Create Policy Goals
Before creating your first Device Control policies, you should develop goals for those policies. Device Control is very flexible and can help you meet those goals regardless of what they are.
When shaping your policy goals, divide planning into two parts:
- Review Organizational Data
Before you create policies, you need to gather information that will help you shape them. - Use that Data to Shape Your Policies
After reviewing your data, you should have a bigger picture of who is using what devices in your organization, and with what purpose. Now you should know what policies are needed.
Use the Policy Planning Worksheet as a template for creating your policies.
If your organization already has a written security policy, determining your Device Control policy goals should be straightforward. Simply identify the authorized use cases in the policy and make a list of them. You can then create a Device Control policy for each case. If your organization does not have a written security policy, you should develop one.
Determine Your Security Category
Device Control is used successfully in organizations ranging from minimum to maximum IT security. Before planning your Device Control policies, determine your organization security category. Knowing this information can help you determine policy settings when you're unsure what they should be.
Organizations typically fall into one of three categories:
- Permissive
These organizations have few Device Control enforcement requirements. Their primary goal is usually auditing and reporting of user activity or resolving a specific issue, such as limiting USB storage devices to read-only access. The written data security policy at these organizations is usually informal or brief. External regulations and compliance concerns are minimal or non- existent.
- Moderate
These organizations usually have a written data security policy in place, and they want to enforce that policy without relying on voluntary user compliance. Their goal is to prevent any unauthorized usage. However, they allow exceptions in authorized cases, resulting in maximum organizational productivity. These organizations typically have external audit or compliance requirements, such as data encryption (including data transferred onto USB flash drives).
- Stringent
These organizations deal in confidential information, and are typically monitored either internally or externally by a third party. The goal of these organizations is to prevent device usage except for cases authorized by their data security policy. Device usage may be restricted to encrypted devices, and every file transferred to or from devices is saved and reviewed.
Review Device Events
An important part of Device Control policy planning is researching how many policies you need to create. Reviewing your Device Event Log Queries provides useful information for determining this number.
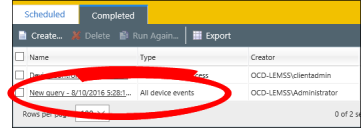
To Review Device Event Log Queries:
- Select Review > Device Event Log Queries.
- Select the most recent query for All Device Events (in the Type column).
- If necessary, click Create to make a log query. Make sure the query is configured to log all device events.
- If you've already create a query that logs all device events, you can click Run Again to update the results.
The latest Device Event Log Query displays.
How Does This Information Help Me?
A Device Event Log Query displays all instances of a device connecting to your endpoints since you enabled Audit mode for your Global Device Control policy. It helps you by displaying:
- Every type of Device Class that's operating in your network. By counting how many different class types are listed, you can make a rough estimate about the minimum number of Device Control policies you need. Notate each Device Class that your organization uses in the Policy Planning Worksheet.
- Every specific model of device that's been connected to your endpoints. If you find that a specific device class has many different types of models connecting, that's a good indication you need to create polices that target Device Collections, which are smaller groups of devices in a class. For example, you may determine that some devices in a Device Class are approved for company use, but others in that class are not, so you'll need two different policies. Notate Device Classes that need to be separated into Device Collections in the Policy Planning Worksheet.
- The Active Directory users responsible for connecting the device. This information is helpful for determining who requires what permissions when creating policies. Also, it can help you identify users who don't use devices responsibly. Use this information for determining who a policy should be to in the Policy Planning Worksheet.
Review Default Policies
During planning, you can benefit from reviewing the settings configured in the default Device Class Policies.
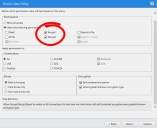
To Review Default Policies:
- Select Manage > Device Control Policies.
- From the page list, expand a default policy to view its settings (as depicted below). Repeat this process for each default policy.
How Does This Information Help Me?
- When you transition from Audit mode to Policy enforcement mode (in the upcoming phase), your endpoints will enforce the default policies until you enable your custom policies. Knowing how your users can interact with devices during this transition is helpful.
- If you're having trouble getting your custom policies to work later, you can use these default policies as a reference for troubleshooting your custom policies.
We do not recommend editing the default policies. We recommend leaving the default settings in place so that if you have to troubleshoot custom Device Control policies, you have the default policies to fall back on while you troubleshoot.
Determine Policy Requirements
Determine a few things before you plan your policies:
- What devices do I need policies for?
- Find out what devices are used in your organization. You need a policy for each device class that's used. See Review Device Events to find information that helps you determine how many policies you need.
- After getting a general idea of how many policies you'll need, learn the different Policy Types Policy Types. This info should help you further refine the number of policies you need.
- When and where should the policy be active?
You can configure each of your policies to be active on certain dates and times. Review Policy Enforcement: When and Where to Enforce Policies and then plan your policies to keep unnecessary device use to a minimum.
- What permissions do my users need?
Different users require different access rights. Review Policy Permission Settings: What Permissions to Give Users on What Devices for more information on assigning user access permissions to each of your policies.
- How should I assign my policies?
You can assign policies by user or endpoint. Review Policy Assignment: Who (Or What) to Assign the Policy to to figure out which method is best for you: users, endpoints, or a combination of both.
Policy Planning Pitfalls
There are some common mishaps that occur during policy planning. Don't let them happen to you!
Device Class Policies: Secondary Hard Drives
If your organization has endpoints that use secondary internal hard drives, you need to have a policy that allows access to those secondary hard drives.
The most common endpoint configuration designates:
- The C: drive as the primary operating system (OS) drive
- Any other drives as user and/or application data drives
Windows operating systems classify secondary hard drives in the Removable Storage Device class. Windows does not clearly communicate this classification (for example, Windows displays the secondary drives in My Computer). However, both Windows and Device Control consider secondary drives removable storage devices. Access to these drives is blocked unless allowed by policy.
To restrict the applicability of a policy to these drives, you have some choices:
- One option is to add all models of secondary hard drives into a Device Collection, and then create a Device Collection policy that allows the Everyone user read and write access to those drives, not just an AD user. This option is the most restrictive, but requires the connection of these drives to a managed endpoint to log the device-attached event so the device model can be added to a collection.
- Another option is to create a Device Class policy for the Removable Storage Device class. On the second page of the policy wizard, allow read and write permissions. Do not allow Encrypt permissions in order to prevent accidental encryption of this drive. In the Connections group, select ATA/IDE, and in the Drives group, select Hard drives only. Assign this policy to Everyone. This policy requires less effort, but is not quite as restrictive. The OS has no way of differentiating between IDE and EIDE connected drives. They are actually the same bus, but the connector is on the outside of the case instead of the inside. A user could connect an EIDE drive and have access to that drive. Also, if you have SCSI connected drives, you must create a second policy, identical to this example except for the bus connection setting.
All Policy Types: Encryption Policy
The encryption options available when creating policy are a little confusing, so we have more detail for you here.
Need instructions on how to set to set encryption permissions? See Encryption Scenarios.
Permission Encryption Options vs. Encryption Options
- Permission Encryption Options
These options (Encrypt and Decrypt) determine whether a user has permission to Encrypt or Decrypt devices.
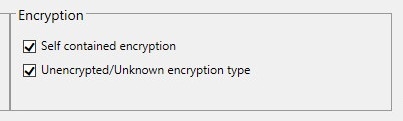
- Encryption Options
These options determine how the user can interact with a device that is:
- Self contained encryption, a device that has encryption contained to the individual device. Only users with a password can access encrypted information on the device.
- Unencrypted/Unknown encryption type, a device that does not have encryption or has an encryption type unrecognized by Device Control control.