Working with Discovery Scan Jobs
The Assets menu item allows you to discover network assets. This task is available from the navigation menu under Discover.
To discover network assets using a Discovery Scan Job , refer to the following items:
Discovering Assets by Discovery Scan Job
Use a Discovery Scan Job to finds endpoints and devices in your network. You can use this job type to schedule future jobs, recurring jobs, or jobs that only use certain discovery options.
Prerequisites:
- Ivanti Endpoint Security is installed and initial replication has completed.
- Windows endpoints must be configured to allow discovery scanning. For additional information about configuring Windows endpoints for discovery, refer to Configuring Endpoints for Discovery
Important: Windows operating systems can have security features that block a Discovery Scan Job. On Windows platforms, the target endpoints must have both Network discovery and File sharing enabled. If the target endpoints do not have these security features enabled, they are not discovered during a Discovery Scan Job. See Installing Agents by Agent Management Job.
Configuration
You can create a Discovery Scan Job from the navigation menu or by clicking a toolbar button on the Job Results page.
- Select Discover > Assets to begin using the wizard. Complete one of the following steps to begin configuration.
- Select Review > Asset Discovery Job Results.
- Select either the Scheduled, Active, or Completed tab.
- Select Discover >Assets.
- Select Review > Agent Management Job Results.
- Select either the Scheduled, Active, or Completed tab.
- Select Discover >Assets.
- [Optional] Type a new name in the Scan job name field.
By default, new Discovery Scan Jobs are named New Discovery Job, followed by the server date and time, which is formatted according to your server's Client Admin user locale setting.
- Schedule the job.
Use one of the following methods.
Tip: During job scheduling, you can use the following shortcuts:
- Click the Calendar icon to select a Start date. Selecting a date automatically fills the Start date field.
- Click the Clock icon to select a Start time. Selecting a time automatically fills the Start time field.
Method
Steps
To schedule an immediate job:
Select the Immediate option.
To schedule a one-time job:
- Ensure the Once option is selected.
- Define a start date by typing a date in the Start date field.
The format must be mm/dd/yyyy. - Define a start time by typing a time in the Start time field.
- The format must be hh:mm followed by AM or PM (if necessary).
- This field supports both 12- and 24-hour time.
Tip: Scheduling a one-time job for a past date and time will launch the job immediately.
To schedule a recurring weekly job:
- Select the Weekly option.
- Define a start date by typing a date in the Start date field.
The format must be mm/dd/yyyy. - Define a start time by typing a time in the Start time field.
- The format must be hh:mm followed by AM or PM (if necessary).
- This field supports both 12- and 24-hour time.
- Define the day of the week the job runs by selecting a day from the Run every week on the following day list.
To schedule a recurring monthly job:
- Select the Monthly option.
- Define a start date by typing a date in the Start date field.
The format must be mm/dd/yyyy. - Define a start time by typing a time in the Start time field.
- The format must be hh:mm followed by AM or PM (if necessary).
- This field supports both 12- and 24-hour time.
- Define the day of the week the job runs by selecting a day from the Run every month on the following day list.
One-time and recurring jobs scheduled for the last day of a 31-day month are automatically rescheduled for the last day of shorter months.
- Click Next.
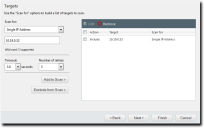
The Targets page opens. - Define targets (endpoints) for the job to locate.
Use one or more of the following discovery methods.Method
Steps
To define targets using a single IP address:
- From the Scan for list, select Single IP Address.
- Type an IP address in the empty field. Wildcards are supported.
For additional information, refer to Defining Targets Using Wildcards. - Select an item in the Timeout list.
The Timeout list defines the number of seconds before a scan fails per attempt due to inactivity for a particular target. Under most network conditions, the Timeout field does not require editing.
Edit the Number of retries list.
The Number of retries list defines the number of times a scan retries on that target if the scan times out.
To define targets using an IP range:
- From the Scan for list, select IP Range.
- In the first empty field, type the beginning of the IP range.
Wildcards are supported. For additional information, refer to Defining Targets Using Wildcards. - In the second empty field, type the ending of the IP range.
Select an item in the Timeout list.
The Timeout list defines the number of seconds per attempt before a scan fails due to inactivity for that particular target. Under most network conditions, the Timeout field does not require editing.
If necessary, edit the Number of retries list.
The Number of retries list defines the number of times a scan retries on that target if the scan times out.
To define targets using a computer name:
- From the Scan for list, select Computer name.
- In the empty field, type an endpoint name in one of the following formats: computernameor domain\computername.
To define targets using network neighborhood:
- From the Scan for list, select Network Neighborhood.
- From the second list, select the desired network neighborhood.
To define targets using active directory:
- From the Scan for list, select Active Directory.
- In the Fully-qualified domain name field, type the DNS domain name of the domain controller you want to scan.
Tip: For example, if your domain controller DNS name is box.domain.company.local, you would type domain.company.local in this field.
- Optionally, in the Organizational Unit field, type the active directory organizational unit string from specific to broad, separating each string with front slashes (such as Techpubs/ Engineering/Corporate)
Tip: The omission of this field returns job results containing the full contents of all the active directory organizational units.
- In the Domain controller field, type the domain controller IP address.
- In the Username field, type a user name that authenticates with the domain controller.
Type the user name in one of the following format: domainname\username or username.
- In the Password field, type the password associated with the user name.
To define targets using an imported file:
- From the Scan for list, select Import file.
- Click Browse.
- Browse to the file you want to use for target discovery.
The following file types are supported: .txt and .csv. - Click Open.
For additional information about how to define targets within an imported file, refer to Defining Targets Within an Imported File.
- Add targets to the wizard list. This list indicates whether defined targets are included in or excluded from the job.
Use one of the following methods.You must include at least one target for Next to become available. You can also delete targets from the list by selecting the applicable check boxes and clicking Remove.
- To include defined targets in the job, click Add to Scan.
- To exclude defined targets from the job, click Exclude from Scan.
For additional information, refer to Editing Targets.
- [Optional] Edit the Targets list.
- To remove targets from the list, select the list item(s) and click Remove.
- To edit targets on the list, select the list item(s) and click Edit.
For additional information, refer to Editing Targets.
- Click Next.
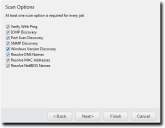
The Scan Options page opens. - Select or clear the desired Scan Options.
The following table defines each Scan Option: - ClickNext.
The Credentials page opens.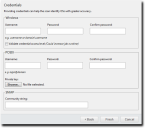
- [Optional] Define Windows credentials for the target.
Type the applicable information in the following fields. - [Optional] Select the Validate credentials access level check box.
Selecting this check box validates the access levels that the entered credentials achieve on scan targets. This information is useful when determining if credentials provided the access necessary for Agent Management Jobs.Selecting this option could increase job run time.
- If necessary, define POSIX credentials (credentials for UNIX-based operating systems).
Type the applicable information in the following fields.Field
Description
Username
A user name that authenticates with POSIX endpoints. Type the user name in the following format: login@domain
Password
The password associated with the Username.
Confirm password
The Password retyped.
- If necessary, define a POSIX private key.
- Click Browse.
- Browse to the applicable .txt file.
- Click Open.
- If necessary, define an SNMP community string that authenticates with network devices.
- Type the applicable community string in the Community string field.
- Click Finish.
The Discover Assets Wizard closes. Depending on how you scheduled the job, the Discover Scan Job moves to either the Job Results page's Scheduled or Active tab.
|
Context |
Steps |
|---|---|
|
To open the Wizard from the toolbar: |
Select Discover > Assets. |
|
To open the Wizard from the Asset Discovery Job Results page: |
|
|
To open the Wizard from the Agent Management Job Results page: |
|
The wizard opens to the Job Name and Scheduling page.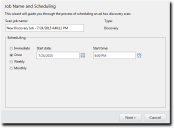
Tip: Repeat this step to add additional targets to the list.
|
Option |
Description |
|---|---|
|
Verify With Ping |
Jobs using this option send ping requests to all network endpoints targeted for discovery. Endpoints that respond to the request are flagged for scanning; unresponsive endpoints are skipped. Endpoints unresponsive to Verify With Ping are not scanned by other selected discovery options. Anti-virus software and host firewalls may block Verify With Ping. If necessary, adjust any antivirus and firewall configurations to permit ping requests. |
|
ICMP Discovery |
Jobs using this option request a series of echoes, information, and address masks from endpoints. Endpoint responses are then compared to a list of known ICMP fingerprints to identify endpoint operating systems. ICMP Discovery is ineffective on endpoints configured to ignore ICMP requests. For best results identifying Windows operating systems, use this option in conjunction with Windows Version Discovery. |
|
Port Scan Discovery |
Jobs using this option perform a limited scan on endpoint FTP, Telnet, SSH, SMTP, and HTTP ports. Based on the application banners found in these ports, endpoint operating systems are generically identified. For best results in identifying Windows operating systems, use this option in conjunction with Windows Version Discovery. |
|
SNMP Discovery |
Jobs using this option request system properties for SNMP devices (routers, printers, and so on) from the management information base. Following credential authentication, SNMP devices are identified. Without authenticated credentials, SNMP devices ignore SNMP Discovery requests. In this event, one of two outcomes occur: the SNMP device is misidentified as a UNIX endpoint or the SNMP device is not detected. Jobs with no SNMP credentials use the public credential by default. |
|
Windows Version Discovery |
Jobs using this option identify an endpoint's specific version of Windows following generic operating system identification during ICMP or Port Scan Discovery. Correct operating system identification is contingent upon authenticated credentials. This option must be used in conjunction with either ICMP or Port Scan Discovery. |
|
Resolve DNS Names |
Jobs using this option acquire the endpoint DNS name through a local DNS server query. These names are displayed in job results for easy endpoint identification. |
|
Resolve MAC Addresses |
Jobs using this option acquire endpoint MAC addresses through endpoint queries. These addresses are displayed in job results for easy endpoint identification. Monitor network inventory reports to prevent MAC address spoofing that may alter the Resolve MAC Addresses results. |
|
Resolve NetBIOS Names |
Jobs using this option acquire endpoint NetBIOS names through WINS NetBIOS mapping. These names are displayed in job results for easy endpoint identification. |
|
Field |
Description |
|---|---|
|
Username |
A user name that authenticates with Windows endpoints. Type the user name in a local format (username) or a domain format (domain\username). |
|
Password |
The password associated with the Username. |
|
Confirm password |
The Password retyped. |
Editing Targets
While configuring jobs, you can edit items included in the Targets list.
Edit Target list items from the Targets page of the wizard.
- From the Targets list, select the check box associated with the item you want to edit.
The Edit button becomes active. - ClickEdit.
The Edit Targets dialog opens.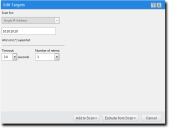
- Based on the type of discovery method, edit the item.
- Type a new IP address in the field. Wildcards are supported. For additional information, refer to Defining Targets Using Wildcards.
- If necessary, edit the Timeout list. The Timeout list defines the number of seconds before a scan fails due to inactivity. Under most network conditions, the Timeout field does not require editing.
- If necessary, edit the Number of retries list. The Number of retries list defines the number of times a discover assets scan retries if the scan times out.
- In the field, type the beginning of IP range. Wildcards are supported. For additional information, refer to Defining Targets Using Wildcards.
- In the field, type the ending of the IP range.
- If necessary, edit the Timeout list. The Timeout list defines the number of seconds before a scan fails due to inactivity. Under most network conditions, the Timeout field does not require editing.
- If necessary, edit the Number of retries list. The Number of retries list defines the number of times a discover assets scan retries if the scan times out.
- In the Fully-qualified domain name field, type the DNS domain name of the domain controller you want to scan. For example, if your domain controller's DNS name was box.domain.company.local, you would type domain.company.local in this field.
- Optionally, in the Organizational Unit field, type the active directory organizational unit string from specific to broad, separating each string with front slashes (such as Techpubs/Engineering/Corporate). The omission of this field returns job results containing the full contents of all the active directory organizational units. View the following figure for an example of how to enter data using Active Directory.
- In the Domain controller field, type the domain controller's IP address.
- In the Username field, type user name that will authenticate with the domain controller. Type the user name in one of the following format: domainname\username or username.
- In the Password field, type the password associated with the user name.
- Add targets to the wizard list. This list indicates whether defined targets are included in or excluded from the job.
Use one of the following methods.- To include defined targets in the job, click Add to Scan.
- To exclude defined targets from the job, click Exclude from Scan.
|
Discovery Method |
Steps |
|---|---|
|
Single IP Address |
|
|
IP Range |
|
|
Computer Name |
In the empty field, type a new endpoint name in one of the following formats: endpointname or domain\endpointname. |
|
Network Neighborhood |
From list, select the desired network neighborhood. |
|
Active Directory |
|
Active Directory Input Example: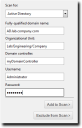
- Review the Targets list.
The Targets list reflects your changes.
Defining Targets Using Wildcards
When configuring a Discovery Scan Job or Agent Management Job, you can define scan targets using wildcard IP addresses. Wildcards are characters that can be used to substitute for any other character or characters in a string. In other words, you can use wildcards to scan for numerous IP address instead of just one. Use wildcards to scan specific IP address ranges.
The following table lists examples of how to define targets using wildcards.
|
Discovery Method |
Step |
Example |
Targets Defined |
|---|---|---|---|
|
To define wildcard IP addresses: |
Type a wildcard IP address using commas (,). Type a wildcard IP address using dashes (-). Type a wildcard IP address using asterisks (*). |
10.1.1.2,9 10.1.1.2-5 10.1.1.* |
10.1.1.2 and 10.1.1.9 10.1.1.2, 10.1.1.3, 10.1.1.4, and 10.1.1.5 10.1.1.0 through 10.1.1.255 |
|
To define wildcard IP addresses using dashes in various octets: |
Type a wildcard IP address using dashes, placing the dashes where applicable. You can use dashes in any octet. |
10.2-4.5.9 |
10.2.5.9, 10.3.5.9, 10.4.5.9 |
|
To define wildcard IP addresses using asterisks in various octets: |
Type a wildcard IP address using asterisks, placing the asterisks where applicable. You can use asterisks in any octet. |
*.6.65.92 10.25.*.* |
1.6.65.92 through 255.6.65.92 10.25.0.0 through 10.25.255.255 |
|
To define wildcard IP addresses using commas in various octets: |
Type a wildcard IP address using commas, placing the commas where applicable. You can use commas in any octet. |
10,12,19.2.5.9 |
10.2.5.9, 12.2.5.9, 19.2.5.9 |
|
To define wildcard IP addresses using a combination of wildcard characters: |
Type a wildcard IP address using dashes, commas, and asterisks. |
10-13.*.12.2,4,7 10.2-4.5,23.* |
10, 11, 12, 13.0-255.12.2, 4, 7 10.2, 3, 4.5, 23.0-255 |