Patch Summary
The grid on the Ivanti Neurons Patch Intelligence homepage contains a list of all the latest validated patches, listed in date order by default. The columns are grouped into categories so you can easily focus on the relevant data; Summary, Reliability & Social, and Threat & Risk. You can customize which columns are on show and the order of the data by filtering, sorting, or searching by keyword.
You can customize the grid view using the Column Chooser  . Available columns are:
. Available columns are:
Id: The advisory ID. Click to open the Patch Details page.
Name: The advisory name. Click to open the Patch Details page.
The following icons may display before the name: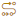 - Patch has been superseded.
- Patch has been superseded.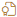 - Patch is an Extended Security Update (ESU). To use this patch you need an ESU subscription.
- Patch is an Extended Security Update (ESU). To use this patch you need an ESU subscription.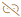 - Applicable only to Linux. Indicates a single package that has no parent advisory.
- Applicable only to Linux. Indicates a single package that has no parent advisory.
Platform: The platform that the patch applies to; Windows, macOS, or Linux.
Unpatched Devices: The number of devices that do not have the patch installed. Click to open the Unpatched Devices tab on the Patch Details page. This column is populated when you have a connector setup, or, when the Ivanti Neurons agent is reporting patch scan data. Filter by: Select All, No data, 0, 1-9, 10-49, 50-99, 100+.
Displays the number of devices used across tenants. The icon ![]() shows the information in the column is not as per specified scope. A banner also indicates this on the top of the page.
shows the information in the column is not as per specified scope. A banner also indicates this on the top of the page.
Date: The issue date of the patch. Filter by: Show all, Last 3 days, Last 14 days, Last 30 days, Last 60 days, Last 365 days, Custom range.
Vendor: The name of the software vendor that issued the patch.
Download Status: The download status for the patch:
- Automatic: The patch can be automatically downloaded from the vendor and is ready for deployment.
- Sideload Required: The patch file cannot be automatically downloaded from the vendor and requires the patch file to be manually sourced and uploaded to Ivanti Neurons before it can be deployed to the endpoint. This process is known as sideloading.
- Sideload in Progress: The patch content has been selected for sideloading and the file is being uploaded to Ivanti Neurons.
- Sideloaded: The patch file has been uploaded to Ivanti Neurons and is ready for deployment.
- Unavailable: The patch is no longer available from the vendor.
You can filter the Download Status column to display only the patches that require sideloading. Learn more about Patch Sideloads.
Reliability: Helps to determine the stability of the patch. Patch Intelligence gathers data from a variety of sources to provide a confidence score for updates to supplement your patch testing efforts. It is derived from the number of successful and failed installs, with other stability metrics, such as Reported issues from vendors or users, to categorize the patch into one of the following:
- Green: Excellent - this represents patches that have a 100% install success rate
- Green: Very High
- Green: High
- Amber: Good
- Amber: Medium
- Amber: Low
- Red: Very Low
- Gray: n/a - too few installation attempts to categorize
My Reliability: Helps determine the stability of the patch. The patches are filtered to show just the devices in your environment, you must have at least one connector to use this column. The score is calculated using the formula successful deployments / total deployments * 10 for all devices in your environment.
Trending score: Trending score indicates the level of social media attention a patch is receiving. A higher trend means there is a higher volume of social media posts.
Reported issues: The number of reported issues for the patch (Windows and macOS patches only). These can be official reported issues by the vendor, such as Microsoft, or customer reported issues. If the patch has received any downvotes the thumb-down icon displays  with the number of votes next to it. Click the number or thumb icon to open the Reported Issues tab on the Patch information page.
with the number of votes next to it. Click the number or thumb icon to open the Reported Issues tab on the Patch information page.
VRR Group: The Vulnerability Risk Rating (VRR) is designed to decipher cybersecurity risk from the widest angle possible. Using an algorithm that intelligently separates, and elevates, the highest risk weaknesses. It takes in the highest fidelity vulnerability and threat data, together with human validation of exploits from penetration testing teams. VRR provides a deeper analysis of context that combats this problem. Subject matter expertise from penetration testers helps build data-driven models to inform the scoring algorithm. VRR represents the risk posed by a given vulnerability, provided as a numerical score between 0 and 10 (the VRR score can be seen on the Patch Details page > CVE tab) it is then represented in one of the following groups:
- 9.00-10 = Critical
- 7.00-8.99 = High
- 4.00-6.99 = Medium
- 0.01-3.99 = Low
The vulnerability and threat components to determine the VVR score and group consist of the following:
- Detailed scanner finding information.
- CVSS base score.
- Industry standard threat intelligence sources such as the National Vulnerability Database (NVD), Common Vulnerabilities and Exposures (CVE), Common Weaknesses Enumeration (CWE), and the OWASP Top 10.
- Curated threat feeds that provide broad coverage and continuous updates on the most active trending exploits being used in the wild.
- Direct input from industry leading penetration testing teams about newly validated exploits.
CVSS: Highest NVD (National Vulnerability Database) CVSS (Common Vulnerability Scoring System) score taken from the latest version of all CVEs associated with the patch. If v4 is not available the v3, v2 score is used. If no score is available No data displays. The score range is from 0.1 to 10.
NIST (National Institute of Standards and Technology) can take up to 2 weeks to update their website.
CVE Count: The number of CVEs the patch contains. If at least one CVE for the patch that has been exploited, a bug icon displays  . Click the icon to open the Patch Details page for more details.
. Click the icon to open the Patch Details page for more details.
Vendor Severity : The patches are categorized to one of the following types:
- Security: Critical, Important, Moderate, Low, Unassigned
- Non-Security: Critical, Important, Moderate, Low, Unassigned
Filter, Sort, Search and Export
You can search, sort, and filter the Summary grid based on a number of attributes.
- To apply a filter on a column select the filter icon
 to display the list of predefined attributes.
to display the list of predefined attributes. - Select the attributes you want to filter on and select OK.
- Once a filter has been applied to a column, the filter name displays in the Smart filters section above the Summary grid, and the Filter button displays an orange dot
 .
.
To remove a single applied filter, select X next to the filter name. To remove all applied filters select Clear filters.
You can apply filters to the Summary grid and save the customized view as a Smart filter.
- Apply column filters, select Smart filters in the smart filters section.
- From the Smart filters drop-down menu, select Add new smart filter from current.
- On the Add new smart filter dialog, enter a Title for the smart filter. The filters that have been applied are listed below the Title.
- Select Add. A toast notification appears in the top right to inform you if the filter has been created successfully. The filter is saved to the list of smart filters for reuse.
To delete a smart filter select Smart filters, from the drop-down menu select Delete existing smart filter, from the list select the filter you want to delete. On the confirmation dialog select Delete to remove the filter from the saved list.
Select the sort icon in any column header to sort into ascending (
in any column header to sort into ascending ( ) or descending (
) or descending ( ) order. To remove the sorting, right-click the column header and select Clear Sorting from the context menu.
) order. To remove the sorting, right-click the column header and select Clear Sorting from the context menu.
Enter a keyword into the Search field to only show patches that contain the keyword. The keyword is matched to any case-insensitive text found from within all of the patches, for example; CVE numbers, patch names, blue screen, and so on.
Example search use cases:
- As a security engineer, I want to supply a CVE to Patch Intelligence to understand what patch I need to have my IT Ops team apply to mitigate the vulnerability. The searching functionality can be an asset to both the Security and Ops teams by allowing them to search for CVEs and see which patches are required.
- As a support technician, I want to know whether a patch is available to fix an issue with PST corruption in Outlook 2016 occurring in conjunction with error 0x80040119. The ability to search benefits the support staff who can search for symptoms or issues around a particular patch.
You can choose to export: selected patches, all CVEs for selected patches, or all CVEs. The data is exported in CSV format to help with your patch reporting requirements. The CSV list of CVE IDs can be imported into other products, such as Ivanti Security Controls and Ivanti Endpoint Manager.
- On the Patch Intelligence Advisories page, apply any required filters.
- Select the check boxes next to the patches you want to export (unless you want All CVEs)
- Select Export.
- From the Export drop-down menu select one of the following:
- Selected Patches: Select the check boxes for the patches that you want to include in the CSV file.
- All CVEs for selected patches: Select the check boxes for the patches that you want to include all CVE IDs in the CSV file.
- All CVEs: All CVE IDs for the patches in the Summary grid will be included in the CSV file. Only patches matching the filters applied, either at the Advisories, chart, or summary grid level, will be included in CSV file.
- The CSV file is created and saved to the downloads folder.