Supplying Scan Credentials for Target Machines
Browse credentials are slightly different from the scan credentials described in this section. Browse credentials are used by servers, domains, and organizational units to enumerate machines but do not actually authenticate to the individual machines. See Adding Virtual Machines Hosted by a Server and Machine Group Dialog: Bottom Section for information on specifying browse credentials.
In addition, Security Controls also uses a scheduler credential for all tasks scheduled to be run on the console. You set this credential from the Scheduled Console Tasks dialog.
This section provides information on how to define new scan credentials and how to assign the credentials to target machines. Credentials consist of a user name and password pair used to authenticate the program to specified target machines. One credential can be associated with any number of operations or entities. The credentials are stored with strong encryption techniques and are not available to anyone except the user who provided them.
The scan credentials you supply will be used to access remote machines, perform any scans, and push any necessary files. The supplied credentials will NOT be used to:
- Authenticate to the local (console) machine
- Perform a patch deployment
Rather, the program uses the credentials of the currently logged on user to authenticate to resources on the local machine. Therefore, in order to perform tasks on the local machine, make sure you log on using an account that has administrator and local machine access rights.
The machine credentials that you supply are used to provide access to the remote machine and to push the necessary patch deployment files. The actual deployment, however, will be run under the remote machine's Local System account.
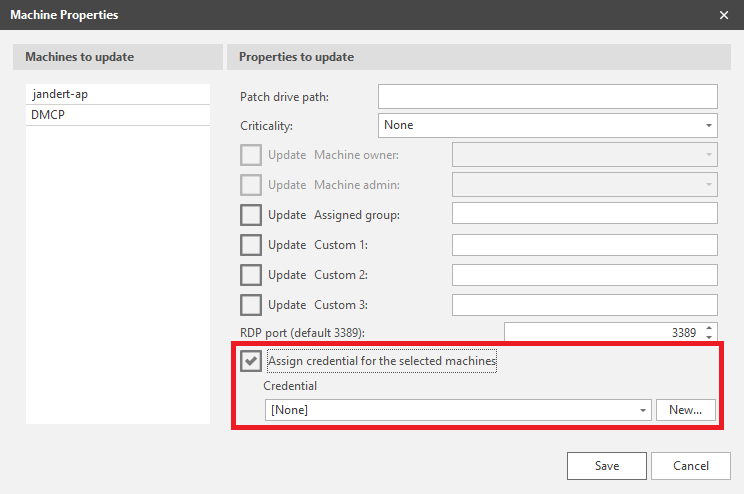
You use a machine group to initially assign scan credentials to target machines. You can assign credentials to individual machines, to all machines in a machine group, or both. After a machine has been scanned and is contained in Security Controls's database of managed machines, you can use the Machine Properties dialog to assign different credentials if desired.
IMPORTANT! If there are two or more administrators using Security Controls, each administrator should provide their own machine credentials. For details see Potential Issues When Using Multiple Admins.
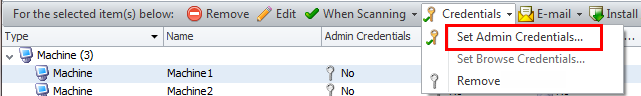
To assign credentials to one or more machines in a machine group, in the bottom pane select the machines and then select Credentials > Set Admin Credentials.
On the Assign Credentials dialog, select from the list of available credentials or click New to define new credentials.
When credentials are applied to the selected machines, the name of the assigned credential is displayed next to the icon.
To assign credentials to all machines in a machine group, in the top pane select Credentials > Set Credentials.
On the Assign Credentials dialog, select from the list of available credentials or click New to define new credentials.
When credentials are assigned, the button name will change to the name of the assigned credential.
There are several different tabs that can be used to add virtual machines to a machine group. The credentials that will be used to scan and/or deploy patches to these machines depends on how the machines are defined to the group and on the current power state of each machine.
- Hosted Virtual Machines tab: Used to add virtual machines that are hosted by a server. The credentials used to scan each machine depends on the current power state of the machine.
- A hosted virtual machine that is offline at the time of a scan will be accessed using the server's browse credentials. Any individual credentials supplied for the machine are ignored.
- A hosted virtual machine that is online at the time of a scan will be accessed using scan credentials for that machine. See Assigning Credentials to Individual Machines in a Machine Group, above.
- Workstation Virtual Machines tab: Used to add offline virtual machines that reside on individual workstations. You should assign individual machine credentials for each virtual machine defined using this tab. If appropriate, credentials can also be assigned at the machine group level. The credentials are used during the mounting process and provide permission for Security Controls to access the virtual machine files on the workstation. See Assigning Credentials to Individual Machines in a Machine Group, above.
- Machine Name tab, Domain Name tab, or IP Address/Range tab: Used to add virtual machines that reside on individual workstations and that are online at the time of a scan. See Assigning Credentials to Individual Machines in a Machine Group, above.
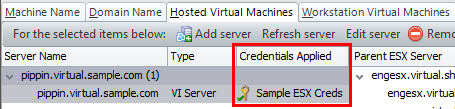
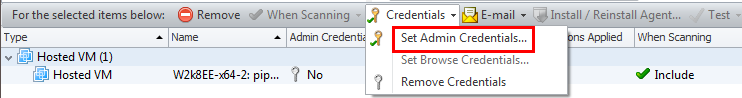
After one or more machines have been scanned and are contained in Security Controls's database of managed machines, you can use the Machine Properties dialog to assign different credentials or to remove credentials.
There may be several reasons for providing different credentials to machines after a scan has been performed. If you have multiple administrators in your organization and each is responsible for a different domain, they will need to set their own credentials before performing an action. Or, your organization's policy may be to separate scan (assessment) duties from deployment duties, in which case different credentials are probably required.
See also:
Credential Precedence for Physical Machines and Online VMs