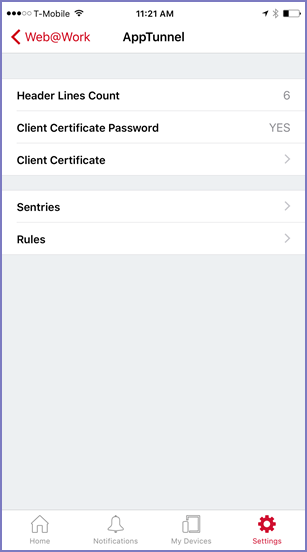
If AppTunnel is None, no AppTunnel configuration is available for the app on Mobile@Work. See AppTunnel configuration troubleshooting checklist.
Troubleshooting with the AppTunnel configuration display fields
Use the AppTunnel configuration display if URL requests that you configured for AppTunnel are not being tunneled. Check the display’s fields to make sure that your AppTunnel configuration has been sent to the device and is what you intended.
Some screenshots are from Mobile@Work 9.1.
Figure 1. AppTunnel display
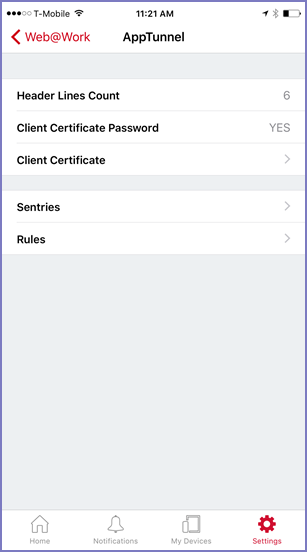
|
Field name |
Description |
Troubleshooting actions |
|||||||||||||||
|
Header Line Count |
HTTP/S request header information for Sentry |
If the value is zero, the device is not receiving the AppTunnel information from MobileIron Core. Verify your AppTunnel configuration as specified in AppTunnel configuration troubleshooting checklist. If the value is still zero, contact Ivanti Technical Support. |
|||||||||||||||
|
Client Certificate Password |
Whether the client certificate that identifies the device user to Sentry is password-enabled. |
When using a SCEP certificate, the value should be YES. |
|||||||||||||||
|
Client Certificate |
Whether a valid client identity is available. This client identity is used to authenticate the app to the Sentry. |
Tap to see the identity’s certificate information, including whether the certificate has expired. If the value is None, check the AppConnect app configuration for the app. Make sure you specified an identity certificate. In the Admin Portal for MobileIron Core:
Make sure you have applied the appropriate labels to the AppConnect app configuration. |
|||||||||||||||
|
Sentries |
The Sentries that are configured for AppTunnel for this app. |
Tap to see the list of Sentries. Make sure they are what you expect this app to use for AppTunnel. |
|||||||||||||||
|
Rules |
The AppTunnel rules configured on the app’s AppConnect app configuration. |
If None, you have not configured AppTunnel rules on the AppConnect app configuration. In the Admin Portal for MobileIron Core:
Make sure you have applied the appropriate labels to the AppConnect app configuration. |
Client Certificate display
Check the client certificate fields, including whether the certificate has expired.
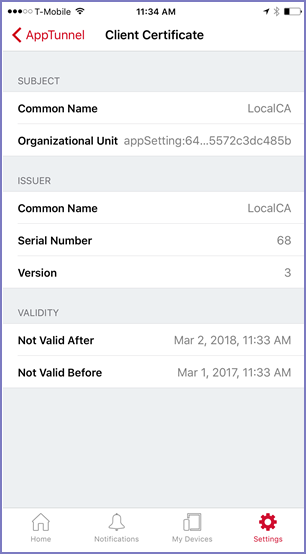
If necessary, tap on a field to view the entire string.
|
Field name |
Description |
Troubleshooting actions |
|||||||||
|
Subject |
You can compare the certificate values to the values on the Core Admin Portal:
•Specifying a trusted root certificate in the Standalone Sentry •Specifying a valid client certificate in the AppConnect app configuration |
||||||||||
|
Common Name |
|
||||||||||
|
Organizational Unit |
|
||||||||||
|
Issuer |
|
||||||||||
|
Common Name |
|
||||||||||
|
Serial Number |
|
||||||||||
|
Version |
|
||||||||||
|
Validity |
|||||||||||
|
Not Valid After |
Expiration date |
Make sure that the certificate has not expired. |
|||||||||
|
Not Valid Before |
Initial date |
Make sure that the certificate is valid. |
|||||||||
Specifying a trusted root certificate in the Standalone Sentry
The client identity is issued from a Trusted Root Certificate.The Standalone Sentry must be configured with the Trusted Root Certificate for device authentication to the Sentry.
To configure Standalone Sentry with the Trusted Root Certificate, in the Admin Portal for MobileIron Core:
| 1. | Go to Services > Sentry. |
| 2. | Select the Standalone Sentry. |
| 3. | Click Edit. |
| 4. | Make sure Enable AppTunnel is selected. |
| 5. | In the Device Authentication Configuration section, select Identity Certificate. |
| 6. | Click Choose File to navigate to and select the Trusted Root Certificate. |
| 7. | Click Upload Certificate. |
| 8. | Click View Certificate to verify the certificate. |
| 9. | Click Save. |
•“Device and server authentication support for Standalone Sentry” in the Sentry Guide for Core.
Specifying a valid client certificate in the AppConnect app configuration
If the client certificate is not valid, specify a valid client identity certificate in the AppConnect app configuration.
In the Admin Portal for MobileIron Core:
| 1. | Go to Policies & Configs > Configurations. |
| 2. | Select the AppConnect app configuration for the app (Setting Type is APPCONFIG) and Click Edit. |
| 3. | If you have not created an AppConnect app configuration, select Add New > AppConnect > Configuration. |
| 4. | In the AppTunnel Rules section, in the Identity Certificate field, specify a valid client certificate. |
| 5. | Click Save. |
Make sure you have applied the appropriate labels to the AppConnect app configuration.
Rules display
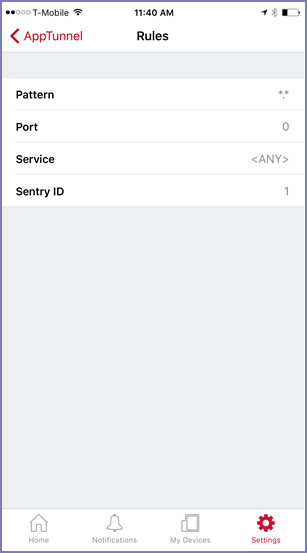
This display shows each AppTunnel rule configured on the app’s AppConnect app configuration. The following table shows the display fields for each rule and the corresponding fields in the AppConnect app configuration:
|
Field name |
Description |
Troubleshooting actions |
|||||||||
|
Pattern |
Corresponds to the URL Wildcard field of the AppConnect app configuration.
|
Make sure the field contains the hostname that the app is trying to access. The pattern can contain the wildcard *. The app data is tunneled only if the hostname and port number in the app’s request matches the Pattern field and Port field. Exception: For iOS apps using AppConnect releases prior to AppConnect for iOS SDK 2.5 and AppConnect for iOS Wrapper 2.7, only the request’s hostname, not the port number, determines whether the app data is tunneled. |
|||||||||
|
Port |
Corresponds to the Port field of the AppConnect app configuration. |
Make sure the field contains the port number that the app is trying to access. The app data is tunneled only if the hostname and port number in the app’s request matches the Pattern field and Port field. Exception: For iOS apps using AppConnect releases prior to AppConnect for iOS SDK 2.5 and AppConnect for iOS Wrapper 2.7, only the request’s hostname, not the port number, determines whether the app data is tunneled. |
|||||||||
|
Service |
Corresponds to the Service field of the AppConnect app configuration. The value specifies an AppTunnel service configured in the AppTunnel Configuration section of the specified Sentry. |
Make sure the service corresponds to an AppTunnel service on the Sentry that accesses the intended app server. In the Admin Portal for MobileIron Core:
|
|||||||||
|
Sentry ID |
The MobileIron Core internal ID for the Sentry. |
Only for use by Ivanti Technical Support. |
Sentry display
This display lists the Sentries that are configured for AppTunnel for this app. Make sure they are what you expect.
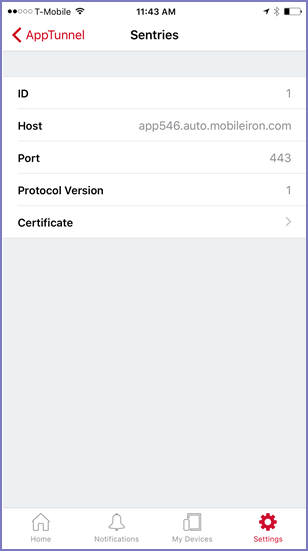
|
Field name |
Description |
Troubleshooting actions |
|||||||||
|
ID |
The MobileIron Core internal ID for the Sentry. |
For use only by Ivanti Technical Support. |
|||||||||
|
Host |
Sentry host name |
Make sure this Sentry is one you intended for AppTunnel for this app. |
|||||||||
|
Port |
Port opened to MobileIron Core. |
|
|||||||||
|
Protocol Version |
Protocol version between the Sentry and MobileIron Core |
For use only by Ivanti Technical Support. |
|||||||||
|
Certificate |
This is the certificate that the AppConnect Library in the app uses to know that the Sentry used for AppTunnel is a trusted server. A valid pinned Sentry certificate must be available for tunneling. |
Tap to see certificate information, including whether the certificate has expired. To view the Sentry certificate in the Admin Portal for MobileIron Core.
|
“Managing certificates for Standalone Sentry” in the Sentry Guide for Core.
Sentry Certificate display
Make sure this is the certificate you intended for devices to use to know that the Sentry used for AppTunnel is a trusted server. Check the certificate fields, including whether the certificate has expired. You sometimes have to scroll down the screen to see all the fields.
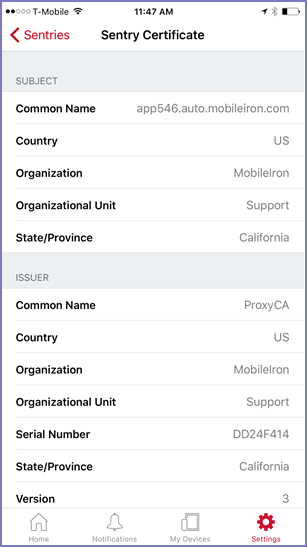
Note the following:
•If necessary, tap on a field to view the entire string.
•Scroll down to see additional fields.
Table 1. Sentry certificate display fields and troubleshooting actions
|
Field name |
Description |
Troubleshooting actions |
|||||||||
|
Subject |
You can compare the certificate values to the values on the Core Admin Portal:
|
||||||||||
|
Common Name |
|
||||||||||
|
Country |
|
||||||||||
|
Email Address |
|
||||||||||
|
Organization |
|
||||||||||
|
Organizational Unit |
|
||||||||||
|
State/Province |
|
||||||||||
|
Issuer |
|||||||||||
|
Common Name |
|
||||||||||
|
Country |
|
||||||||||
|
Organization |
|
||||||||||
|
Organizational Unit |
|
||||||||||
|
Serial Number |
|
||||||||||
|
State/Province |
|
||||||||||
|
Version |
|
||||||||||
|
Validity |
|||||||||||
|
Not Valid After |
Expiration date |
Make sure that the certificate has not expired. |
|||||||||
|
Not Valid Before |
Initial date |
Make sure that the certificate is valid. |
|||||||||
Uploading a valid Sentry certificate to Standalone Sentry
If the certificate is not valid, upload a valid certificate.
In the Admin Portal for MobileIron Core:
| 1. | Go to Services > Sentry. |
| 2. | Find the line for the appropriate Sentry. |
| 3. | Click Manage Certificate. |
| 4. | Select Upload Certificate. |
| 5. | Click Browse. |
| 6. | Select the certificate and click Upload Certificate. |
| 7. | Click View Certificate to verify the certificate. |
“Standalone Sentry certificate” in the Sentry Guide for Core.
AppTunnel configuration troubleshooting checklist
If an app is not successfully tunneling to its app server, check the following in the MobileIron Core Admin Portal:
|
Admin Portal location |
Troubleshooting actions |
||||||||||||
|
Settings > Additional Products > Licensed Products |
Make sure you have enabled the appropriate products. Make sure you have selected App Tunnel for Third-party and In-house apps, if you are using AppTunnel for any app besides Docs@Work. |
||||||||||||
|
Policies & Configs > Policies AppConnect global policy |
Check the AppConnect global policy configuration:
|
||||||||||||
|
Services > Sentry |
Make sure the Standalone Sentry is configured with a certificate that devices use to know that the Sentry used for AppTunnel is a trusted server. To view the Sentry certificate in the Admin Portal for MobileIron Core.
|
||||||||||||
|
Services > Sentry |
Make sure the Standalone Sentry is configured for AppTunnel for the app:
|
||||||||||||
|
Policies & Configs > Configurations AppConnect container policy |
Check the AppConnect container policy for the app. Make sure it is applied to a label belonging to the device. You do not need an AppConnect container policy if the AppConnect global policy selects Authorize for Apps without an AppConnect container policy. |
||||||||||||
|
Policies & Configs > Configurations AppConnect app configuration |
Check the AppConnect app configuration for the app:
|
- Enabling AppTunnel
- AppConnect global policy
- Configuring an AppTunnel service
- Configuring the Open With Secure Email App option
- AppConnect container policies
- AppConnect app configuration
- “Standalone Sentry certificate” and “Device and server authentication” in the Sentry Guide for Core