Application Control
The Application Control is your dashboard to monitor and to control your applications:
- You can monitor whether there have been any attacks.
- You can block all the traffic to all hosts of an application. For example, this can be useful in the event of a problem or during updates.
- You can deactivate a ruleset for an application temporarily without having to delete it. All requests are then accepted unchecked. This can be useful in the short term, for example if individual rules have been created that are too restrictive and users can no longer access parts of your web application.
Opening
In the navigation area, select Application Control.
The Application Control opens with an overview of all applications.
Unless you don’t belong to the user group zeusafm Administrator, you only see the subset of those applications to which you have access according to your user groups.
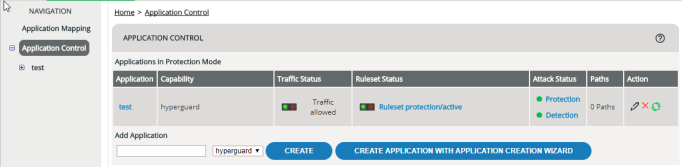
The list of applications is divided into two groups: applications in protection mode, and applications in detection mode (see Detection Mode, Protection Mode).
You can change the mode of an application on the Configuration | Application Settings tab (see Editing Applications).
Blocking/allowing traffic
ATTENTION
Blocking traffic even works when in detection mode. When you block traffic, your web application is no longer accessible.
To block or allow the traffic for a specific application:
The traffic light symbol indicates the current status:
- red: traffic blocked
- green: traffic allowed
Switching the rule set on or off
To switch the ruleset for a specific application on or off:
The traffic light symbol indicates the current status:
- red: ruleset inactive
- orange (flashing): no valid license
- green: ruleset active
Monitoring the attack status
You can check at a glance whether there have been any potential attacks on an application.
- If any requests were denied by the protection ruleset within the last 24 hours, the Protection symbol in the Attack Status column turns red (this symbol is only visible for applications in protection mode).
- If any requests were identified by the detection ruleset in the last 24 hours (requests that would have been denied if the detection ruleset had been a protection ruleset), the Detection symbol in the Attack Status column turns red (this symbol is only visible for applications in detection mode, as well as for application in protection mode that have a second, detection ruleset assigned).
You can click the colored symbols. This opens a pre-filtered log file view of the relevant requests (see Log Files).
Adding applications
To create a new application, enter its name into the field Add Application and click Create. For details, please refer to Editing Applications.