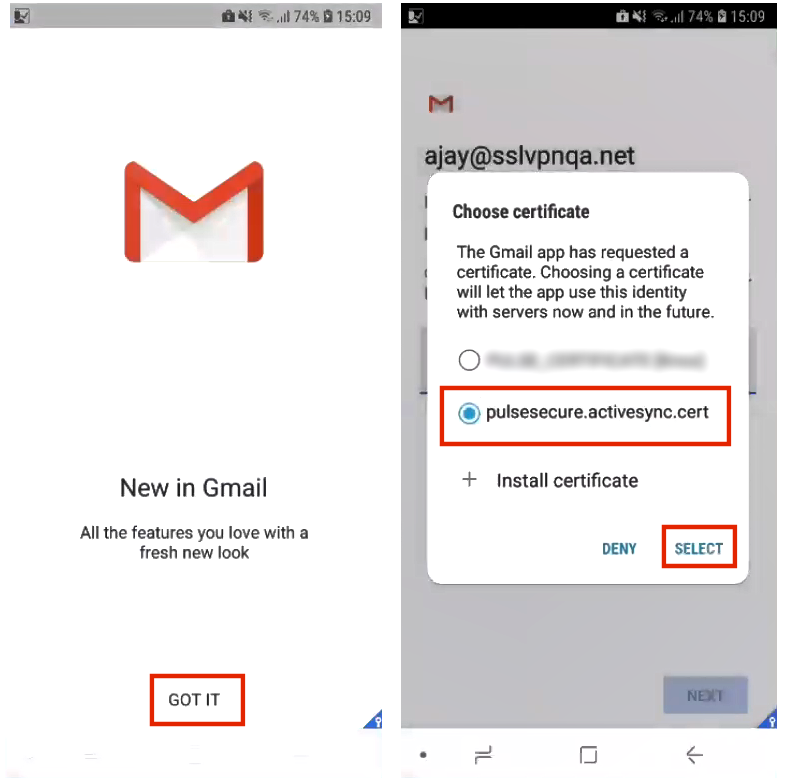
Configuring ActiveSync
Configuring Office365 as an ActiveSync Proxy
To configure Office365 as an ActiveSync proxy:
1.Navigate to Policies.
2.Select the policy name for which you would like to add ActiveSync configuration.
3.Click Properties.
4.Under ActiveSync, configure the following:
•ActiveSync Accept All Certificates: true
•ActiveSync Domain: pulsesecure.net
•ActiveSync Server: outlook.office365.com
•ActiveSync Server Proxy: None
•ActiveSync SSL: true
•ActiveSync UserID Field: email or username
•If ActiveSync Userid Field is set as username, in the Gmail and Google Calendar apps it shows activesync_domain\Username.
•If ActiveSync Userid Field is set as email, in the Gmail and Google Calendar apps it shows [email protected].
The Divide Productivity app is no longer supported and no more available in Google Play Store. Instead, Google's Gmail and Google Calendar apps provide universal Exchange support on Android and enterprise-focused features like managed configurations, scheduling, rich text formatting, and Exchange ActiveSync 16 support. For details, refer to see End of Life for the Divide Productivity app.
5.For Android policies only:
•Navigate to Policies > <policy_name> > Properties.
•Under Space, set Android Email Auto Configuration Enabled to true.
6.For iOS policies:
•Navigate to Policies > <policy_name> > Properties.
•Under iOS ActiveSync, set iOS ActiveSync Enabled to true.
7.Click Publish.
Configuring a Security Appliance as an ActiveSync Proxy
This feature enables a Pulse Connect Secure gateway to function as an ActiveSync proxy for Mobile devices that are onboarded through Pulse Workspace Server. Pulse Connect Secure gateway will be able to filter out and reject ActiveSync connection requests coming from unauthorized mobile devices and allow only those devices that have been successfully provisioned on Pulse Workspace Server.
Configuring Email Policy Attributes for ActiveSync
To configure policy attributes:
1.Navigate to Policies.
2.Select the policy name for which you would like to add ActiveSync configuration.
3.Click Properties.
4.Under ActiveSync, configure the following:
•ActiveSync Accept All Certificates: true
•ActiveSyncDomain: pulsesecure.net
•ActiveSync server: mail.pulsesecure.net
•ActiveSync Server Proxy: Security appliance
•ActiveSync SSL: true
•ActiveSync UserID Field: username
5.For Android policies only:
•Navigate to Policies > <policy_name> > Properties.
•Under Space, set Android Email Auto Configuration Enabled to true.
6.For iOS policies:
•Navigate to Policies > <policy_name> > Properties.
•Under iOS ActiveSync, set iOS ActiveSync Enabled to true.
7.Click Publish.
Specifying Role-Based Options
It is recommended that admin creates a new role for Pulse Workspace onboarded devices. Assuming that admin creates a new role with the name as “secure_email”, perform the following procedure:
1.Navigate to Users > User Roles.
2.Select the secure_email role.
3.Enable the Secure Mail check box.
4.Under Access features, click Save Changes.
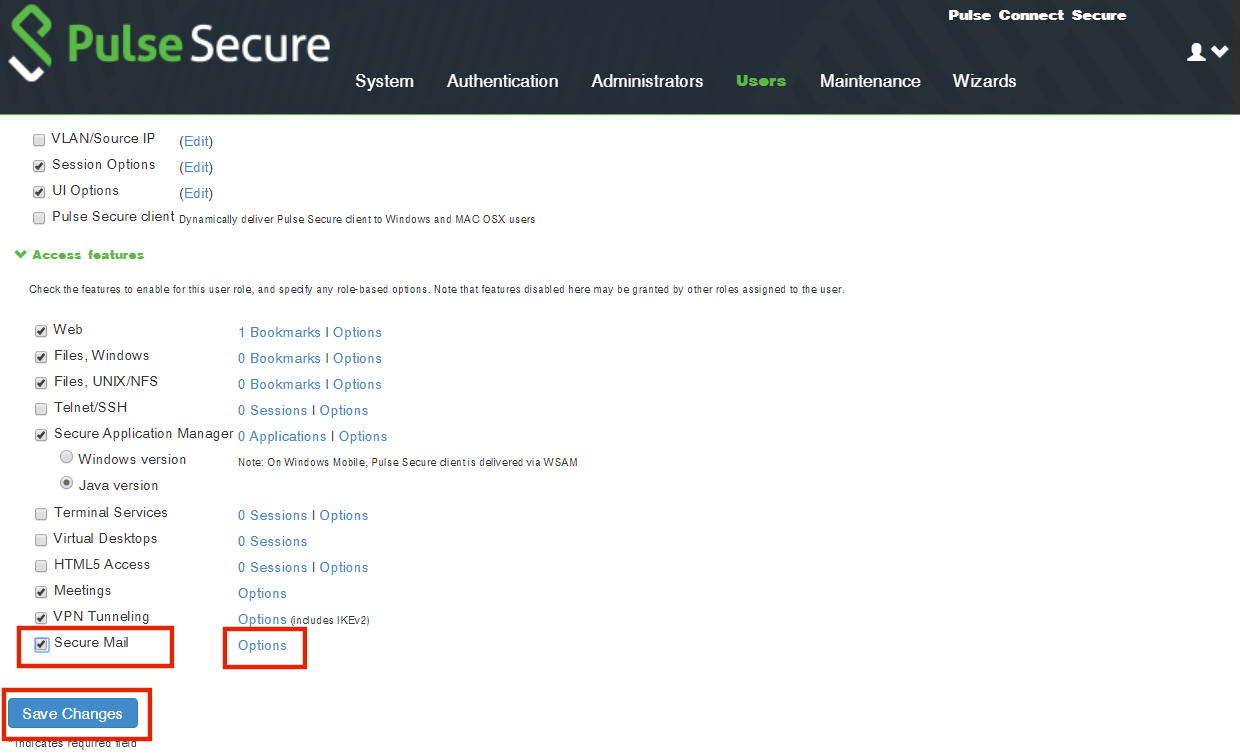
5.Navigate back to the Access features for the secure_email role and click Options.
The Secure Mail page appears.
6.Configure a Virtual Hostname which is resolvable on mobile devices.
7.Enter the Exchange Server address.
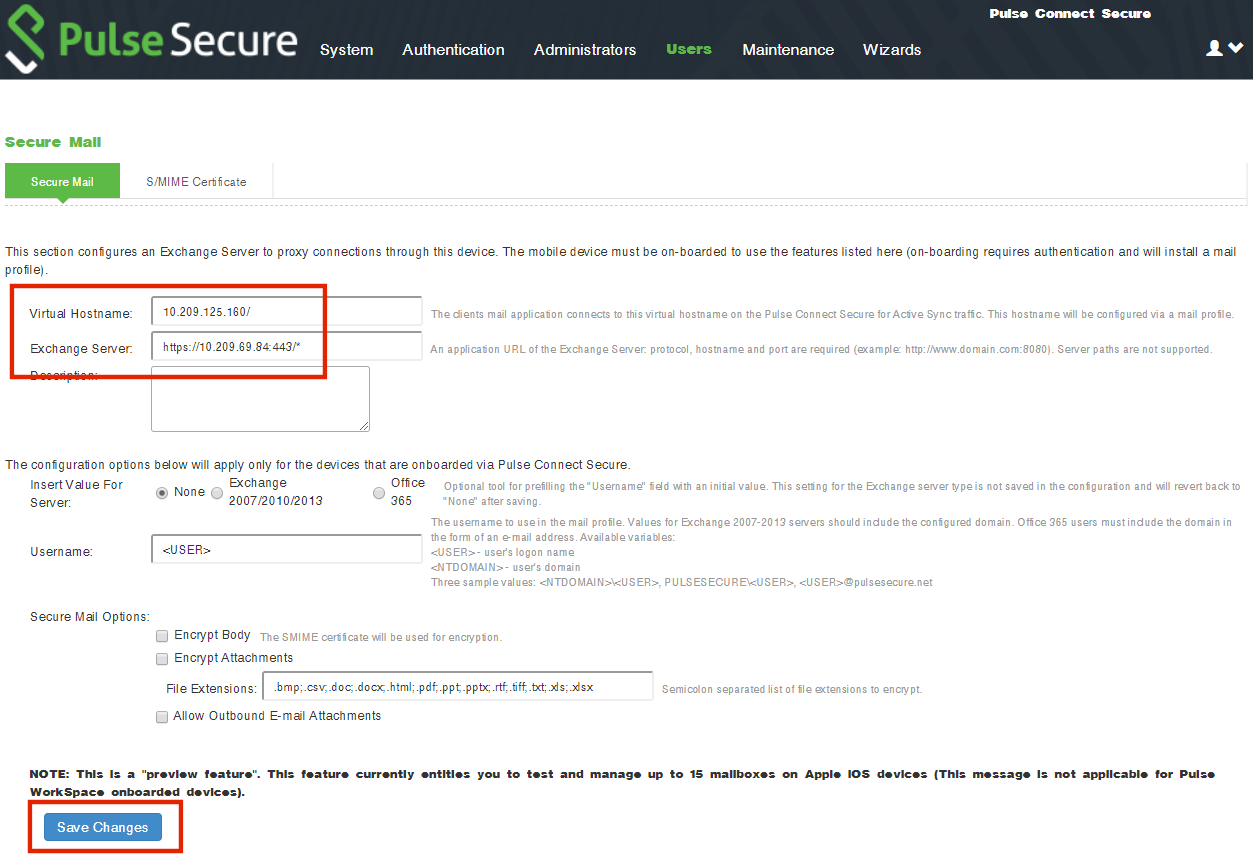
8.Click Save Changes.
9.Navigate to System > Configuration > Pulse One > Command Handlers.
The Pulse One page appears.
10.Select the Pulse Workspace Handler tab.
11.For the Device Role, select the role configured in previous step. That is, the secure_email role.
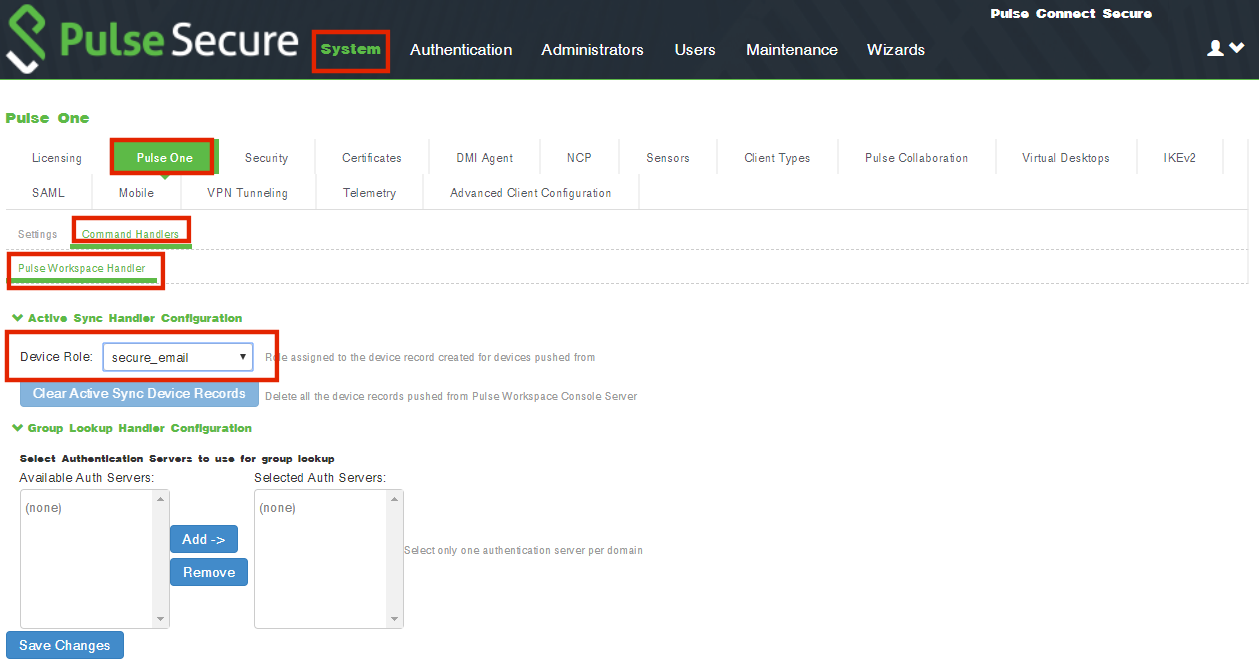
12.Click Save Changes.
Configuring the Appliance for ActiveSync
To configure the PCS appliance for ActiveSync:
1.Click the Settings icon on top-right-corner of the page and select Workspace Properties.
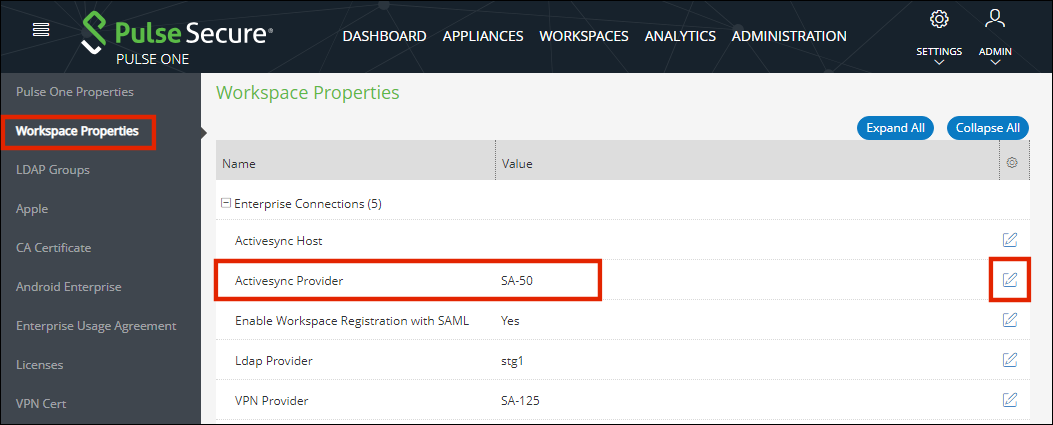
2.The Activesync Provider field must be set to the Connect Secure device. This requires ActiveSync configuration in the Pulse Connect Secure server, and for the details refer to the section “ActiveSync Configuration” in the Pulse Workspace Configuration Guide.
3.Click the Edit (![]() ) icon.
) icon.
The Edit Property dialog appears.
4.Modify the ActiveSync property of the policy. For example:
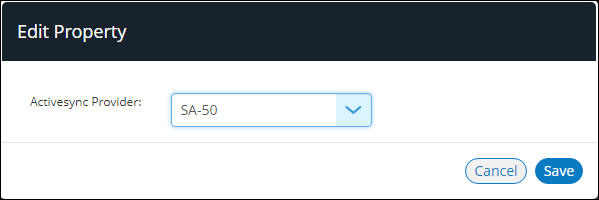
5.Click Save.
Configuring Certificate-Based ActiveSync
This feature enables the delivery of an ActiveSync certificate to mobile devices managed by Pulse Workspace. The device user can then select the ActiveSync certificate on the first use of any supported server/app.
The use of certificate-based ActiveSync is currently supported by the following server:
•Microsoft Exchange Server 2013.
To configure certificate authentication in Exchange Server, see https://docs.microsoft.com/en-us/Exchange/plan-and-deploy/post-installation-tasks/configure-certificate-based-auth?view=exchserver-2016.
This configuration only supports the on-premises Exchange Server, and not the cloud-based Office365.
The use of certificate-based ActiveSync is currently supported by the following email clients:
•On Android: Gmail and Nine Work apps.
•On iOS: the native iOS email app.
Currently, Pulse Workspace supports two delivery mechanisms for ActiveSync certificates:
•Pulse Workspace pushes a SCEP Payload to the onboarded Android and iOS devices. Each device then automatically fetches the ActiveSync certificate from the SCEP Server, see Working with ActiveSync Certificates via SCEP.
•Pulse Workspace fetches the ActiveSync certificate from a Windows CAWE server and pushes it to Android and iOS onboarded device, see Working with ActiveSync Certificates via Windows CAWE.
Working with ActiveSync Certificates via SCEP
To enable the delivery of an ActiveSync certificate via SCEP:
1.Log into Pulse One as an administrator.
2.Click the Settings icon on top-right-corner of the page and select Workspace Properties.
3.Expand the ActiveSync category.
4.If you want SCEP to be used to deliver an ActiveSync certificate to Android devices, set the Use SCEP to request certificate for Android ActiveSync from external PKI server workspace property to True.
5.If you want SCEP to be used to deliver an ActiveSync certificate to iOS devices, set the Use SCEP to request certificate for iOS ActiveSync from external PKI server workspace property to True.
6.Select the Workspaces menu.
7.Select the Policies tab.
8.Select a policy used by devices that require the delivery of an ActiveSync certificate.
9.Click the Properties tab for the selected policy.
10.Expand the Enterprise PKI Integration category.
11.Set the Activesync Allow Authentication via Certificate policy property to True.
12.Publish the policy to all devices.
Each affected device will then receive an SCEP payload, and will then automatically retrieve the required ActiveSync certificate from the SCEP server.
On each device, when a supported app (see Configuring Certificate-Based ActiveSync) is first used, the user is asked for an ActiveSync certificate instead of a username and password. The user should select the ActiveSync certificate from the list of available certificates on the device. For example:
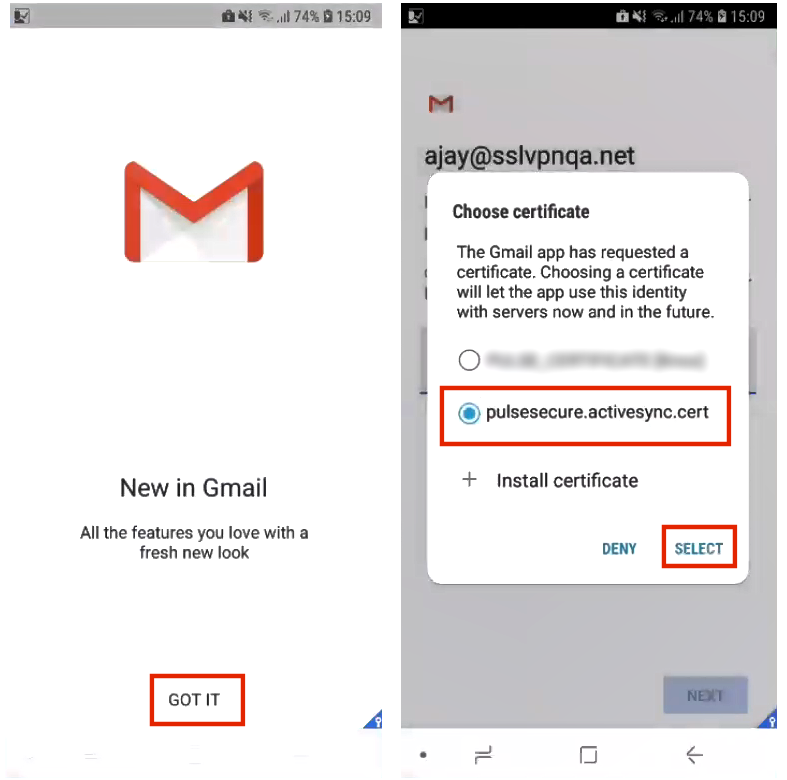
Working with ActiveSync Certificates via Windows CAWE
To enable the delivery of an ActiveSync certificate via SCEP:
1.Log into Pulse One as an administrator.
2.Click the Settings icon on top-right-corner of the page and select Workspace Properties.
3.Expand the ActiveSync category.
4.If you want Windows CAWE to deliver an ActiveSync certificate to Android devices:
•Set the Use Windows CA server CAWE to request ActiveSync certificates for both Android and iOS devices to True.
•Set the Use SCEP to request certificate for Android ActiveSync from external PKI server workspace property to False.
5.If you want Windows CAWE to deliver an ActiveSync certificate to iOS devices:
•Set the Use Windows CA server CAWE to request ActiveSync certificates for both Android and iOS devices to True.
•Set the Use SCEP to request certificate for iOS ActiveSync from external PKI server workspace property to False.
6.Select the Workspaces menu.
7.Select the Policies tab.
8.Select a policy used by devices that require the delivery of an ActiveSync certificate.
9.Click the Properties tab for the selected policy.
10.Expand the Enterprise PKI Integration category.
11.Set the Activesync Allow Authentication via Certificate policy property to True.
12.Publish the policy to all devices.
An ActiveSync certificate will be delivered by Windows CAWE to each affected device directly.
On each device, when a supported app (see Configuring Certificate-Based ActiveSync) is first used, the user is asked for an ActiveSync certificate instead of a username and password. The user should select the ActiveSync certificate from the list of available certificates on the device. For example: