Working with User Authentication
The Services Director VA supports user authentication in two forms:
•vTM user authentication controls access to individual vTM instances. See Overview: vTM User Authentication.
•Services Director user authentication controls access to the Services Director's graphical user interface (GUI), command line interface (CLI) and REST API. See Overview: Services Director User Authentication.
Overview: vTM User Authentication
Each Virtual Traffic Manager (vTM) supports user authentication. This enables the vTM to verify the identify of any connecting user.
The use of vTM user authentication is optional.
The vTM verifies a user’s credentials (username and password) against two possible user authentication sources:
•Local users - user credentials are authenticated against all locally-defined user accounts (such as admin).
•Remote authenticators - user credentials are authenticated against externally-located servers that are based on RADIUS, LDAP or TACACS+ services.
Successful authentication identifies the user’s permission group. This defines the activities that the connected user can perform on the vTM.
The Services Director VA enables you to optionally configure the authenticators and permissions groups that will be used by the vTMs within its estate. Specific combinations of authenticators and permission groups are combined as access profiles on the Services Director.
To configure vTM user authentication, you must create:
•(Secure LDAP only) One or more vTM authentication certificates, see Adding a CA Certificate (Secure LDAP Only).
•One or more Services Director authenticators, see No CA certificate is required for non-secure LDAP connections. Similarly, no certificate is required for either RADIUS connections or TACACS+ connections..
•One or more permission groups. See Creating a Permission Group.
•One or more access profiles. See Creating an Access Profile (vTM User Authentication Only).
The Services Director Administrator chooses when to apply user authentication to a vTM. This is either:
•During the acceptance of a vTM self-registration request. See Accepting a Pending Self-Registration Request.
•During later configuration of the vTM from the Services Director VA. See Applying User Authentication to a vTM.
Both processes require the Services Director Administrator to choose an access profile. The access profile identifies the authenticators and permission groups that are applied to the vTM to define its user authentication. These will be applied to the vTM. All cluster members are affected. If the assigned authenticator is a secure LDAP authenticator, all of the vTM certificate authorities will also be applied.
If you are using a secure LDAP server for vTM access, there must be a matching certificate present when the access profile is applied, see Applying User Authentication to a vTM.
The vTM Administrator can also configure user authentication directly from the vTM. The Services Director does not track any such activity, and cannot display live user authentication settings for the vTM.
Overview: Services Director User Authentication
Services Director user authentication controls access to the Services Director's graphical user interface (GUI), command line interface (CLI) and REST API.
The use of Services Director user authentication is optional.
User credentials (username and password) are evaluated against two possible user authentication sources:
•Local users - user credentials are authenticated against all locally-defined user accounts (such as admin).
•Remote authenticators - user credentials are authenticated against externally-located servers that are based on RADIUS, LDAP or TACACS+ services.
Successful authentication identifies the user’s permission group. This defines the activities that the connected user can perform on the vTM.
For Services Director user authentication, there is typically a single permission group, which has access to all functionality.
To configure Services Director user authentication, you must create:
•(Secure LDAP only) One or more Services Director authentication certificates, see Adding a CA Certificate (Secure LDAP Only).
•One or more Services Director authenticators, see No CA certificate is required for non-secure LDAP connections. Similarly, no certificate is required for either RADIUS connections or TACACS+ connections..
•A permission group. See Creating a Permission Group.
Access profiles (which are required for vTM user authentication) are not required for Services Director user authentication.
Once you have created a Services Director authenticator and a permission group, the configuration of Services Director user authentication is complete.
Adding a CA Certificate (Secure LDAP Only)
If you are using secure LDAP connection for user authentication on either the Services Director or vTMs, you require a matching CA certificate.
No CA certificate is required for non-secure LDAP connections. Similarly, no certificate is required for either RADIUS connections or TACACS+ connections.
To add a CA certificate for either vTM or Services Director access:
1.Access your Services Director VA from a browser, using its Service Endpoint IP Address.
2.Log in as the administration user. The Home page appears.
3.Click the Catalogs menu, and then click Authentication: Certificate Authorities.
The Certificate Authorities page appears.
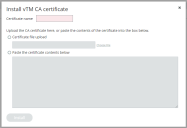
4.Click the plus symbol above either the vTM certificate authorities table or the Services Director certificate authorities table.
A dialog box appears. For example:
5.Enter a Certificate name.
6.Either:
•Select Certificate file upload and choose the required CA certificate file, OR
•Select Paste the certificate contents below and paste the CA certificate content from your clipboard.
7.Click Install.
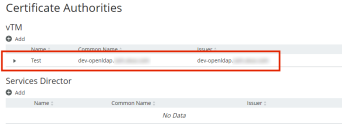
After the CA certificate installs, it is added to the list of certificate authorities. For example:
Creating an Authenticator
Services Director supports user authentication at both the vTM level and the Services Director level.
One or more authenticators are required when establishing user authentication from the Services Director VA. An authenticator defines an external user authentication service. Three proprietary authentication services are supported, each of which has service-specific settings.
Services Director supports standard LDAP user authentication and certificate-based secure LDAP user authentication for both Services Director and VTMs.
•LDAP (both secure and non-secure), see Creating an LDAP Authenticator.
•RADIUS, see Creating a RADIUS Authenticator.
•TACACS+, see Creating a TACACS+ Authenticator.
Authenticators are listed on the Authenticators page, see Viewing Authenticators.
A vTM administrator can also create and implement an authenticator on the vTM directly. Refer to the Virtual Traffic Manager documentation for details.
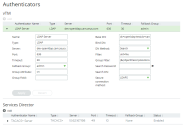
Viewing Authenticators
One or more authenticators are required when establishing user authentication from the Services Director VA.
The Authenticators page includes a table of vTM authenticators and a table of Services Director authenticators. Each entry in these tables shows the details that are common to all user authentication services (LDAP, Radius, TACACS+).
|
Name |
Description |
|
Authenticator Name |
The name of the authenticator. |
|
Type |
The user authentication service for the authenticator. That is: LDAP, RADIUS or TACACS+. |
|
Server |
The IP address or hostname of the user authentication server. |
|
Port |
The port used to connect to the user authentication server. |
|
Timeout |
The timeout period (in seconds) for a connection to the user authentication server. |
|
Fallback Group |
The permissions group to which a valid user will belong if its group is not identified. |
|
Status |
(Services Director authenticators only). Indicates whether the authenticator is the active authenticator. |
Expand an entry in either table to see full details for an authenticator. The displayed details will vary, depending on whether the authenticator is LDAP, RADIUS or TACACS+.
Creating an LDAP Authenticator
This procedure supports:
•Both vTM authenticators and Services Director authenticators.
•Both secure and non-secure LDAP user authentication.
To create an LDAP authenticator:
1.Access your Services Director VA from a browser, using its Service Endpoint IP Address.
2.Log in as the administration user. The Home page appears.
3.Click the Catalogs menu, and then click Authentication: Authenticators.
The Authenticators page appears.
4.Click the plus symbol above either the vTM authenticator table or the Services Director authenticator table.
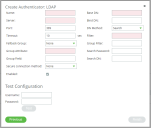
The Create Authenticator dialog box appears.
5.Select the LDAP authenticator type, and click Next.
The Create Authenticator: LDAP dialog box appears.
6.Specify the following authenticator properties:
•Name: The name of the LDAP authenticator on the Services Director.
•Server: The IP address or hostname of the LDAP server.
•Port: The port used to connect to the LDAP server.
•Timeout: The timeout period (in seconds) for a connection to the LDAP server.
•Fallback Group: A permission group, for example: "admin".
If Group Attribute is not defined, or is not set for the user, the permission group named here will be used.
•Group Attribute: The LDAP attribute that gives a user's group. For example: "memberOf".
If multiple values are returned by the LDAP server the first valid one will be used.
This is required if Fallback Group is unset.
•Group Field: the sub-field of the Group Attribute that gives a user's group.
For example: if Group Attribute is "memberOf" which delivers "CN=mygroup, OU=groups, OU=users, DC=mycompany, DC=local", set Group Field to "CN". The first matching field will be used.
•Secure Connection Method: the required LDAP security type:
•None. Select this if your LDAP server does not support secure connections.
•STARTTLS. Select this if your LDAP server supports STARTTLS secure connections. You must ensure that a matching CA certificate is present to use this option.
•LDAPS. Select this if your LDAP server supports LDAPS secure connections. You must ensure that a matching CA certificate is present to use this option.
•Base DN: The base DN (Distinguished Name) for directory searches.
•Bind DN: A template to construct the bind DN from the username. This is only used when the DN Method is "Construct".
The string "%u" is replaced by the username. For example: "%[email protected]" or "cn=%u, dn=mycompany, dn=local"
•DN Method: This value determines relevance/requirement of Bind DN and Search DN.
Use "Construct" when the bind DN for a user can be constructed from a known string. Refer to the Bind DN field.
Use "Search" when the bind DN for a user can be searched for in the directory. This is necessary if you have users under different directory paths. Refer to the Search DN and Search Password fields.
•Filter: A filter that uniquely identifies a user located under the Base DN.
The string "%u" will be substituted with the username. For example: "sAMAccountName=%u" (Active Directory), or "uid=%u" (Unix LDAP).
•Group Filter: If the user record returned by the LDAP Filter does not contain the required group information, you can specify an alternative group search filter here. This will typically be required if you have Unix/POSIX-style user records. If multiple records are returned the list of group names will be extracted from all of them.
The string "%u" will be replaced by the username. For example: "(&(memberUid=%u)(objectClass=posixGroup))"
•Search DN / Search Password - the DN and password to use when searching the directory for a user's bind DN. These are only used when the DN Method is "Search". You can leave these blank if it is possible to perform the bind DN search using an anonymous bind.
7.(Optional) Set the Enabled check box if this is to be the active Services Director authenticator.
8.(Optional) Test the specified details for a Services Director user authentication by specifying a Username and Password and clicking Test.
This function is not available for vTM authenticators.
A matching CA certificate for Services Director access is required for this step, see Adding a CA Certificate (Secure LDAP Only).
9.Click Finish.
The LDAP authenticator is added to the Authenticator table.
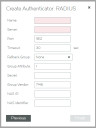
Creating a RADIUS Authenticator
This procedure supports both vTM authenticators and Services Director authenticators.
1.Access your Services Director VA from a browser, using its Service Endpoint IP Address.
2.Log in as the administration user. The Home page appears.
3.Click the Catalogs menu, and then click Authentication: Authenticators. The Authenticators page appears.
4.Click the plus symbol above either the vTM authenticator table or the Services Director authenticator table.
The Create Authenticator dialog box appears.
5.Select the RADIUS authenticator type, and click Next.
The Create Authenticator: RADIUS dialog box appears.
6.Specify the following authenticator properties:
•Name: The name of the RADIUS authenticator on the Services Director.
•Server: The IP address or hostname of the RADIUS server.
•Port: The port used to connect to the RADIUS server.
•Timeout: The timeout period (in seconds) for a connection to the RADIUS server.
•Fallback Group: If no group is found using the vendor and group identifiers, or the group found is not valid, the group specified here will be used.
•Group Attribute: The RADIUS identifier for the attribute that specifies an account's group.
This is optional if Fallback Group is specified, but required if Fallback Group is unset.
•Secret: The secret key shared with the RADIUS server.
•Group Vendor: The RADIUS identifier for the vendor of the RADIUS attribute that specifies an account's group.
Leave blank if using a standard attribute such as Filter-Id.
•NAS IP: A string identifying the Network Access Server (NAS) which is requesting authentication of the user. This value is sent to the RADIUS server.
If left blank, the address of the interface used to connect to the server will be used.
•NAS Identifier: The identifying IP Address of the NAS which is requesting authentication of the user. This value is sent to the RADIUS server.
7.(Optional) Set the Enabled check box if this is to be the active Services Director authenticator.
This property is not available for vTM authenticators.
8.Click Finish.
The RADIUS authenticator is added to the Authenticator table.
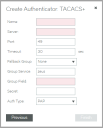
Creating a TACACS+ Authenticator
This procedure supports both vTM authenticators and Services Director authenticators.
1.Access your Services Director VA from a browser, using its Service Endpoint IP Address.
2.Log in as the administration user. The Home page appears.
3.Click the Catalogs menu, and then click Authentication: Authenticators. The Authenticators page appears.
4.Click the plus symbol above either the vTM authenticator table or the Services Director authenticator table.
The Create Authenticator dialog box appears.
5.Select the TACACS+ authenticator type, and click Next.
The Create Authenticator: TACACS+ dialog box appears.
6.Specify the following authenticator properties:
•Name: The name of the TACACS+ authenticator on the Services Director.
•Server: The IP address or hostname of the TACACS+ server.
•Port: The port used to connect to the TACACS+ server.
•Timeout: The timeout period (in seconds) for a connection to the TACACS+ server.
•Fallback Group: If Group Service is not defined, or no group value is provided for the user by the TACACS+ server, the group specified here will be used.
•Secret: The secret key shared with the TACACS+ server.
•Auth Type: The TACACS+ authentication type, either "PAP" or "ASCII".
•Group Service: The TACACS+ "service" that identifies a user's group field. This is required if Fallback Group is unset.
•Group Field: The TACACS+ "service" field that provides each user's group.
7.(Optional) Set the Enabled check box if this is to be the active Services Director authenticator.
This property is not available for vTM authenticators.
8.Click Finish.
The TACACS+ authenticator is added to its authenticator table.
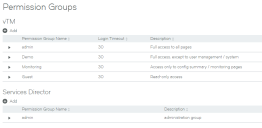
Creating a Permission Group
Services Director supports user authentication at both the vTM level and the Services Director level.
•One or more permission groups are required when establishing vTM user authentication. Each permission group defines what a user in the group can do, by combining permission names with access levels. There are four default permission groups:
•admin - this group has full access to all vTM pages.
•Demo - this group has full access, except to user management / system.
•Monitoring - this group has access only to config summary / monitoring pages.
•Guest - this group has read-only access
•A single permission group is typically required when establishing Services Director user authentication. This permission group has access to all functionality.
Permission groups are listed on the Permission Groups page, see Viewing Permission Groups.
You create permission groups from the Permission Groups page.
•To create a permission group for vTM user authentication, see Creating a Permission Group (vTM User Authentication).
•To create a permission group for Services Director authentication, see Creating a Permission Group (SD User Authentication).
The vTM administrator can create and implement a permission group on the vTM directly. Refer to the Virtual Traffic Manager documentation for details.
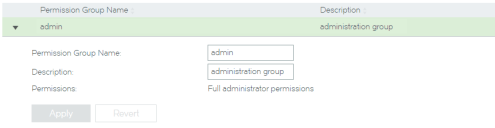
Viewing Permission Groups
One or more authenticators are required when establishing user authentication from the Services Director VA. Each permission group defines what a user in the group can do.
The Permission Groups page includes a table of permission groups for vTM user authentication, and a table of permission groups for Services Director user authentication.
Each entry in the permission groups table displays summary details for the permission group.
To view full details for a vTM user authentication permission group, click the arrow on the left side of the permission group’s entry.
|
Name |
Description |
|
Permission Group Name |
The name of the permission group. |
|
Timeout (vTM Only) |
A timeout setting (in minutes) for a login session for a user in this group. A zero value indicates that sessions should never time out. |
|
Description |
A list of permissions known by the Services Director. The access level for each of these can be set to None, Read-Only or Full. |
|
Permission |
A list of permissions known by the Services Director. The access level for each of these can be set to None, Read-Only or Full. If you click Advanced Options, you can manually specify permissions of which Services Director is not aware. That is, you can reference any permission that is supported by the vTM. To find these permission names, refer to the Virtual Traffic Manager documentation. The Services Director VA does not verify permissions entered under Advanced Options. The vTM itself verifies all permissions when the permission group is applied to the vTM. Any permission that is not recognized by the vTM is ignored. |
To view full details for a Services Director user authentication permission group, click the arrow on the left side of the permission group’s entry.
Typically, there is only one Services Director user authentication permission group.
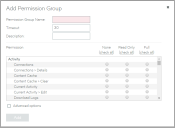
Creating a Permission Group (vTM User Authentication)
1.Access your Services Director VA from a browser, using its Service Endpoint IP Address.
2.Log in as the administration user. The Home page appears.
3.Click the Catalogs menu, and then click Authentication: Permission Groups. The Permission Groups page appears.
4.Click the plus symbol above the vTM permission group table.
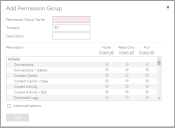
The Add Permission Group dialog box appears.
5.Specify a Permission Group Name.
6.Specify a Timeout period, in minutes.
7.(Optional) Add a description for the permission group.
8.Specify an access level for each listed Permission. That is, None, Read-Only or Full.
•To select None for all listed permissions, click None (check all).
•To select Read-Only for all listed permissions, click Read-Only (check all).
•To select Full for all listed permissions, click Full (check all).
9.To specify a permission for an unlisted Permission:
•Click Advanced Options.
•Enter the name of the Permission. You can reference any permission that is supported by the vTM. To find these permission names, refer to the Virtual Traffic Manager documentation.
•Select the required access level. That is, None, Read-Only or Full.
10.Click Add to create the vTM permission group.
The vTM administrator can create and implement a permission group on the vTM. Refer to the Virtual Traffic Manager documentation for details.
Creating a Permission Group (SD User Authentication)
1.Access your Services Director VA from a browser, using its Service Endpoint IP Address.
2.Log in as the administration user. The Home page appears.
3.Click the Catalogs menu, and then click Authentication: Permission Groups. The Permission Groups page appears.
4.Click the plus symbol above the Services Director permission group table.
The Add Permission Group dialog box appears.
5.Specify a Permission Group Name.
6.(Optional) Add a description for the permission group.
7.Click Add to create the Services Director permission group.
Creating an Access Profile (vTM User Authentication Only)
An access profile is required when establishing user authentication for a vTM from the Services Director VA. An access profile combines an authenticator with one or more permission groups. When and access profile is selected, the authenticator and permission groups included in the profile are used by the vTM to define its user authentication.
Access profiles are not required when creating Services Director user authentication.
Access profiles are listed on the Access Profiles page, see Viewing Access Profiles.
You create access profiles from the Access Profiles page, see Creating an Access Profile.
The use of access profiles enable the Services Director Administrator to set the user authentication on the vTM from the Services Director VA. However, the vTM Administrator can also configure user authentication directly from the vTM. The Services Director does not track any such activity, and cannot display live user authentication settings for the vTM.
If you are using a secure LDAP server for vTM access, there must be a matching certificate present when the access profile is applied, see Applying User Authentication to a vTM.
Viewing Access Profiles
An access profile is required when establishing user authentication for a vTM from the Services Director VA. An access profile combines an authenticator with one or more permission groups. When it is selected, the authenticator and permission groups included in the access profile are used by the vTM to define its user authentication.
Access profiles are not supported for Services Director user authentication.
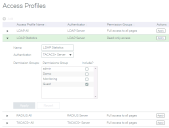
The Access Profiles page shows a table of all access profiles defined on the Services Director. Each entry in the table shows summary details for an access profile.
|
Name |
Description |
|
Access Profile Name |
The name of the access profile. This is used when applying an access profile to: a Pending self-registration request by a vTM. See Accepting a Pending Self-Registration Request. one or more registered/deployed vTMs. See Applying User Authentication to a vTM. |
|
Authenticator |
The selected authenticator for the access profile. See No CA certificate is required for non-secure LDAP connections. Similarly, no certificate is required for either RADIUS connections or TACACS+ connections.. |
|
Permission Groups |
A list of permission groups included in the access profile. There are four default permission groups, but you can define others. See Creating a Permission Group. |
|
Actions |
The Apply to vTM Instance(s) control in this column enables you to apply the permissions groups and authenticators associated with this access profile to one or more vTMs. See Applying User Authentication to a vTM. |
To view full details for an access profile, click the arrow on the left side of the access profile’s entry.
Creating an Access Profile
1.Access your Services Director VA from a browser, using its Service Endpoint IP Address.
2.Log in as the administration user. The Home page appears.
3.Click the Catalogs menu, and then click Authentication: Access Profiles. The Access Profiles page appears.
4.Click the plus symbol above the access profile table.
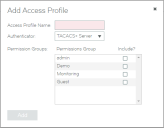
The Add Access Profile dialog box appears.
5.Specify an Access Profile Name.
6.Select an Authenticator.
7.Select one or more permission groups.
8.Click Add to create the access profile.
Applying User Authentication to a vTM
1.Access your Services Director VA from a browser, using its Service Endpoint IP Address.
2.Log in as the administration user. The Home page appears.
3.Click the Catalogs menu, and then click Authentication: Access Profiles. The Access Profiles page appears.
4.In the table of access profiles, locate the required access profile. Expand the entry to confirm its properties if required.
5.Click the Apply button that is next to the required access profile.
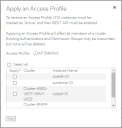
The Apply an Access Profile dialog box appears. This dialog box lists all vTMs that are Active and with a REST API enabled.
6.Select the check box for each required vTM instance, or click Select All.
7.Click Apply.
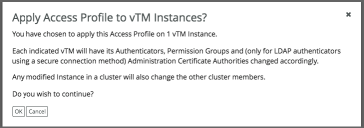
If you are using a secure LDAP server for vTM access, there must be a matching certificate present when the access profile is applied, see Applying User Authentication to a vTM.
A summary of selections appears. For example:
8.Click OK to continue.
The permissions groups and authenticators associated with the chosen access profile are applied to the selected vTMs. A progress bar tracks this:
Once the changes are complete, a message appears:
9.Click OK. The process is complete.
Working with vTM Templates
During the process of configuring a vTM for self-registration, you can mark a vTM as a template vTM. This prevents it from self-registering, but ensures that all vTMs made from the template will request self-registration.
The template vTM is visible in the list of virtual machines in VMware, and can be used to create other vTMs. Refer to the Virtual Traffic Manager documentation.