Learn Device Control Concepts and Policy Features
Before you begin planning your policies, review the core ideas behind Device Control. Understanding these ideas helps you create a comprehensive plan.
Device Control Concepts
Before planning your policies, you should understand some of the larger concepts behind Device Control.
The purpose of Device Control is to allow your users to access devices needed to do their job, while blocking use of devices that present unnecessary security risk.
These goals are accomplished by using Device Control Policies, which are sets of rules that determine:
- Which specific devices a user can access (or cannot access)
- When users can access a device
- What permissions the user has on a device (read access, write access, etc.)
- The physical ports that can be used to connect a device
- The object used to assign a Device Control Policy (users or endpoints) There are four types of Device Control Policies:
- Device Class Policies
- Device Collection Policies
- Media Collection Policies
- Port Control Policies
For more information on these, see Policy Types.
Device classes are categories created by Microsoft to sort similar hardware devices into logical groups. Device Control uses these categories to block or permit device use.
Within Endpoint Security, hardware devices are classified into Device Classes. When a device is connected to a Windows endpoint, that device registers itself with Windows as one or more device classes.
Some examples of device classes include:
- Biometric Devices
- DVD/CD Drives
- Printers
- Removable Storage Devices
For a list of all Device Classes supported, see Supported Device Classes.
You can view device classes in Endpoint Security by selecting Manage > Device Library. View them in the Device Browser.
Some device classes, such as Removable Storage Devices, are so diverse that they are difficult to organize. For example, the Removable Storage Device class can include:
- Internal secondary hard drives
- External hard drives
- USB flash drives
Because of these large categories, Device Control includes Device Collections, which are smaller groups that you can create within the Device Library.
You can create Device Collections by right-clicking an existing Device Class.
While enforcement mode is enabled, Device Control operates on a default-deny principle . This principle dictates that if no policy for a device exists, that device is blocked from use.
Some implications of this principle are:
- You, the administrator, must create a policy for each device that your end users need to complete their work. End users can only use devices that you explicitly approve.
- Any device that you have no policy for is blocked. The default-deny principle protects your organization from unknown devices.
Device Control Policy Types and Options
When planning your policies, it's important to understand the different policy types at your disposal, along with the options they offer.
Policy Types
Device Control allows you to create four different policy types. Review this section to understand each policy type and how they fit into your organization security policy.
The policy types are:
Device Class Polices are policies based on Device Classes. These policies control user access to a generic type of endpoint hardware. This is the main type of policy you'll be creating.
Create Device class policies by selecting Manage > Device Control Policies and then selecting Create > Device class policy from the toolbar.
Default Device Class Policies
Device Control comes pre-configured with a default Device Class Policy for each Windows Device Class. View these policies from Manage > Device Control Policies.
After transitioning from Audit mode to Policy enforcement mode (which will happen later in Enable Enforcement), these default policies are in effect. They are configured to be minimally intrusive. Their default settings assign full Read/Write permissions to all users.
We've provided these policies so that you can deploy your own policies individually. The default policy remains in effect until you disable it in favor of your custom policy.
We do not recommend editing the default policies. We recommend leaving the default settings in place so that if you have to troubleshoot custom Device Control policies, you have the default policies to fall back on while you troubleshoot.
This policy type is similar to a Device Class Policy. However, instead of targeting an entire class, it targets Device Collections that you've created.
This policy type is useful when a Device Class Policy would be ineffective due to variety within the class.
Let's simulate a scenario where you want to create a policy for the Removable Storage Devices class. This class includes many different devices, including internal hard drives, USB flash drives, and external hard drives. However, you want to treat each of these devices differently:
- Internal Hard Drives: You want to allow all users unlimited access.
- USB Flash Drives: You want to allow all users read-only access.
- External Hard Drives: You want to limit user copying to less than a gigabyte a day.
For cases like the one above, instead of creating a single Device Class Policy, you would instead create three Device Collections, and then create three Device Collection Policies. These policies allow more flexibility within a given Device Class.
The remaining policy types are media collection policies and port control policies. These policy types are used less than device policies.
- Media Collection Policies
Use these policies to control access to data on CDs and DVDs.
- Port Control Policies
Use these policies to control access to endpoint physical ports, such as USB ports, FireWire, Bluetooth, and so on.
Policy Options
Regardless of policy type, policies are created by completing a wizard. This wizard contains common options. You can review what those options are here.
When planning your policies, consider when and where you want them enforced. During policy creation, Device Control offers the following policy enforcement options:
- Always
This simple, straightforward option enforces the policy at all times once applied. This is the mostly commonly chosen option, but the policy is applied without regard to context. - Online Only
Online policies are enforced when the endpoint is within your organization's network and can contact the Endpoint Security Server. - Offline Only
Offline policies are enforced when the endpoint is disconnected from your organization's network. This policy is best applied to users and endpoints that are mobile; field workers who carry laptops for example.Online and Offline policy enforcement is best used in tandem, applying them to the same users and groups. This enforcement plan allows you to apply a restrictive policy when the endpoint is off site, preventing field workers from copying data off their endpoints when at customer sites.
- Scheduled
Scheduled policies are enforced during days and times that you choose. This policy enforcement option restricts device use during office hours. - Temporary
This enforcement option temporarily assigns a user special permissions for a short time before revoking them.Normally this enforcement option isn't used during initial deployment of Device Control, and is best-used for daily administration—for example, when allowing access to a USB flash drive from a conference room computer.
However, organizations with high employee turnover may prefer Temporary policies rather than Always policies. For example, you might:
- Assign users permissions six months to a year.
- Either extend or revoke the policy when the initial period ends.
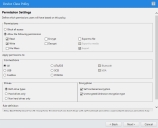
Regardless of the policy types that you create, they all include Permission Settings. These settings let you choose different access rights for users and endpoints that are assigned the policy. The permissions that are available change according to device class, but the most important settings are:
- Permissions for users (or endpoints) assigned this policy, including standard Windows permissions like read and write access, and more specialized access like the ability to encrypt devices.
- Need help with creating policies that include encryption permissions? See Encryption Scenarios.
- The permissions available vary according to policy type and device class. See Policy Permission Settings: What Permissions to Give Users on What Devices for more information.
- Connections (and other settings), which specify that the permissions that you've selected apply to only devices that have connected over a specific type of physical port. For example, you can create a policy for secondary storage devices that are connected internally using a SCSI port.
There many be additional options for specifying what devices that the permissions apply to, such as All Policy Types: Encryption Policy.
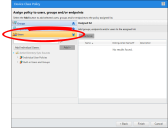
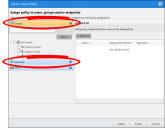
Before creating your policies, determine how you're going to assign them to your organization. Earlier in this best practice guide we demonstrated how to Synchronize With Active Directory. You can now use your active directory objects to assign Device Control policies. You can assign policies using one of two methods:
Assignment by Users
Typically, Device Control policies are centered around people, not machines. Therefore, we recommend assigning Device Control policies by user groups rather than endpoints. Assignment by user groups improves policy distribution and enforcement efficiency.
This method of assignment can be a shift in thinking, especially for IT organizations that usually manage other functions by endpoint, such as patching or antivirus. However, assignment by user ultimately reduces your administrative workload.
Why Should I Apply Policies to Users and Not Endpoints?
- When a policy is applied only to a user or user group, it applies to those users on all endpoints they use. In contrast, when a policy is applied only to an Organizational Unit, endpoint, or endpoint group, it applies to all users on those specific endpoints.
- When a policy is applied to a combination of users and endpoints, it applies only to those users when they are logged onto those endpoints.
- A policy that's assigned to users is identical on every endpoint. Therefore, it can be distributed as a single policy. In contrast, policies assigned to endpoints are unique; a policy file per policy must be distributed. When assigning a policy directly to a large number of endpoints, many policy files are created and transmitted, resulting in increased network traffic.
- Assigning by user ensures you won't have to reassign policies when hardware is upgraded, replaced, or moved.
Assignment by Endpoint
Although we typically recommend assigning policies by user and user group, you can also assign policies to endpoints and endpoints groups. We recommend assigning Device Control policies by endpoint instead of users only in specific circumstances.
When Should I Apply Policies by Endpoint?
Examples of when you should apply a Device Control policy to an endpoint/endpoint group instead of a user include:
- Apply policies directly to endpoints such as a lobby kiosk that only has guests using it.
- Apply policies directly to servers that have a specialized piece of hardware not used with other servers.