Deploying Ivanti Policy Secure on Azure using Azure Portal
Before proceeding with the deployment, refer the following sections:
- Upload Ivanti Policy Secure Virtual Appliance Image to Azure Web Portal
- Upload Azure Resource Manager Template to Azure Account
Ivanti Policy Secure can be deployed on:
Deploying Ivanti Policy Secure on New Virtual Network
This section describes deployment with three NIC cards and two NIC cards.
Deployment on VM with Three NIC Cards
To deploy PPS on Azure using the Azure portal, do the following:
-
Select the template file created in section ‘Upload Azure Resource Manager Template to Azure account’ and click Save.
Before proceeding with deployment, ensure that the attribute “accept-license-agreement” in
pulse-config is set to “y”.
-
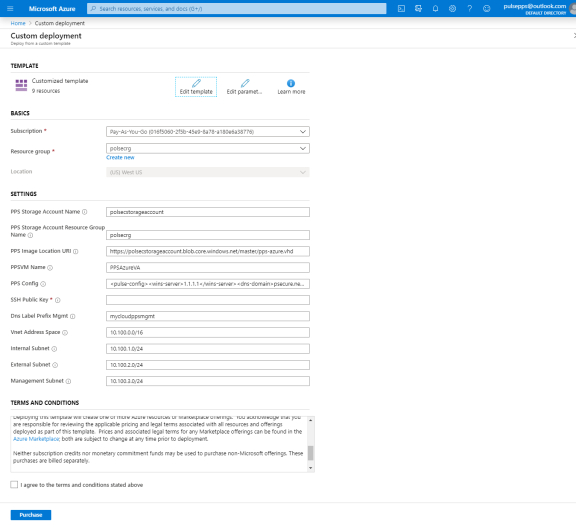
Fill or modify the following parameters:
-
Resource group: Specify the resource group name in which Ivanti Policy Secure needs to be deployed
-
Location: Region where resource group needs to be created
-
PPS Storage Account Name: Storage account name where the Ivanti Policy Secure Virtual Appliance image is available
-
PPS Storage Account Resource Group: Resource group of where the Ivanti Policy Secure Virtual Appliance image is copied
-
PPS Image Location URI: URI to Ivanti Policy Secure Virtual Appliance Image
-
PPSVM Name: Name of the Ivanti Policy Secure Virtual instance
-
PPS Config: Provisioning parameters in an XML format. Refer the section ‘Ivanti Policy Secure Provisioning Parameters’
-
SSH Public Key: This key is used to access Ivanti Policy Secure via SSH. The SSH keys are generated using ssh-keygen on Linux and OS X, or PuTTyGen on Windows. For details about generating the SSH key pairs, refer:
For Windows: https://docs.microsoft.com/en-us/azure/virtual-machines/linux/ssh-from-windows
For MacOS and Linux: https://docs.microsoft.com/en-us/azure/virtual-machines/linux/mac-create-ssh-keys
-
DNS Label Prefix Mgmt: Prefix for the management interface DNS label
-
Vnet Address Space: Virtual network address space
-
Internal Subnet: Subnet from which Ivanti Policy Secure internal interface needs to lease IP
-
External Subnet: Subnet from which Ivanti Policy Secure external interface needs to lease IP
-
Management Subnet: Subnet from which Ivanti Policy Secure management interface needs to lease IP
-
-
Agree to the Azure licensing terms and click Purchase.
-
Watch for the deployment succeeded message after 3 to 5 minutes.
-
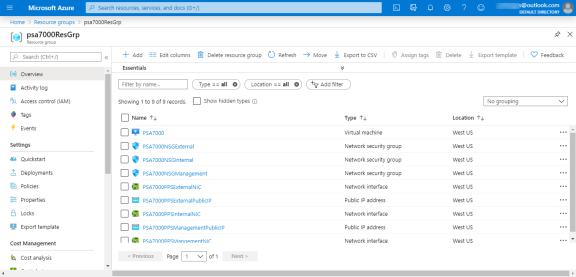
Go to the resource group in which the Ivanti Policy Secure Virtual Appliance was deployed to see the resources created.
-
Navigate to the resource group and click PPS Management Public IP. Make a note of the Ivanti Policy Secure Management Public IP and DNS name (FQDN) to access Ivanti Policy Secure for admin page.
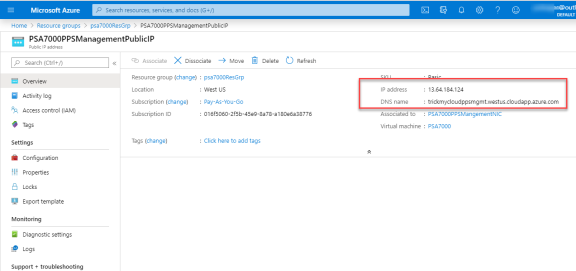
Azure allows static as well as dynamic assignment of IP addresses to the network interfaces. The mode of IP assignment (static/dynamic) can be mentioned in the Azure Resource Manage template file. The current JSON template uses the dynamic method of allotting IP addresses to the network interfaces.
Deployment on VM with Two NIC Cards
To deploy Ivanti Policy Secure on Azure using the Azure portal, do the following:
-
1.Select the template file created in section ‘Upload Azure Resource Manager Template to Azure account’ and click Deploy.
Before proceeding with deployment, ensure that the attribute “accept-license-agreement” in
pulse-config is set to “y”.
-
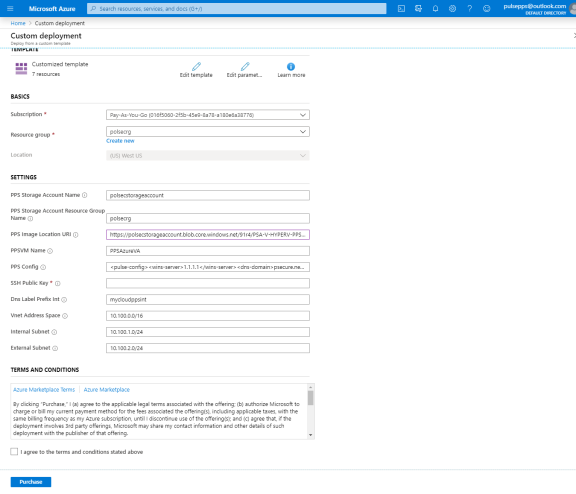
Fill or modify the following parameters:
-
Resource group: Specify the resource group name in which Ivanti Policy Secure needs to be deployed
-
Location: Region where resource group needs to be created
-
PPS Storage Account Name: Storage account name where the Ivanti Policy Secure Virtual Appliance image is available
-
PPS Storage Account Resource Group: Resource group of where the Ivanti Policy Secure Virtual Appliance image is copied
-
PPS Image Location URI: URI to Ivanti Policy Secure Virtual Appliance Image
-
PPSVM Name: Name of the Ivanti Policy Secure Virtual instance
-
PPS Config: Provisioning parameters in an XML format.
-
SSH Public Key: This key is used to access Ivanti Policy Secure via SSH. The SSH keys are generated using ssh-keygen on Linux and OS X, or PuTTyGen on Windows. For details about generating the SSH key pairs, refer:
For Windows: https://docs.microsoft.com/en-us/azure/virtual-machines/linux/ssh-from-windows
For MacOS and Linux: https://docs.microsoft.com/en-us/azure/virtual-machines/linux/mac-create-ssh-keys
-
DNS Label Prefix Int: Prefix for the internal interface DNS label
-
Vnet Address Space: Virtual network address space
-
Internal Subnet: Subnet from which Ivanti Policy Secure internal interface needs to lease IP
-
External Subnet: Subnet from which Ivanti Policy Secure external interface needs to lease IP
-
-
Agree to the Azure licensing terms and click Purchase.
-
Watch for the deployment succeeded message after 3 to 5 minutes.
-
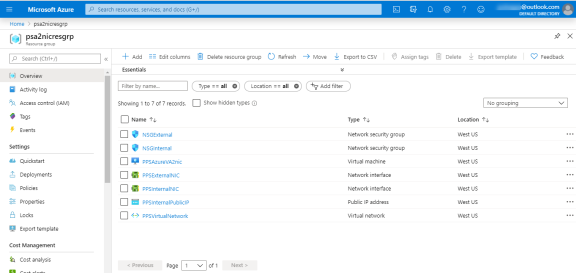
Go to the resource group in which the Ivanti Policy Secure Virtual Appliance was deployed to see the resources created.
-
Click PPS Internal Public IP and note down the PPS Internal Public IP and DNS name (FQDN) to access Ivanti Policy Secure for end user page.
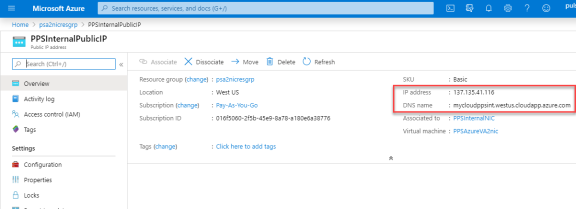
Azure allows static as well as dynamic assignment of IP addresses to the network interfaces. The mode of IP assignment (static/dynamic) can be mentioned in the Azure Resource Manage template file. The current JSON template uses the dynamic method of allotting IP addresses to the network interfaces.
Deploying Ivanti Policy Secure on an Existing Virtual Network
This section describes deployment with three NIC cards and two NIC cards.
Deployment on VM with Three NIC Cards
To deploy Ivanti Policy Secure on Azure using the Azure portal, do the following:
-
1.Select the template file “pulsesecure-pps-3-nics-existing-vnet” created in the section ‘Upload Azure Resource Manager Template to Azure account’ and click Save.
Before proceeding with deployment, ensure that the attribute “accept-license-agreement” in
pulse-config is set to “y”.
-
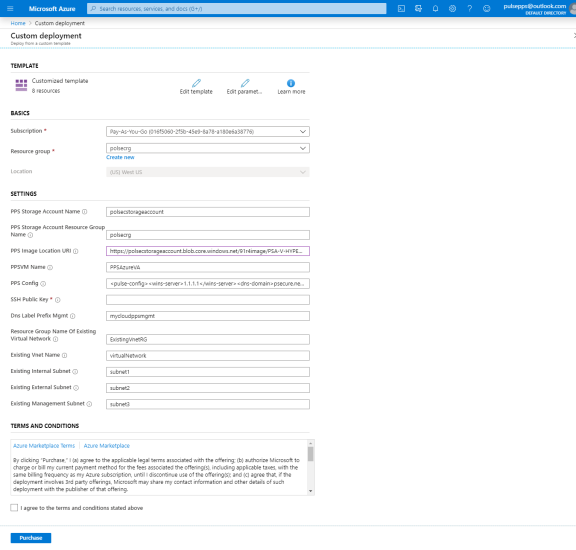
Fill or modify the following parameters:
-
Resource group: Specify the resource group name in which Ivanti Policy Secure needs to be deployed
-
Location: Region where resource group needs to be created
-
Ivanti Policy Secure Storage Account Name: Storage account name where the Ivanti Policy Secure Virtual Appliance image is available
-
Ivanti Policy Secure Storage Account Resource Group: Resource group of where the Ivanti Policy Secure Virtual Appliance image is copied
-
Ivanti Policy Secure Image Location URI: URI to Ivanti Policy Secure Virtual Appliance Image
-
Ivanti Policy Secure VM Name: Name of the Ivanti Policy Secure Virtual instance
-
Ivanti Policy Secure Config: Provisioning parameters in XML format. Refer Ivanti Policy Secure ProvisioningParameters
-
SSH Public Key: This key is used to access Ivanti Policy Secure via SSH. The SSH keys are generated using ssh-keygen on Linux and OS X, or PuTTyGen on Windows. For details about generating the SSH key pairs, refer:
For Windows: https://docs.microsoft.com/en-us/azure/virtual-machines/linux/ssh-from-windows
For MacOS and Linux: https://docs.microsoft.com/en-us/azure/virtual-machines/linux/mac-create-ssh-keys
-
DNS Label Prefix Mgmt: Prefix for the management interface DNS label
-
Resource Group Name of Existing Virtual Network: Resource Group name of the Virtual network
-
Existing Vnet Name: Virtual network name
-
Existing Internal Subnet: Subnet from which the Ivanti Policy Secure internal interface needs to lease IP
-
Existing External Subnet: Subnet from which the Ivanti Policy Secure external interface needs to lease IP
-
Existing Management Subnet: Subnet from which the Ivanti Policy Secure management interface needs to lease IP
-
-
Agree to the Azure licensing terms and click Purchase.
-
Watch for the deployment succeeded message after 3 to 5 minutes.

-
Go to the resource group in which the Ivanti Policy Secure Virtual appliance was deployed to see the resources created.
-
Navigate to the resource group and click PPS Management Public IP. Make a note of the Ivanti Policy Secure Management Public IP and DNS name (FQDN) to access Ivanti Policy Secure for admin page.

Azure allows static as well as dynamic assignment of the IP addresses to the network interfaces. The mode of IP assignment (static/dynamic) can be mentioned in the Azure Resource Manage template file. The current JSON template uses dynamic method of allotting IP addresses to the network interfaces.
Deployment on VM with Two NIC Cards
To deploy Ivanti Policy Secure on Azure using the Azure portal, do the following:
-
1.Select the template file “pulsesecure-pps-2-nics-existing-vnet” created in the section ‘Upload Azure Resource Manager Template to Azure account’ and click Deploy.
Before proceeding with deployment, ensure that the attribute “accept-license-agreement” in
pulse-config is set to “y”.
-
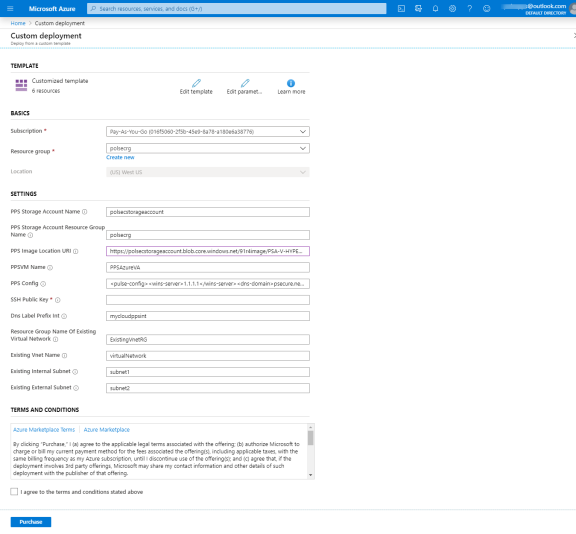
Fill or modify the following parameters:
-
Resource group: Specify the resource group name in which Ivanti Policy Secure needs to be deployed
-
Location: Region where resource group needs to be created
-
PPS Storage Account Name: Storage account name where the Ivanti Policy Secure Virtual Appliance image is available
-
PPS Storage Account Resource Group: Resource group of where the Ivanti Policy Secure Virtual Appliance image is copied
-
PPS Image Location URI: URI to Ivanti Policy Secure Virtual Appliance Image
-
PPS VM Name: Name of the Ivanti Policy Secure Virtual instance
-
PPS Config: Provisioning parameters in XML format.
-
SSH Public Key: This key is used to access PPS via SSH. The SSH keys are generated using ssh-keygen on Linux and OS X, or PuTTyGen on Windows. For details about generating the SSH key pairs, refer:
For Windows: https://docs.microsoft.com/en-us/azure/virtual-machines/linux/ssh-from-windows
For MacOS and Linux: https://docs.microsoft.com/en-us/azure/virtual-machines/linux/mac-create-ssh-keys
-
DNS Label Prefix Int: Prefix for the internal interface DNS label
-
Resource Group Name of Existing Virtual Network: Resource Group name of the Virtual network
-
Existing Vnet Name: Virtual network name
-
Existing Internal Subnet: Subnet from which the Ivanti Policy Secure internal interface needs to lease IP
-
Existing External Subnet: Subnet from which the Ivanti Policy Secure external interface needs to lease IP
-
-
Agree to the Azure licensing terms and click Purchase.
-
Watch for the deployment succeeded message after 3 to 5 minutes.

-
Go to the resource group in which the Ivanti Policy Secure Virtual appliance was deployed to see the resources created.
-
Click Ivanti Policy Secure Internal Public IP and note down the Ivanti Policy Secure Internal Public IP and DNS name (FQDN) to access PPS for end user page.

Azure allows static as well as dynamic assignment of the IP addresses to the network interfaces. The mode of IP assignment (static/dynamic) can be mentioned in the Azure Resource Manage template file. The current JSON template uses dynamic method of allotting IP addresses to the network interfaces.