System Controls
In this section:
- About System Controls
- Uninstall Control Items
- Service Control Items
- Event Log Control Items
- Process Termination Control Item
About System Controls
Use System Controls to control the removal or modification of applications and processes, the management of specific services and the clearing of named event logs. Controls can be applied to elevate or restrict access to the specified item.
Restricting or elevating the ability to install or uninstall, modify or repair desktop applications for Windows 10 applies to MSI and .exe based installers accessed via the Control Panel Programs & Features view. From Application Control release 2020.2, assigned permissions are also supported within the Windows Settings Apps and Features view.
System Controls are available on User Privilege node for each rule group.
Add System Controls
- Select the User Privileges node for the required rule group.
- Select the System Controls tab.
- Click Add Item and select the required system control:
For Process Rules, only Process Termination items can be added.
- Complete the required details and click OK.
- From the policy column, select the required option:
- Builtin Restrict - Always restrict access to the named item.
- Builtin Elevate - Always allow access to the named item.
- Configure further items by clicking Add Item in the Privilege Management ribbon and selecting the required option.
-
Click the Click here to set the messages displayed when a user is restricted from accessing system controls link to configure the messages that display when a user attempts to uninstall a restricted program or clear a restricted event log.
For further information, see Message Settings.
Click the Add Ivanti, Inc. Components and Dependencies button to automatically pre-populate the Uninstall, Service, and Event Log control items configurations with an AppSense*. Other required dependencies are also added. This is useful when restricting admin privileges to prevent any critical agent components being changed.
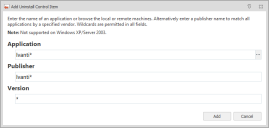
Uninstall Control Items
Application Access Control must be enabled before configuring an Uninstall Control Item. For further information, see Policy Settings.
Use this option to allow or restrict installed applications from being uninstalled when the rule conditions have been matched. Uninstall Control Items are configured by defining which applications are controlled. Further validation can be applied to target a named publisher and specific application versions. To allow or restrict all applications from a publisher, enter a * in the Application field combined with the publisher name.
For an example of using the Uninstall Control Item, see Elevating a Group - Example, Allow Uninstall of Microsoft OneDrive.
AppSense Uninstall Control Items
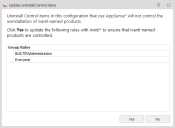
The AppSense company name has changed to Ivanti and because of this, Application Control configurations that include AppSense* uninstall items will not control Ivanti products that previously used the AppSense name.
When a configuration that contains AppSense* uninstall control items is opened in a 10.1 FR1 (or later) console, a dialog displays. The dialog offers an option to automatically add Ivanti* to all rules that contain AppSense*. Uninstall controls function by matching the name and publisher that appear in Programs and Features. Agreeing to the automatic update ensures that, when the configuration is deployed to a rebranded Application Control 10.1 FR1 (or later) agent, AppSense products that have been rebranded to Ivanti remain subject to the same uninstall controls.
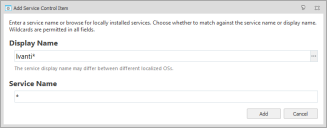
Service Control Items
Use this option to select which services can be modified, stopped, started and restarted when the Rule conditions have been matched.
The Agent Service is the only service that cannot be restarted once stopped.
Service Control Items are configured by specifying the service name or the name by which the service is known. The service display name may differ between different localized Operating Systems.
For an example of using the Service Control Items, see Preventing the Windows Firewall Service from Being Stopped.
Event Log Control Items
Use this option to select which event logs can or cannot be cleared when the Rule conditions have been matched. Event log control items are configured by selecting the name of the log or logs to be controlled.
For an example of using the Event Log Control Items, see Preventing the System Log from being cleared.
Process Termination Control Item
Use this option to protect processes, such as antivirus software from termination by all users, including administrators. Users can still stop processes gracefully, for example, by clicking close in an application UI, but they cannot forcibly terminate a process, such as ending a task from the Details tab in Task Manager. An individual file can be specified or all processes in a particular folder can be targeted.
Optionally, add Metadata to include additional criteria for matching files and folders.
For further information, see Metadata.