Working with Agent Management Jobs
The Ivanti Endpoint Security console utilizes an Agent Management Job to install or uninstall agents on Windows endpoints. The tasks to do this is available from the navigation menu under Discover.
To work with Agent Management Jobs, refer to the following items:
For additional information on Agents, refer to the Ivanti Endpoint Security: Agent Installation Guide.
Installing Agents by Agent Management Job
You can install agents on network endpoints remotely by using Agent Management Jobs. Installing agents remotely substantially eases your workload, since you do not have to install agents locally.
Prerequisites:
- Verify that your target endpoints are Windows endpoints.
Refer to the Ivanti Endpoint Security: System Requirements Guide for a complete list of supported Windows platforms for endpoints. - Ensure any anti-virus software installed on your target endpoints is disabled.
- Gather the built-in Administrator credentials for endpoints you are installing agents on. Successful job outcome is contingent upon authenticated credentials for this account.
- Configure your server to allow an Agent Management Job. For additional information, refer to Configuring the Ivanti Endpoint Security Server for Discovery Scanning.
- Configure your targets to allow an Agent Management Job. For additional information, refer to Configuring Endpoints for Agent Management Jobs.
Important: Linux, UNIX, and Mac endpoints cannot have agents installed using an Agent Management Job.
Configuration of an Agent Management Job is similar to configuration of a Discovery Scan Job. Configuration occurs in the Install Agents Wizard.
- Begin configuration of the Install Agent Wizard.
Complete one of the following steps to begin configuration.Context
Steps
To open the Wizard without targets predefined:
Select Discover > Assets and Install Agents.
To open the Wizard with target predefined:
- Select Manage > Endpoints.
- Select the endpoints you want to install the agent on.
- From the toolbar, select Manage Agents > Install Agents.
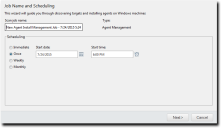
- [Optional] Type a new name in the Scan job name field.
By default, a new Agent Management Job for installation is named New Agent Install Management Job, followed by the server's date and time.
- Schedule the job using one of the following methods.
Tip: During job scheduling, you can use the following shortcuts:
- Click the Calendar icon to select a Start date. Selecting a date automatically fills the Start date field.
- Click the Clock icon to select a Start time. Selecting a time automatically fills the Start time field.
- Ensure the Once option is selected.
- Define a start date by typing a date in the Start date field.
The format must be mm/dd/yyyy. - Define a start time by typing a time in the Start time field.
- The format must be hh:mm followed by AM or PM (if necessary).
- This field supports both 12- and 24-hour time.
Tip: Scheduling a one-time job for a past date and time will launch the job immediately.
- Select the Weekly option.
- Define a start date by typing a date in the Start date field.
The format must be mm/dd/yyyy. - Define a start time by typing a time in the Start time field.
- The format must be hh:mm followed by AM or PM (if necessary).
- This field supports both 12- and 24-hour time.
- Define the day of the week the job runs by selecting a day from the Run every week on the following day list.
- Select the Monthly option.
- Define a start date by typing a date in the Start date field.
The format must be mm/dd/yyyy. - Define a start time by typing a time in the Start time field.
- The format must be hh:mm followed by AM or PM (if necessary).
- This field supports both 12- and 24-hour time.
- Define the day of the month the job runs by typing a day in the Run every month on the following day field.
- Click Next.
The Targets page opens. - Define targets (endpoints) for the job to locate.
Use one or more of the following discovery methods. - From the Scan for list, select Single IP Address.
- Type an IP address in the empty field. Wildcards are supported.
For additional information, refer to Defining Targets Using Wildcards - Select an item in the Timeout list
The Timeout list defines the number of seconds before a scan fails per attempt due to inactivity for a particular target. Under most network conditions, the Timeout field does not require editing.
- Edit the Number of retries list. The Number of retries list defines the number of times a scan retries on that target if the scan times out.
- From the Scan for list, select IP Range.
- In the first empty field, type the beginning of IP range.
Wildcards are supported. For additional information, refer to Defining Targets Using Wildcards. - In the second empty field, type the ending of the IP range.
- Select an item in the Timeout list.
The Timeout list defines the number of seconds per attempt before a scan fails due to inactivity for that particular target. Under most network conditions, the Timeout field does not require editing.
- If necessary, edit the Number of retries list. The Number of retries list defines the number of times a scan retries on that target if the scan times out.
- From the Scan for list, select Computer name.
- In the empty field, type an endpoint name in one of the following formats: computername or domain\computername.
- From the Scan for list, select Network Neighborhood.
- From the second list, select the desired network neighborhood.
- From the Scan for list, select Active Directory.
- In the Fully-qualified domain name field, type the DNS domain name of the domain controller you want to scan.
Tip: For example, if your domain controller DNS name is box.domain.company.local, you would type domain.company.local in this field.
- Optionally, in the Organizational Unit field, type the active directory organizational unit string from specific to broad, separating each string with front slashes (such as Techpubs/Engineering/Corporate ).
Tip: The omission of this field returns job results containing the full contents of all the active directory organizational units.
- In the Domain controller field, type the domain controller IP address.
- In the Username field, type a user name that authenticates with the domain controller.
Type the user name in one of the following format: domainname\username or username.
- In the Password field, type the password associated with the user name.
- From the Scan for list, select Import file.
- Click Browse.
- Browse to the file you want to use for target discovery.
The following file types are supported: .txt and .csv. - Click Open.
For additional information about how to define targets within an imported file, refer to Defining Targets Within an Imported File. - Add targets to the wizard list. This list indicates whether defined targets are included in or excluded from the job.
Use one of the following methods.You must include at least one target for Next to become available. You can also delete targets from the list by selecting the applicable check boxes and clicking Remove.
- To include defined targets in the job, click Add to Scan.
- To exclude defined targets from the job, click Exclude from Scan.
Tip: Repeat this step to add additional targets to the list.
- [Optional] Edit the Targets list.
- To remove targets from the list, select the list item(s) and click Remove.
- To edit targets on the list, select the list item(s) and click Edit.
For additional information, refer to Editing Targets.
- Click Next.
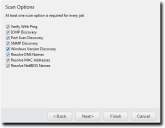
The Scan Options page opens. - Select or clear the desired Scan Options.
The following table defines each Scan Option. - Click Next.
The Agent Options page opens. - Select the desired Agent Options.
These options control which version of the agent is installed on Windows-based endpoints. - Select an agent version from the Agent version list.
The agent versions available for selection are defined by the Agent Version Options , which you can edit from the Options page Agents tab. For additional information, refer to Agent Versions.
- Select the modules you want to install with the agent.
Select the check box associated with the module(s) you want to install. - [Optional] Select the Overwrite existing agents check box.
This option controls whether the Agent Management Job skips targets that already have agents installed.Attention: Selecting this option will cause data loss when an endpoint's Ivanti Endpoint Security Agent is overwritten.
- Click Next.
The Credentials page opens.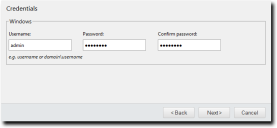
If a dialog opens that notifies you that an endpoint reboot is required following agent installation, click Continue to dismiss the dialog.
- Define Windows credentials for the target.
Type the applicable information in the following fields.When configuring an Agent Management Job, you must define valid Windows credentials.
- Click Next.
The Agent Settings page opens.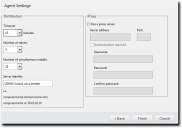
- Define the Distribution options.
The following table describes each list their available values.List
Description
Timeout (list)
Defines the number of minutes before the Agent Management Job terminates an install attempt due to a non-responsive agent installation or removal (0-30).
Number of retries (list)
Defines the number of attempts an agent installation or removal will retry if the initial attempt fails (1-10).
Number of simultaneous installs
(list)
Defines the maximum number of agents that can installed or removed simultaneously during the job (1-25). A value of 1 indicates that serial installs or removals should occur.
- Define the Ivanti Endpoint Security server that the agent will report to using the Server Identity field.
Define the Server identity using one of the following formats.- DNS name (computername.domainname.com)
- Computer name (computername)
- IP address (10.10.10.10)
Tip: The wizard fills this field with the server computername by default.
- If the target endpoints will communicate with the Ivanti Endpoint Security server through a proxy server following initial agent installation, select the Use a proxy server check box and define the following fields:
Server address: The applicable proxy IP address
Port: The applicable proxy port number used to communicateIn many network environments, although a proxy is used for Internet access, a proxy bypass is used for all access within the corporate network. Therefore, only enter proxy information if your agents will be required to use a proxy to access your Ivanti Endpoint Security server.
- If the target endpoints will use a proxy for agent to server communication, and that proxy requires authentication, select the Authentication required check box and define the following fields:
Username: A user name that authenticates with the proxy.
Password: The password associated with the Username.
Confirm password: The Password retyped. - Click Finish.
The Install Agents Wizard closes. Depending on how you configured the job, it moves to either the Scheduled tab or Active tab on the Job Results page. The job will run at the applicable time, installing agents on the defined targets, and move to Completed tab when finished.
|
Method |
Steps |
|---|---|
|
To schedule an immediate job: |
Select the Immediate option. |
|
To schedule a one-time job: |
|
|
To schedule a recurring weekly job: |
|
|
To schedule a recurring monthly job: |
|
Tip: One-time and recurring jobs scheduled for the last day of a 31-day month are automatically rescheduled for the last day of shorter months.
|
Method |
Steps |
|
|---|---|---|
|
To define targets using a single IP address: |
|
|
|
To define targets using an IP range: |
|
|
|
To define targets using a computer name: |
|
|
|
To define targets using network neighborhood: |
|
|
|
To define targets using active directory: |
|
|
|
To define targets using an imported file: |
|
|
Active Directory Input Example: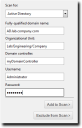
|
Option |
Description |
|---|---|
|
Verify With Ping |
Jobs using this option send ping requests to all network endpoints targeted for discovery. Endpoints that respond to the request are flagged for scanning; unresponsive endpoints are skipped. Endpoints unresponsive to Verify With Ping are not scanned by other selected discovery options. Anti-virus software and host firewalls may block Verify With Ping. If necessary, adjust any antivirus and firewall configurations to permit ping requests. |
|
ICMP Discovery |
Jobs using this option request a series of echoes, information, and address masks from endpoints. Endpoint responses are then compared to a list of known ICMP fingerprints to identify endpoint operating systems. ICMP Discovery is ineffective on endpoints configured to ignore ICMP requests. For best results identifying Windows operating systems, use this option in conjunction with Windows Version Discovery. |
|
Port Scan Discovery |
Jobs using this option perform a limited scan on endpoint FTP, Telnet, SSH, SMTP, and HTTP ports. Based on the application banners found in these ports, endpoint operating systems are generically identified. For best results in identifying Windows operating systems, use this option in conjunction with Windows Version Discovery. |
|
SNMP Discovery |
Jobs using this option request system properties for SNMP devices (routers, printers, and so on) from the management information base. Following credential authentication, SNMP devices are identified. Without authenticated credentials, SNMP devices ignore SNMP Discovery requests. In this event, one of two outcomes occur: the SNMP device is misidentified as a UNIX endpoint or the SNMP device is not detected. Jobs with no SNMP credentials use the public credential by default. |
|
Windows Version Discovery |
Jobs using this option identify an endpoint's specific version of Windows following generic operating system identification during ICMP or Port Scan Discovery. Correct operating system identification is contingent upon authenticated credentials. This option must be used in conjunction with either ICMP or Port Scan Discovery. |
|
Resolve DNS Names |
Jobs using this option acquire the endpoint DNS name through a local DNS server query. These names are displayed in job results for easy endpoint identification. |
|
Resolve MAC Addresses |
Jobs using this option acquire endpoint MAC addresses through endpoint queries. These addresses are displayed in job results for easy endpoint identification. Monitor network inventory reports to prevent MAC address spoofing that may alter the Resolve MAC Addresses results. |
|
Resolve NetBIOS Names |
Jobs using this option acquire endpoint NetBIOS names through WINS NetBIOS mapping. These names are displayed in job results for easy endpoint identification. |
|
Field |
Description |
|---|---|
|
Username |
A user name that authenticates with Windows-based endpoints. Type the user name in a local format (UserName) or a domain format (DOMAIN\UserName). When configuring Agent Management Jobs, Ivanti recommends using the built-in Administrator account. |
|
Password |
The password associated with the Username. |
|
Confirm password |
The Password retyped. |
After Completing This Task:
- If you installed an endpoint module that requires a reboot, reboot the endpoint(s) when the Agent Management Job completes.
- After the Agent Management Job completes, install agent modules if necessary. For additional information, refer to Installing Endpoint Modules.
Uninstalling Agents by Agent Management Job
You can remotely uninstall agents from endpoints in your network using an Agent Management Job. These jobs prevent administrators from having to uninstall agents locally.
Prerequisites:
- Verify that your target endpoints are Windows endpoints.
Refer to the Ivanti Endpoint Security: System Requirements Guide for a complete list of supported Windows platforms for endpoints.Important: Linux, UNIX, and Mac endpoints cannot have agents installed using an Agent Management Job.
- Ensure any anti-virus software installed on your target endpoints is disabled.
- Gather the built-in Administrator credentials for endpoints you are installing agents on. Successful job outcome is contingent upon authenticated credentials for this account.
- Configure your server to allow an Agent Management Job. For additional information, refer to Configuring the Ivanti Endpoint Security Server for Discovery Scanning.
- Configure your targets to allow an Agent Management Job. For additional information, refer to Configuring Endpoints for Agent Management Jobs
You complete the Agent Management Job within the Ivanti Endpoint Security Web console using an easy-to-use wizard. Configuration of the Agent Management Job is similar to configuration of a Discovery Scan Job. Configuration occurs in the Uninstall Agents Wizard.
- Begin configuration of the Uninstall Agent Wizard.
Complete one of the following steps sets to begin configuration.Context
Steps
To open the Wizard without targets predefined
Select Discover > Assets and Uninstall Agents
To open the Wizard with target predefined:
- Select Manage > Endpoints.
- Select the endpoints you want to uninstall agents from.
- From the toolbar, select Manage Agents > Uninstall Agents.
- [Optional] Type a new name in the Scan job name field.
By default, a new Agent Management Job for uninstallation is named New Agent Uninstall Management Job , followed by the server's date and time, which is formatted according to your browser's locale setting.
- Schedule the job using one of the following methods.
Tip: During job scheduling, you can use the following shortcuts:- Click the Calendar icon to select a Start date. Selecting a date automatically fills the Start date field.
- Click the Clock icon to select a Start time. Selecting a time automatically fills the Start time field.
Method
Steps
To schedule an immediate job:
Select the Immediate option.
To schedule a one-time job:
- Ensure the Once option is selected.
- Define a start date by typing a date in the Start date field.
The format must be mm/dd/yyyy. - Define a start time by typing a time in the Start time field.
- The format must be hh:mm followed by AM or PM (if necessary).
- This field supports both 12- and 24-hour time.
Tip: Scheduling a one-time job for a past date and time will launch the job immediately.
To schedule a recurring weekly job:
- Select the Weekly option.
- Define a start date by typing a date in the Start date field.
The format must be mm/dd/yyyy. - Define a start time by typing a time in the Start time field.
- The format must be hh:mm followed by AM or PM (if necessary).
- This field supports both 12- and 24-hour time.
- Define the day of the week the job runs by selecting a day from the Run every week on the following day list.
To schedule a recurring monthly job:
- Select the Monthly option.
- Define a start date by typing a date in the Start date field.
The format must be mm/dd/yyyy. - Define a start time by typing a time in the Start time field.
- The format must be hh:mm followed by AM or PM (if necessary).
- This field supports both 12- and 24-hour time.
- Define the day of the month the job runs by typing a day in the Run every month on the following day field.
- Click Next.
The Targets page opens.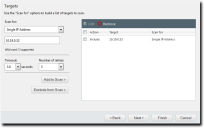
- Define targets (endpoints) for the job to locate.
Use one or more of the following discovery methods.Method
Steps
To define targets using a single IP address:
- From the Scan for list, select Single IP Address.
- Type an IP address in the empty field. Wildcards are supported.
For additional information, refer to Defining Targets Using Wildcards - Select an item in the Timeout list
The Timeout list defines the number of seconds before a scan fails per attempt due to inactivity for a particular target. Under most network conditions, the Timeout field does not require editing.
- Edit the Number of retries list. The Number of retries list defines the number of times a scan retries on that target if the scan times out.
To define targets using an IP range:
- From the Scan for list, select IP Range.
- In the first empty field, type the beginning of IP range.
Wildcards are supported. For additional information, refer to Defining Targets Using Wildcards. - In the second empty field, type the ending of the IP range.
- Select an item in the Timeout list.
The Timeout list defines the number of seconds per attempt before a scan fails due to inactivity for that particular target. Under most network conditions, the Timeout field does not require editing.
- If necessary, edit the Number of retries list. The Number of retries list defines the number of times a scan retries on that target if the scan times out.
To define targets using a computer name:
- From the Scan for list, select Computer name.
- In the empty field, type an endpoint name in one of the following formats: computername or domain\computername.
To define targets using network neighborhood:
- From the Scan for list, select Network Neighborhood.
- From the second list, select the desired network neighborhood.
To define targets using active directory:
- From the Scan for list, select Active Directory.
- In the Fully-qualified domain name field, type the DNS domain name of the domain controller you want to scan.
Tip: For example, if your domain controller DNS name is box.domain.company.local, you would type domain.company.local in this field.
- Optionally, in the Organizational Unit field, type the active directory organizational unit string from specific to broad, separating each string with front slashes (such as Techpubs/Engineering/Corporate ).
Tip: The omission of this field returns job results containing the full contents of all the active directory organizational units.
- In the Domain controller field, type the domain controller IP address.
- In the Username field, type a user name that authenticates with the domain controller.
Type the user name in one of the following format: domainname\username or username.
- In the Password field, type the password associated with the user name.
To define targets using an imported file:
- From the Scan for list, select Import file.
- Click Browse.
- Browse to the file you want to use for target discovery.
The following file types are supported: .txt and .csv. - Click Open.
For additional information about how to define targets within an imported file, refer to Defining Targets Within an Imported File.
- Add targets to the wizard list. This list indicates whether defined targets are included in or excluded from the job.
Use one of the following methods.You must include at least one target for Next to become available. You can also delete targets from the list by selecting the applicable check boxes and clicking Remove.
- To include defined targets in the job, click Add to Scan.
- To exclude defined targets from the job, click Exclude from Scan.
Tip: Repeat this step to add additional targets to the list.
- [Optional] Edit the Targets list.
- To remove targets from the list, select the list item(s) and click Remove.
- To edit targets on the list, select the list item(s) and click Edit.
For additional information, refer to Editing Targets.
- Click Next.
The Options page opens. - Select or clear the desired Scan Options.
The following table defines each Scan Option. - Click Next.
The Credentials page opens.
- Define Windows credentials for the target.
Type the applicable information in the following fields.When configuring an Agent Management Job, you must define valid Windows credentials.
- Click Next.
The Agent Settings page opens.
- Define the Distribution options.
The following table describes each list their available values.List
Description
Timeout (list)
Defines the number of minutes before the Agent Management Job terminates an install attempt due to a non-responsive agent installation or removal (0-30).
Number of retries (list)
Defines the number of attempts an agent installation or removal will retry if the initial attempt fails (1-10).
Number of simultaneous installs
(list)
Defines the maximum number of agents that can installed or removed simultaneously during the job (1-25). A value of 1 indicates that serial installs or removals should occur.
- Click Finish.
The Uninstall Agents Wizard closes. Depending on how you configured the job, it moves to either the Scheduled tab or Active tab on the Job Results page. The job will run at the applicable time, uninstalling agents on the defined targets, and move to the Completed tab when finished.
Tip: One-time and recurring jobs scheduled for the last day of a 31-day month are automatically rescheduled for the last day of shorter months.
|
Option |
Description |
|---|---|
|
Verify With Ping |
Jobs using this option send ping requests to all network endpoints targeted for discovery. Endpoints that respond to the request are flagged for scanning; unresponsive endpoints are skipped. Endpoints unresponsive to Verify With Ping are not scanned by other selected discovery options. Anti-virus software and host firewalls may block Verify With Ping. If necessary, adjust any antivirus and firewall configurations to permit ping requests. |
|
ICMP Discovery |
Jobs using this option request a series of echoes, information, and address masks from endpoints. Endpoint responses are then compared to a list of known ICMP fingerprints to identify endpoint operating systems. ICMP Discovery is ineffective on endpoints configured to ignore ICMP requests. For best results identifying Windows operating systems, use this option in conjunction with Windows Version Discovery. |
|
Port Scan Discovery |
Jobs using this option perform a limited scan on endpoint FTP, Telnet, SSH, SMTP, and HTTP ports. Based on the application banners found in these ports, endpoint operating systems are generically identified. For best results in identifying Windows operating systems, use this option in conjunction with Windows Version Discovery. |
|
SNMP Discovery |
Jobs using this option request system properties for SNMP devices (routers, printers, and so on) from the management information base. Following credential authentication, SNMP devices are identified. Without authenticated credentials, SNMP devices ignore SNMP Discovery requests. In this event, one of two outcomes occur: the SNMP device is misidentified as a UNIX endpoint or the SNMP device is not detected. Jobs with no SNMP credentials use the public credential by default. |
|
Windows Version Discovery |
Jobs using this option identify an endpoint's specific version of Windows following generic operating system identification during ICMP or Port Scan Discovery. Correct operating system identification is contingent upon authenticated credentials. This option must be used in conjunction with either ICMP or Port Scan Discovery. |
|
Resolve DNS Names |
Jobs using this option acquire the endpoint DNS name through a local DNS server query. These names are displayed in job results for easy endpoint identification. |
|
Resolve MAC Addresses |
Jobs using this option acquire endpoint MAC addresses through endpoint queries. These addresses are displayed in job results for easy endpoint identification. Monitor network inventory reports to prevent MAC address spoofing that may alter the Resolve MAC Addresses results. |
|
Resolve NetBIOS Names |
Jobs using this option acquire endpoint NetBIOS names through WINS NetBIOS mapping. These names are displayed in job results for easy endpoint identification. |
|
Field |
Description |
|---|---|
|
Username |
A user name that authenticates with Windows-based endpoints. Type the user name in a local format (UserName) or a domain format (DOMAIN\UserName). When configuring Agent Management Jobs, Ivanti recommends using the built-in Administrator account. |
|
Password |
The password associated with the Username. |
|
Confirm password |
The Password retyped. |