Trusted Agents
Trusted Agents offer cross-network access between CSM servers and other private resources, such as LDAP directories, mail servers, and relational databases. Enabled Trusted Agents connect to CSM servers using firewall friendly protocols. The CSM servers then call Trusted Agents to perform operations on their behalf.
For example, Trusted Agents:
- Provide CSM SaaS customers secure access between resources on their private network and the Cherwell data center.
- Enable secure access to private resources across networks in your organization.
- Enable secure access between a Cherwell partner's CSM network and private resources on your network.
The following diagram provides an example of one possible Trusted Agents configuration. While other deployment architectures are possible, this diagram provides a simple visual representation of the relationship between the components.
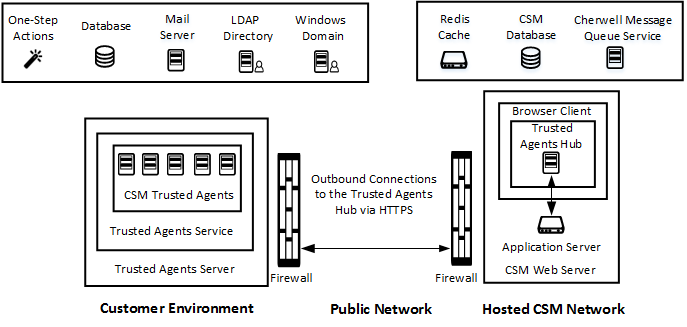
Features That Can Use Trusted Agents
Trusted Agents support integration with several different kinds of private resources. The table below summarizes these supported types of resources and the CSM operations that can be performed with each. You can create service groups to control which private resources use Trusted Agents and to route requests to each service group. For more information, see Configure Trusted Agents Service Groups.
| Private Resource Type | CSM Operations |
|---|---|
|
All email operations within CSM. |
|
| LDAP Directory |
LDAP Authentication. LDAP-mapped user import. LDAP-mapped Business Object import. |
| One-Step Actions |
The following Action types:
|
| External databases (relational database) |
Bulk import of mapped Business Objects.
Linked data imports are not supported at this time.
|
| Windows Domain |
Windows Authentication. |