Configuring IoT Access Policy
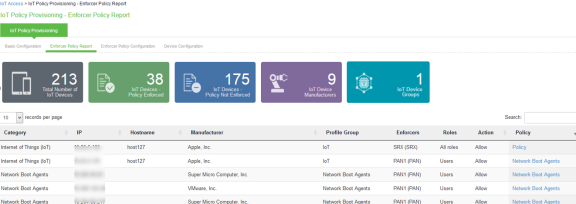
Viewing Devices in Enforcer Policy Report
This page provides details of discovered and connected IoT device's and firewall policies applied for IoT devices. You can view details such as total number of IoT devices, number of IoT devices enforced, number of IoT devices not enforced, and IoT device manufacturers.
To view the enforcer policy report:
-
Select Endpoint Policy > IoT Access > IoT Policy Provisioning.
-
Click Enforcer Policy Report.
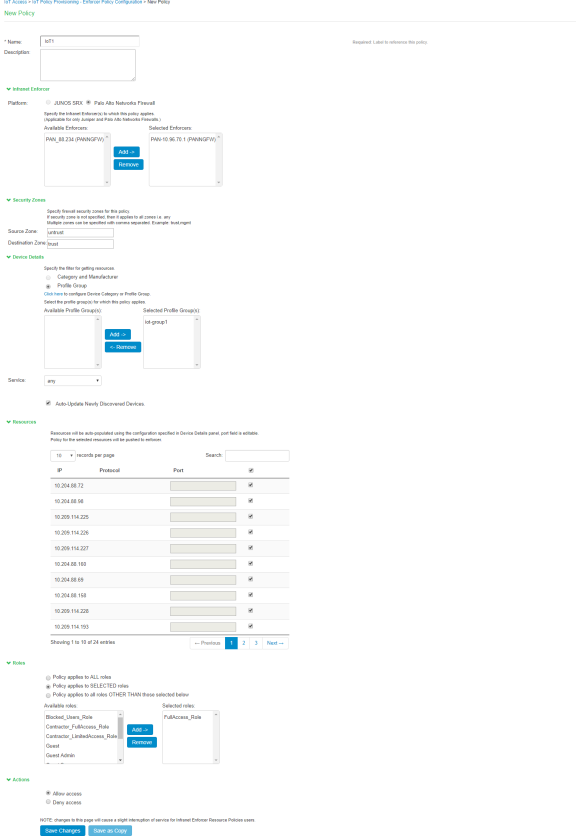
Configuring IoT Access Policy using Palo Alto Networks Firewall
The IoT access policy specifies which users are allowed or denied access to a set of protected resources. You can specify which users you want to allow or deny by choosing the roles for each IoT Access Policy. The IoT Access Policy page enables you to configure the policy based on device details using Profiler device attributes, such as device category and device manufacturer or Profile Group.
When the network Administrator selects category and manufacturer or Profile Group information under device details the IP addresses of the corresponding discovered devices get automatically updated under Resources. Hencethe Administrator can seamlessly create IoT Access Policy of profiled devices based on device category, device manufacturerattributes, or Profiler group. If the Administrator wants to have granular control over the IoT devices, further control can be achieved by providing specific port and protocol. The specified port and protocol configuration is applied to all the discovered devices of the selected category and manufacturers.
Follow the steps as mentioned below to configure IoT access policy:
-
Select Endpoint Policy > IoT Access > IoT Policy Provisioning > Enforcer Policy Configuration.
-
Click New Policy.
-
Enter the Policy name.
-
Enter a description.
-
Under Infranet Enforcer, select the Platform as Palo Alto Networks Firewall.
-
Under Security Zones, specify the firewall security zones (source zone/destination zone) for the policy. Multiple zones can be specified with comma separated values. If zones are not specified, then it applies to all zones.
-
Under Service, select any to allow all TCP and UDP ports (default) or select the service to specify the TCP or UDP port or port range. The policy port and protocol configuration remain same for all the resources.
-
Under Device Details, specify whether the policy should be applied based on device category and manufacturer or Profile group.
-
Category and manufacturer
-
Specify the category from the drop-down list. The values in the drop-down list is populated based on the Device category configuration (IoT Access > IoT Policy Provisioning - Device Configuration).
-
Select the Device manufacturer from the Available Device Manufacturers.
-
Specify the protocol (TCP/UDP) and Port/Range to be applied to the discovered devices.
-
-
Profile Group
-
Configure the Profiler Group (IoT Access > IoT Policy Provisioning - Device Configuration). To configure Profiler Groups, see Configuring Profiler Groups.
-
Select the Profile Group from the Available Profile Groups.
-
Specify the protocol (TCP/UDP) and Port/Range to be applied to the discovered devices.
-
Port ranges must be configured in dash-separated, comma-delimited, ascending, and non-overlapping order. Multiple port ranges must be separated by a comma. For example, the following examples show the delimiters that are used to enter port ranges:(80, 443, 1-1024, 1-100, 500-600).
The Port/Range entered will be applied to all the discovered devices.
-
Select Auto-Update Newly Discovered Devices to automatically add IoT Access Policy for the newly discovered devices from the selected category and manufacturer or Profile Group.
For example, If a policy is created for IoT device category with manufacturer or Profile Group with Auto-Update Newly Discovered Devices enabled then for any new IoT device discovered with the selected manufacturer, a IoT Access Policy is automatically added to firewall. If port and protocol are specified in the "Device Details" panel, the policy for the newly discovered devices is applied for specified port and protocol.
-
-
Under Resources, the IoT devices will be auto populated using the Device details configuration described earlier. If the administrator wants to apply policies on different ports and protocols for different discovered devices, the port configuration can be edited. If the Admin selects multiple protocol (for example, TCP and UDP) then the device entries appear twice with protocol information in the Resources table. The Admin can choose whether to push the policies for the selected resource based on the IP address, Protocol, and Port information to enforcer by enabling/disabling the checkbox in the resources table.
-
Select the desired Roles for which the policy applies. For example, IoT Administrator.
-
Under Actions, select whether to allow access or deny access.
-
Click Save Changes.
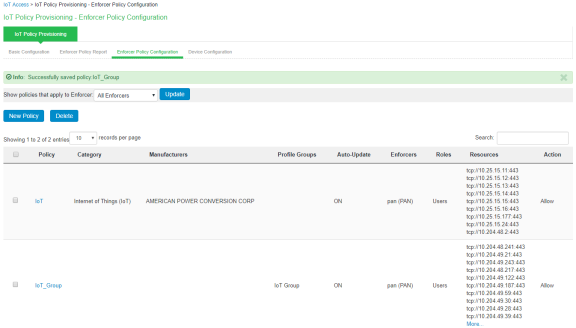
Once the policy is successfully added, it can be viewed as shown in figure.
Resource Access Policy and IoT Policy Provisioning with Palo Alto Network’s Firewall works only with default Virtual System “vsys1” and default device name “localhost.localdomain” configuration.