Using Patch Content
In this section:
- About Patch Content
- The Patch Content Page
- Working With Content
- The Patch Status Page
- Working with Content Items
The term patch content encompasses all updates across all endpoints registered to the Ivanti Patch and Remediation Server.
Within Ivanti Patch and Remediation, content consists of:
- The content description.
- Signatures and fingerprints required to determine whether the content is patched or not patched.
- Associated package or packages for performing the patch.
Packages contain all vendor-supplied updates and executable code used to correct or patch security issues.
The following graphic illustrates the relationship between content and packages. Typically, a single content item is shared by multiple endpoints on multiple operating system platforms. There may be a series of separate patches to remediate the same content in different environments. The separate patches are grouped in packages identified by their respective product or OS. As a result, a series of packages may be included for one content item.
Patch Content and Package relationship:
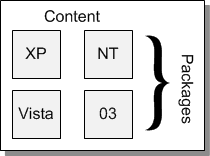
About Patch Content
The various pages pertaining to content display a listing of known vulnerabilities, software updates, and other patch content. Once reported and analyzed, the content is distributed to your Ivanti Endpoint Security server through the Global Subscription Service agent.
The agent installed on each endpoint checks for known content using the Discover Applicable Updates (DAU) task. The DAU runs an inventory scan and sends the results back to the Ivanti Endpoint Security server, which compares it with the list of known content. If the endpoint is found to be missing security items, a deployment can be set up to resolve the issues.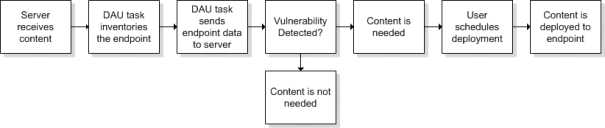
Defining Content Structure
The structure of a content item allows the ability to create one patch applicable for many different operating systems and software versions. This allows for different packages and signatures capable of identifying the presence of patch files within an endpoint.
As depicted in the following diagram, for each content item you can have more than one signature. For each signature, you can have multiple fingerprints and pre-requisites. However, you can only have one package per signature.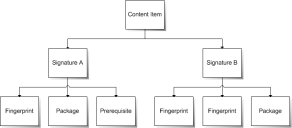
Content Item
A content item is the container for the entire object. All properties set for the content item are viewed in content pages. Each security content item can have one or more signatures.
Signatures
Signatures recognize specific combinations of installed software in an operating system. Vulnerabilities usually contain multiple signatures to compensate for variances within applications. Frequently, a patch will require different executables, dynamic-link libraries, and switches in order to run or detect the patch within different operating systems.
Fingerprints
A fingerprint can represent a unique file, folder, registry key, or other data value somewhere within a system. Each signature can contain one or more fingerprints detecting if a patch is present in the system.
Prerequisites
A prerequisite is a signature belonging to another vulnerability with its own fingerprints.
Adding a prerequisite to a signature requires the prerequisite be met before analyzing the signature for the current patch. If that signature's prerequisite is met, the agent will analyze the fingerprints of the current signature, otherwise they will be ignored and the patch will not be applied to the device.
Packages
The package contains the actual files used to update or install software on the system. Each package contains the script commands for installing the package files or running the executable that installs the patch.
Vulnerabilities
Vulnerabilities are fixes for critical security issues. They are categorized by content type, which indicates the level of need for an endpoint to have the vulnerability deployed and installed.
Vulnerabilities are classified into the following content types:
Critical: Ivanti or the product manufacturer has determined that this patch is critical and should be installed as soon as possible. Most of the recent security updates fall in to this category. The patches for this category are automatically downloaded and stored on your Ivanti Patch and Remediation server.
Critical - 01: Ivanti or the product manufacturer has determined that this patch is critical and should be installed as soon as possible. This patch is older than 30 days and has not been superseded.
Critical - 05: Ivanti or the product manufacturer has determined that this patch is critical and should be installed as soon as possible. This patch has been superseded.
Critical - Intl: An international patch, where Ivanti or the product manufacturer has determined that this patch is critical and should be installed as soon as possible. Most of the recent international security updates fall in to this category. After 30 days international patches in this category will be moved to Critical - 01.
Software Content
Software content consists of content intended to keep software up to date. You can review software content in the following categories:
Service packs: Collections of software fixes and enhancements that apply to installed software.
Software installers: Installers for third party software.
Updates: Non-critical updates to installed software.
In addition to the categories listed above, you can also view a list of all available software security content.
Other Content
Other content includes items that are not directly related to patching an endpoint or updating software. It is categorized by content type, which indicates the level of need for an endpoint to have the vulnerability deployed and installed.
Other content items are classified into the following content types:
Detection Only: These security content items contain signatures that are common to multiple vulnerabilities. They contain no associated patches and are only used in the detection process.
Informational: These security content items detect a condition that Ivanti or the product manufacturer has determined as informational. If the report has an associated package, you may want to install it at your discretion.
Policies: These security content items apply security policies to an endpoint.
Recommended: Ivanti or the product manufacturer has determined that these content items, while not critical or security related, are useful and should be applied to maintain the health of your endpoints.
Task: These security content items contain tasks which administrators may use to run various detection or deployment tasks across their network.
Virus Removal: This security content items contain packages which administrators may use to run various virus detections across their network. Anti- Virus tools and updates are included in this category.
About Custom Patch Lists
Custom Patch Lists are a Patch and Remediation feature you can use to create lists of patch content useful in your enterprise.
Ivanti Endpoint Security Patch and Remediation has access to a large repository of patch content. Due to the repository size, users can often have difficulty tracking the patch content they are working with.
You can create Custom Patch Lists from either the Patch Content page or the Groups page Vulnerabilities/Patch Content view.
Custom Patch List Usage Tips
- For content that is used frequently in your enterprise, create a Custom Patch List containing commonly used patch content, and maintain it as your enterprise network changes. As endpoints are updated with new hardware and software, you can update the list to include new patches, while removing old, superseded patches.
- For content that will only be deployed once, create a Custom Patch List containing only the patch content needed for that deployment. For example, you can populate a Custom Patch List with only content released on Patch Tuesday, and then use the content list to deploy it. Afterward, you can leave the Custom Patch List unedited, leaving a record or the patch content released and deployed for a month.
- Use Custom Patch Lists to cache patch content from the Global Subscription Service. Caching using a custom list is a good way of downloading a group of patches.
- Use Custom Patch Lists to test new patch content deployments. You deploy custom patch lists to a group of test endpoints before deploying them in a production environment.
- Use Custom Patch Lists for reporting purposes. Since these lists contain only patch content relevant in your enterprise, they are a great way to report deployment progress and status.