Configuring Policy Settings
Adding an Android App to a Policy
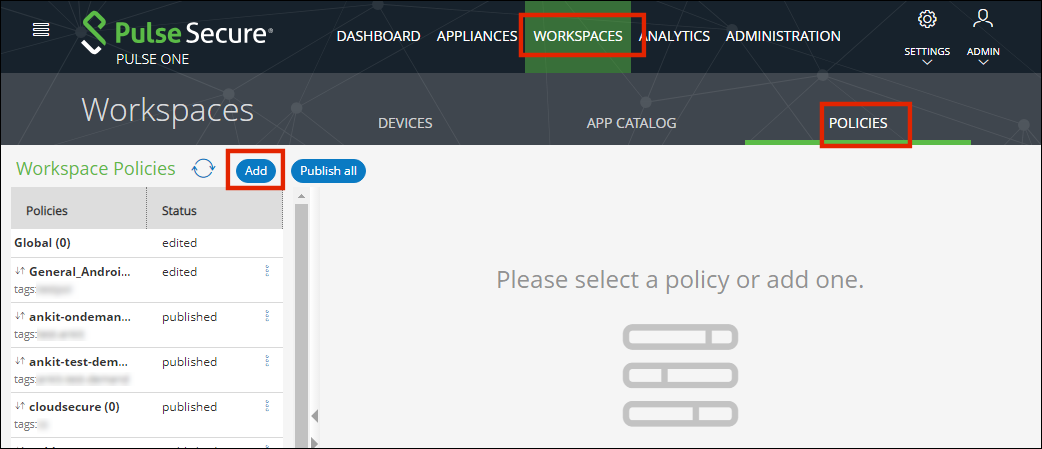
To add an app to a policy:
1.Log in to Pulse One as an admin.
2.Select the Workspaces menu.
3.Select the Policies tab.
4.Click Add to add a new policy.
5.Enter a Policy Name, complete the Has user tags property, and click Save. For example:
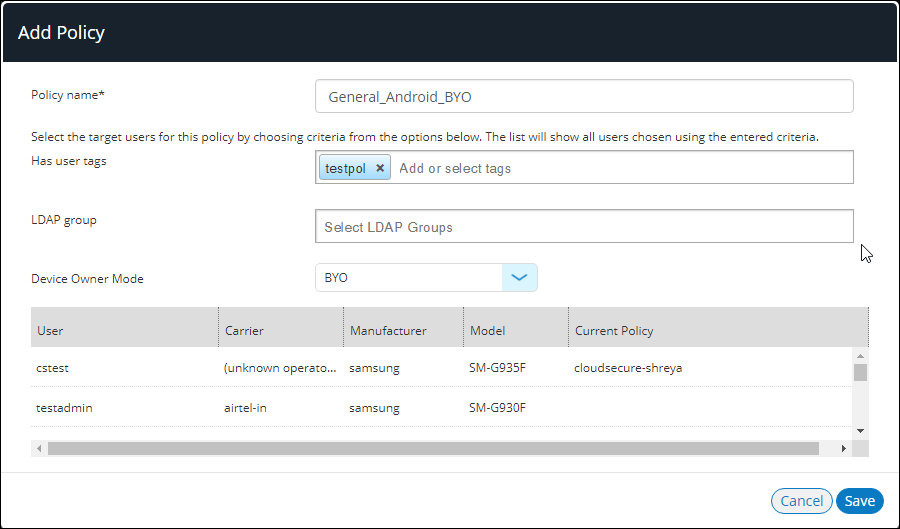
The policy is added to the Policies list in the Workspace Properties page.
You must now add apps from the Google Play Store to this policy.
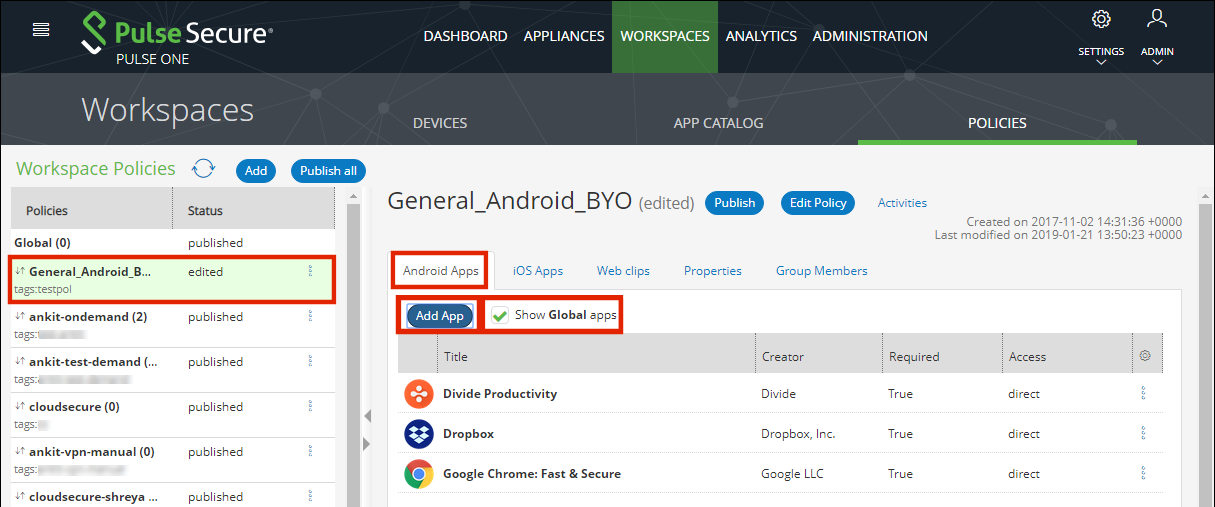
6.Click the Android Apps tab.
7.Enable the Show Global apps option.
A list of apps that are configured with global policy are displayed.
8.Click Add App.
9.In the Add App from App Catalog dialog, enter the app name in the Search box and press Enter.
A list of apps is displayed based on the search criteria. For example:
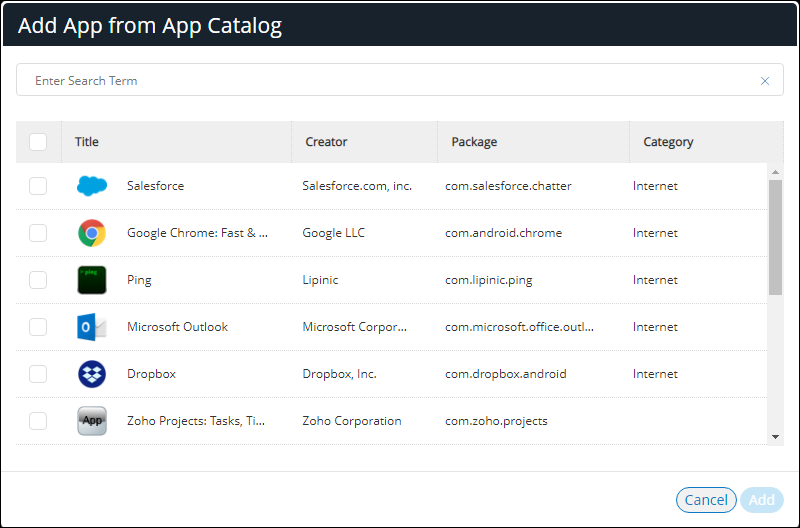
10.From the apps list, select the required app and click Add.
The app is added to the policy. For example:
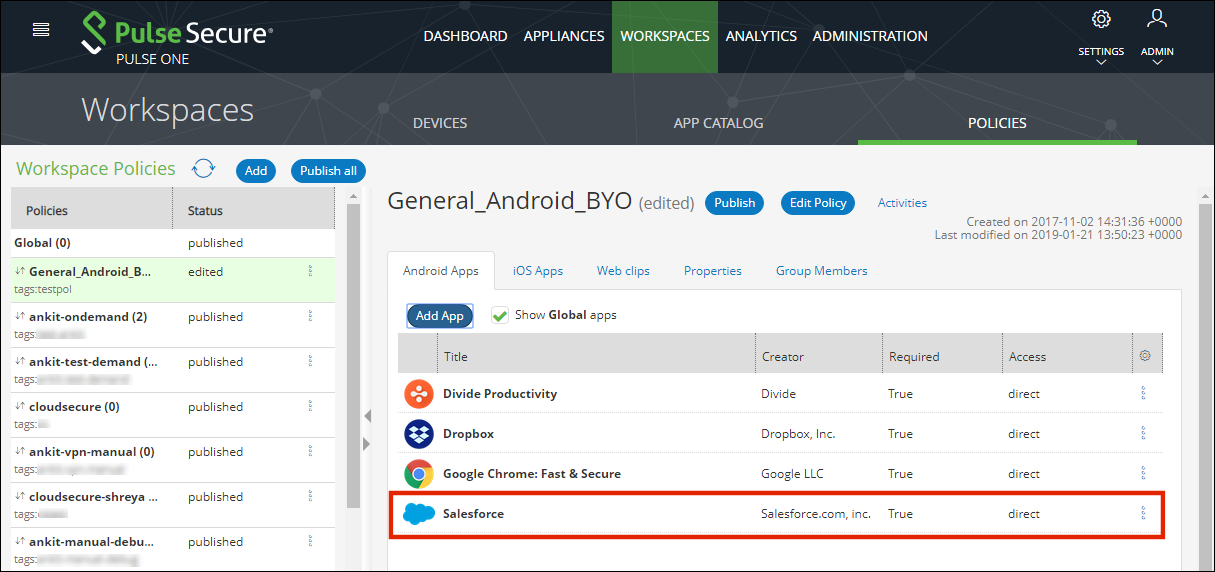
11.In the Android Apps list, select the Actions icon (![]() ) for the app and click Edit app rule.
) for the app and click Edit app rule.
The Configure App Details dialog appears.
12.Make the required configuration changes.
For example, if you access the app through VPN only, then set Network access to Require VPN.
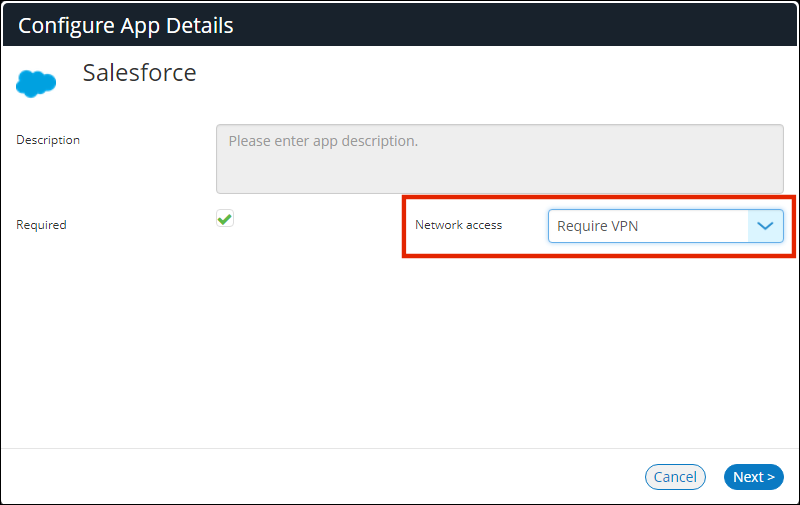
You cannot change the Description.
13.Click Next.
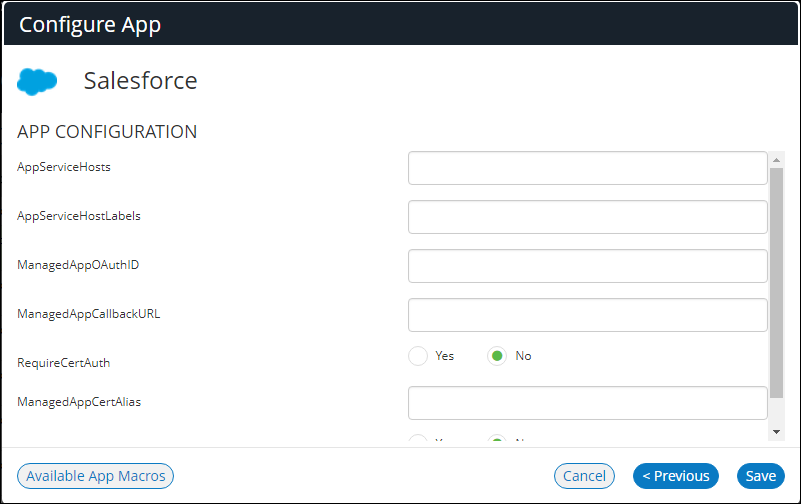
The Configure App dialog appears.
14.Supply the required configuration and click Save. For example:
15.Some apps need permissions to access. For these apps, the App Permissions dialog appears. Select the required permissions for the app and click Save.
For information about enabling app permission property and configuring default runtime permission, see Managing Pulse One Properties.
16.Select the app from the app list and click Publish.
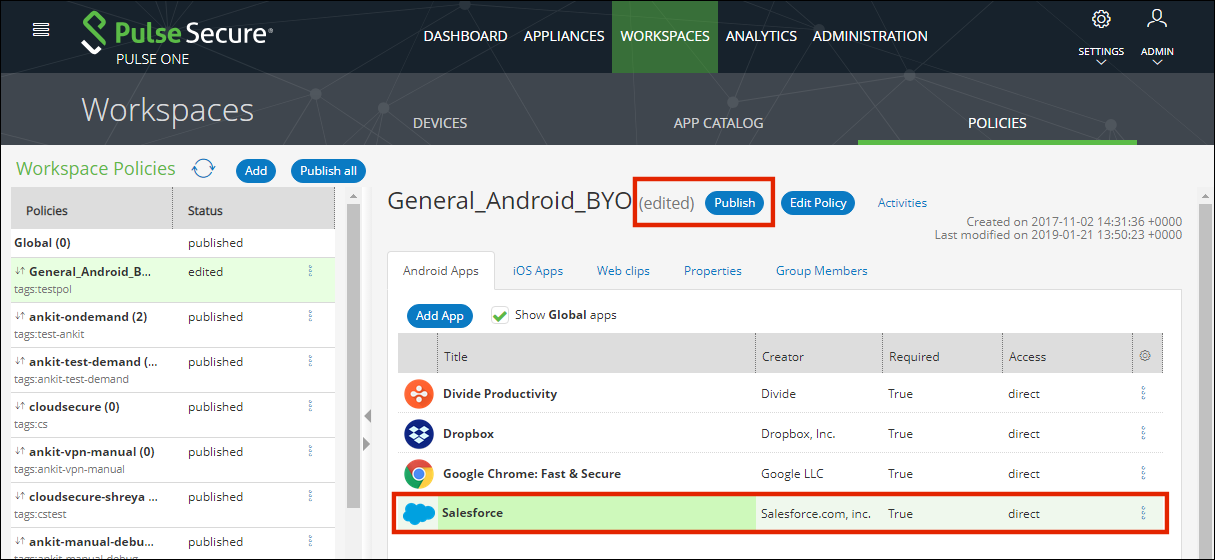
The Publish confirmation dialog appears.
17.Click Yes. The app is published.
This completes adding an Android app to a policy.
Configuring Policy Properties
To set the properties for a policy:
1.Select the Workspace tab.
2.Select the Policies tab.
3.Select the required policy.
4.Click the Properties tab for the policy.
5.Expand the required collection of policies. For example, ActiveSync.
6.Locate the required policy in the expanded list and click its Edit icon.
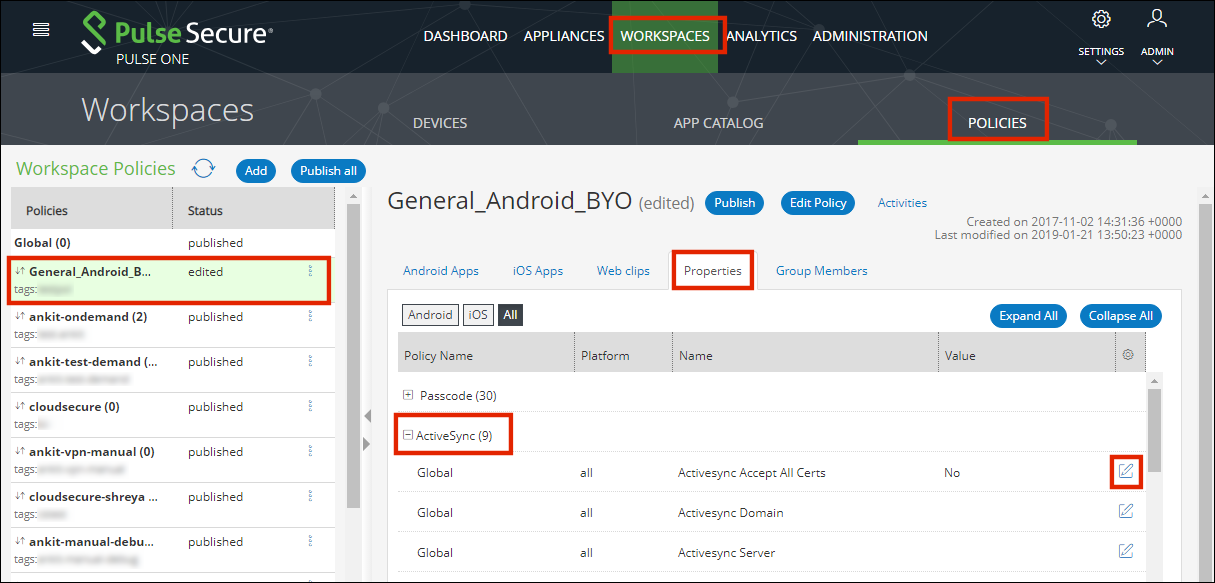
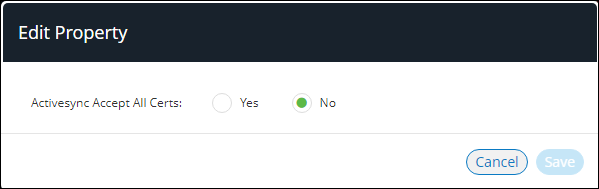
7.Make the required changes and Save each. For example:
Setting a Password Policy
Android password settings are categorized into: quality, expiration and complex. For details of the password policy properties, see Understanding Policy Properties.
Password policies are configured in the admin console and deployed on Android devices.
•Devices running Android v6 (or earlier) support workspace management device passcodes only.
•Devices running Android v7 (or later) support both workspace management device passcodes and work profile passcodes. These can be used simultaneously.
To set a password:
1.Select the Workspace tab.
2.Select the Policies tab.
3.Select the required policy.
4.Click the Properties tab.
5.Expand the Passcode category.
6.Set the following properties for the workspace management device passcode:
•Expiration Days – The number of days for which the passcode can remain unchanged.
•Lock Timeout – The time in seconds where the Workspace will be locked if no Workspace app was in the foreground.
•Max Tries (iOS Factory Reset) – The number of allowed failed attempts to enter the passcode at the device's lock screen.
•Numeric Only – Boolean. If True, the user must to set a PIN.
•Passcode History – When the user changes the passcode, it must be unique within the most recent specified number of entries in the history.
•Passcode Length – The minimum overall length of the passcode.
•Require Special – The minimum count of special characters in a passcode.
For Android, this is used for Workspace Managed Device Passcodes only.
•Require Letters – The minimum count of letters in a Workspace Managed Device passcode.
•Require Lowercase – The minimum count of lowercase letters in a Workspace Managed Device passcode.
•Require Non-Letters – The minimum count of numbers and symbols in a Workspace Managed Device passcode.
•Require Number – The minimum count of numbers in a Workspace Managed Device passcode.
•Require Uppercase – The minimum count of uppercase letters in a Workspace Managed Device passcode.
•Screenlock Password Quality – The screen unlock mechanism. This can be set to none, biometric, password, pattern, pin, pin_complex, alpha, alphanumeric and complex.
•If the device uses a different screen lock type to the one specified by the policy, the device is flagged as non-compliant.
•If the screen unlock type is password, then Passcode Length and Passcode History policies are enforced.
•If the screen unlock type is pin or pin_complex, then Passcode History policies are enforced.
7.For Android v7.0 (or later) you can also set the following properties for the work profile passcode:
•(Work Profile) Expiration Days – The number of days for which the passcode can remain unchanged.
•(Work Profile) Lock Timeout – The time in seconds where the Workspace will be locked if no Workspace app was in the foreground.
•(Work Profile) Max Tries – The number of allowed failed attempts to enter the passcode at the device's lock screen.
•(Work Profile) Numeric Only – Boolean. If True, the user is forced to set a PIN.
•(Work Profile) Passcode History – When the user changes the passcode, it must be unique within the most recent specified number of entries in the history.
•(Work Profile) Passcode Length – The minimum overall length of the passcode.
•(Work Profile) Require Letters – The minimum count of letters in a passcode.
•(Work Profile) Require Lowercase – The minimum count of lowercase letters in a passcode.
•(Work Profile) Require Non-Letters – The minimum count of numbers and symbols in a passcode.
•(Work Profile) Require Number – The minimum count of numbers in a passcode.
•(Work Profile) Require Special – The minimum count of special characters in a passcode.
•(Work Profile) Require Uppercase – The minimum count of uppercase letters in a passcode.
•(Work Profile) Screenlock Password Quality – The screen unlock mechanism. This can be set to none, biometric, password, pattern, pin, pin_complex, alpha, alphanumeric and complex.
•If the device uses a different screen lock type to the one specified by the console, the device is flagged as non-compliant.
•If the screen unlock type is password, then Passcode Length and Passcode History policies are enforced.
•If the screen unlock type is pin or pin_complex, then Passcode History policies are enforced.
8.After the password policy is complete, Publish the policy to all devices that use it.
If a user has not defined a screen lock in his device, then the password policy defined by the admin will be forced to the user's device.