Deployments
This topic describes the deployment scenarios of the Guest access solution.
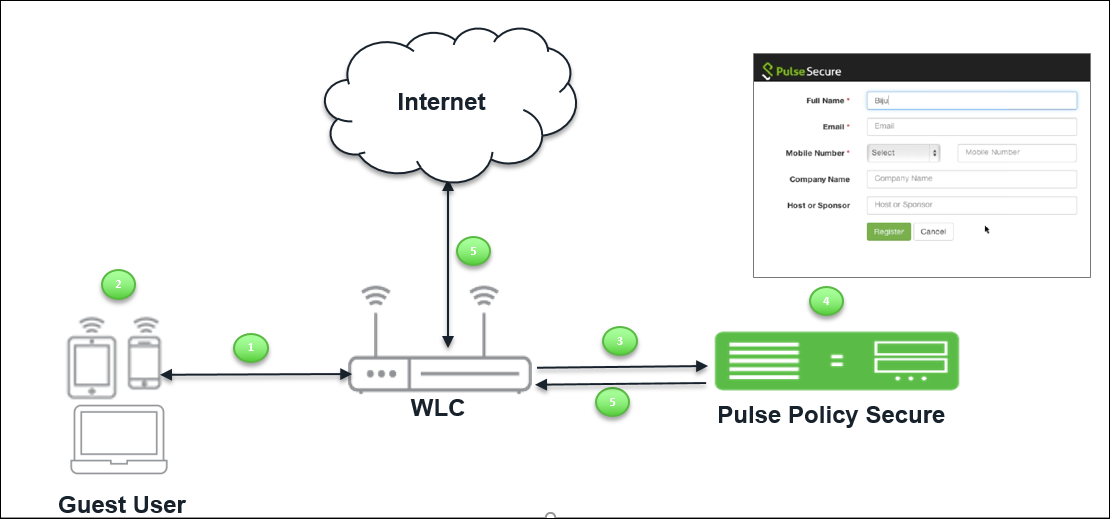
Guest Access using WLC
The guest access solution for wireless network can be deployed with leading Wireless LAN controllers. You can deploy wireless network with WLCs and wireless network for guests. The guest authentication is done with external authentication server and IPS server can be used as an external authentication server.
The assumption for this deployment the user has already deployed wireless network for guest using WLC and would like to have centralized authentication server. When wireless network is built with multiple vendors WLCs then it further becomes useful to have centralized authentication server.
The user flow is explained below:
- Guest user comes on-premises and connects to guest SSID.
- Guest user opens a browser to access an internet resource.
- The user is redirected to IPS guest login page.
- Guest user clicks the self-registration link from the guest login page and completes the registration process.
- If the Administrator has configured Host Checker policy then IPS evaluates the Host Checker results.
- Pre authentication – Host Checker policies are evaluated first and then user is prompted for credentials. For configuration details, see User Realms
- Post authentication – User credentials are validated first and then the Host Checker policies are evaluated. For configuration details, see User Roles
- Guest user logins with guest user credentials. IPS validates the credentials and based on the result WLC redirects the guest user to the resource requested.
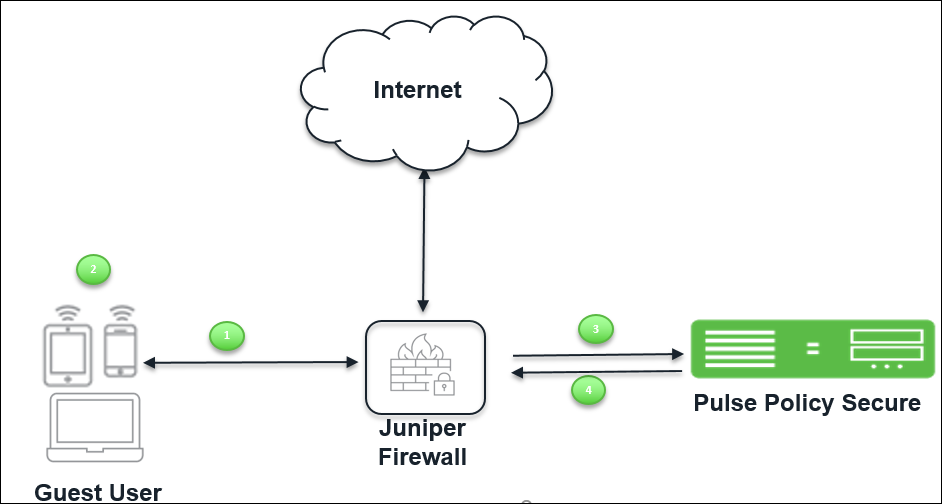
Guest Access using EX switch/SRX Firewall
When a IPS and an EX Series switch/SRX firewall is deployed, users must first sign into IPS for authentication before they can access a protected resource behind the EX Series switch/SRX firewall.
To facilitate sign-in, you can configure a redirect policy on the EX Series switch/SRX firewall to automatically redirect HTTP traffic destined for protected resources to IPS. When the sign-in page for the IPS is displayed, the user signs in, and access is granted to internet. These user accounts can be created by Guest User Account Manager.
The user flow is explained below:
- Guest user comes on-premises and tries to connect to internet.
- Guest user opens a browser to access an internet resource.
- The Guest user is redirected to IPS login page.
- If the Admin has configured Host Checker restrictions on the Guest role/realm then the Guest user is provided access only after Host Checker policies are evaluated.
- The Admin can configure the Host Checker in two ways:
- Pre-Authentication (Host Checker restriction on guest realm)– The Host Checker policies are evaluated first and then user is prompted for credentials.
- Post-Authentication (Host Checker restriction on guest role) – The user credentials are validated first and then the host checker policies are evaluated.
- The Guest user logins with the credentials provided by the guest Admin (GUAM).
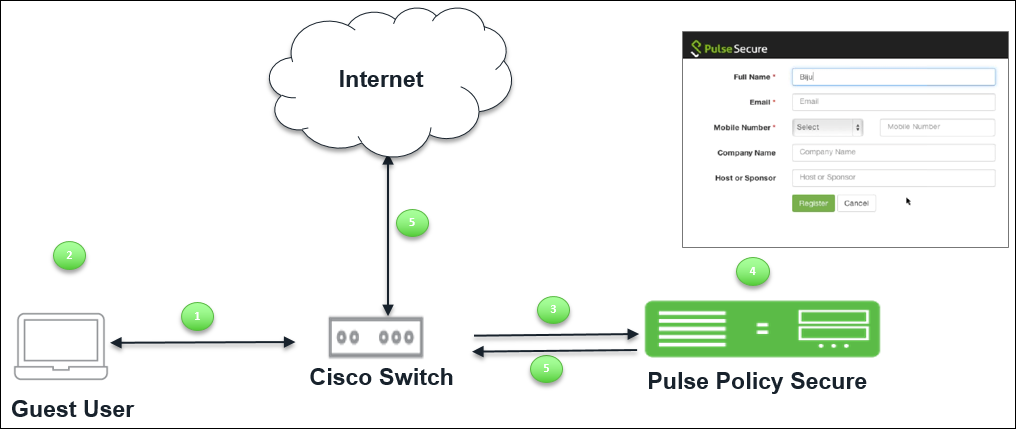
Guest Access using Cisco Switch
The guest access feature is supported for wired guest endpoints with Cisco switches. To facilitate sign-in, you can configure a redirect policy on the Cisco switch to automatically redirect HTTP traffic destined for protected resources throughIPS . When the sign-in page for the IPS is displayed, the user signs in, and access is granted to internet.
The user flow is explained below:
- Guest user comes on-premises and connects to LAN.
- Guest user opens a browser to access an internet resource.
- The user is redirected to IPS guest login page.
- The Guest user self registers on IPS guest portal and receives the credentials over the email/SMS or on the UI.
- If the Administrator has configured Host Checker policy then IPS evaluates the Host Checker results.
- Pre authentication – Host Checker policies are evaluated first and then user is prompted for credentials. For configuration details, see User Realms.
- Post authentication – User credentials are validated first and then the Host Checker policies are evaluated. For configuration details, see User Roles.
- The guest user gets authenticated and gets redirected to the requested internet resource.
The configuration details are covered in Configuring IPS for Guest Wired Authentication using Cisco Switch.