Creating compliance policy rules and groups
Before you begin
Be sure you have completed Setting up the MTD threat management console.
Threat types
Within Ivanti Mobile Threat Defense, there are three threat types. Within each type there are severity levels: Critical, Elevated, Normal, and Low. Altogether you have:
- Device – Critical, Elevated, Normal, and Low severity levels
- Network – Critical, Elevated, Normal, and Low severity levels
- App – Critical, Elevated, Normal, and Low severity levels
For each threat type, you create compliance policy rules based on the threat severity. As a best practice, you should have the following compliance policy rules:
-
For Low and Normal threat types – use Send Alert
-
For Elevated threat type – use Block Access and/or Quarantine
-
For Critical threat type – use Quarantine or Tier Compliance:
- Block
- Notification
- Quarantine
- Tiered Compliance 23 hours
- Tiered Compliance 4 hours
Example of threat type implementation: user connects to hotel Wi-Fi
- Tier 1 - Notification - MTD alerts the device user "You just connected to unsecure Wi-Fi"
- Tier 2 - After 4 hours, MTD blocks the user's access to email and AppConnect apps.
- Tier 3 - MTD Quarantines and blocks the Wi-Fi; removes user's access to the company network.
Creating compliance policy rules
You will need to create compliance policy rules based on threat severity level.
Procedure
- From the Ivanti EPMM Admin Portal, select Policies & Configs > Compliance Policies.
- Click the Compliance Policy Rule tab and then click Add+.
- Enter "Block" in the Rule Name field.
- Set the Status to Enabled.
- (Optional) Enter a description of the rule, for example, "MTD Block Rule."
-
In the Condition expression field, enter this expression:
(("common.platform" = "Android" OR "common.platform" = "iOS") AND "common.retired" = false) AND "common.retired" = false
- In the Compliance Actions field, select from the drop-down: Block Email, AppConnect apps, and Send Alert.
- (Optional) In the Message field, enter text for alerts generated by violations of the policy rule.
- Click Save. The Block rule displays in the Compliance Policy Rule tab.
-
Repeat steps 2-9 using the parameters below for creating additional compliance policy rules.
Table 6. Create additional compliance policy rules Rule Name field Condition expression field Compliance Actions field Notification
(("common.platform" = "Android" OR "common.platform" = "iOS") AND "common.retired" = false) AND "common.retired" = false
Send Alert
Quarantine
(("common.platform" = "Android" OR "common.platform" = "iOS") AND "common.retired" = false) AND "common.retired" = false
Quarantine
Tiered Compliance23hours
(("common.platform" = "Android" OR "common.platform" = "iOS") AND "common.retired" = false) AND "common.retired" = false
Tiered Compliance 23 hours
Tiered Compliance4hours
(("common.platform" = "Android" OR "common.platform" = "iOS") AND "common.retired" = false) AND "common.retired" = false
Tiered Compliance 4 hours
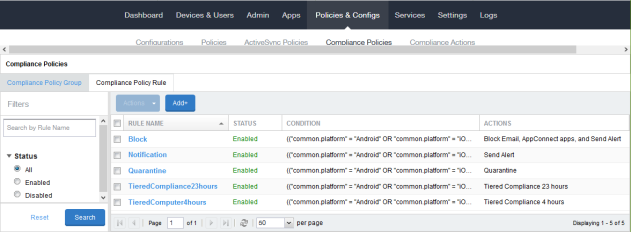
When you have finished, you should have five compliance policy rules displayed in the Compliance Policy Rule tab.
Figure 1. Compliance Policy Rule examples
Creating compliance policy groups
Compliance policy groups are used to apply the group's rules to devices matching the label.
Procedure
- Select Policies & Configs > Compliance Policies.
- Click on the Compliance Policy Group tab and then click on Add+.
- Enter "MTDBlock" into the Group Name field.
- Keep the default Status of Enabled.
- (Optional) Enter a description of the group name, for example, "MTDBlock."
- In the Available Rules field, move the "Block" rule to the Selected Rules section. (Action is "Block Email, AppConnect apps, and Send Alert.")
- Click Save. The MTDBlock group displays in the Compliance Policy Group tab.
-
Repeat steps 2-7 using the parameters below for creating additional compliance policy groups.
Table 7. Compliance policy rule group examples Group Name field Status Rule Name Action Name MTDNotification
Enabled
Notification
Send Alert
MTDQuarantine
Enabled
Quarantine
Quarantine
MTDTiered23hours
Enabled
TieredCompliance23hours
Tiered Compliance 23 hours
MTDTiered4hours
Enabled
TieredCompliance4hours
Tiered Compliance 4 hours
-
Apply labels. Every rule group (MTDBlock, MTDNotification, etc.) needs to be assigned to the appropriate label (MTD-Block, MTD-Notification, etc.)
When you have finished, you should have five compliance policy rules displayed in the Compliance Policy Group tab.