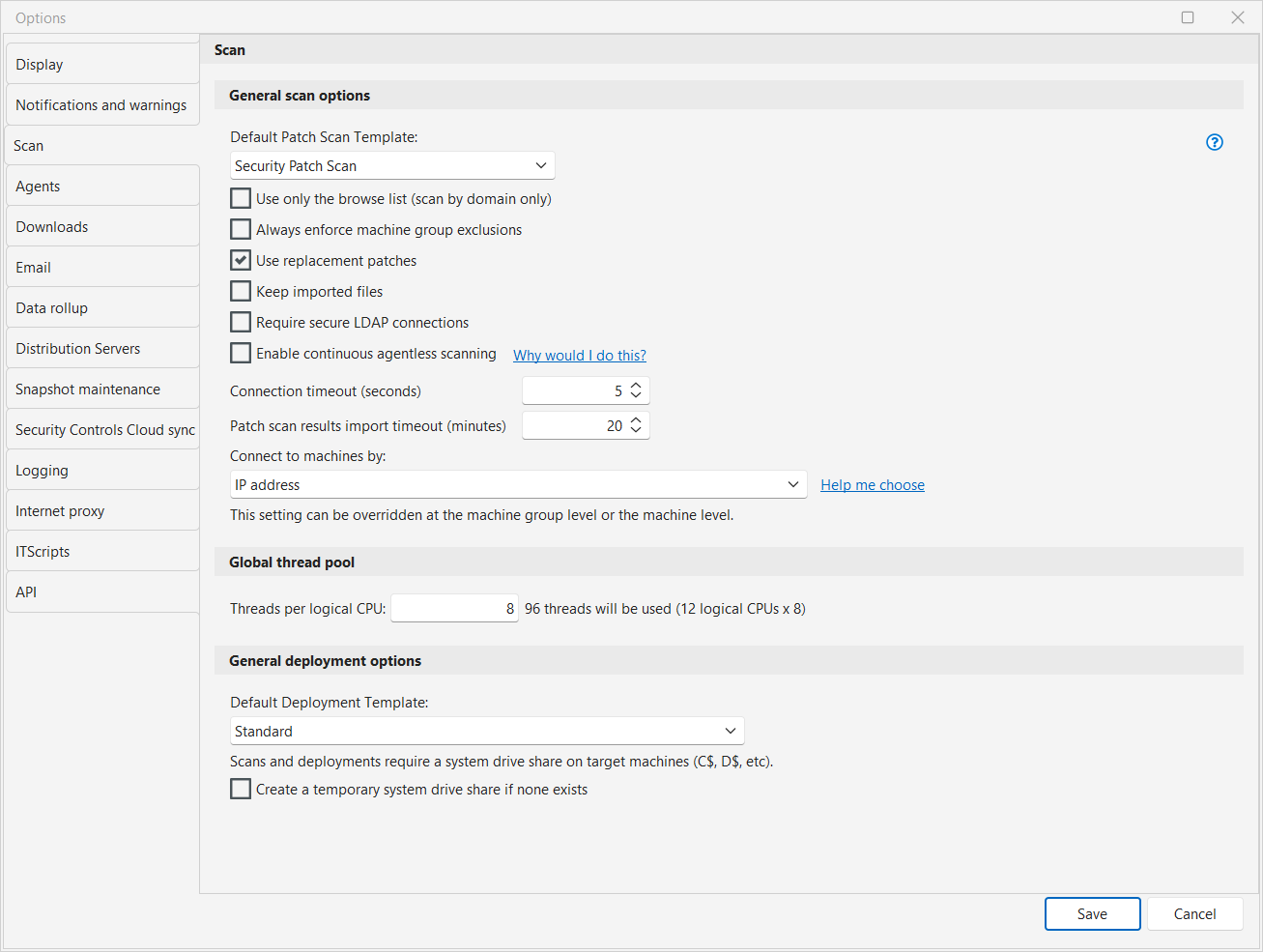
Scan Options
The Scan Options dialog allows you to specify patch scanning and deployment options.
|
Field |
Description |
|---|---|
|
Default Patch Scan Template |
The scan template you wish to set as the default when performing patch scans. |
|
Use only the browse list (scan by domain only) |
When scanning domains, the machines scanned are those contained in the "browse list" of machines in your Microsoft network rather than all the machines in the domain as specified by the domain controller. Using this option will typically reduce the number of machines that the program will attempt to connect to when performing the scan. For more information, see Discovering Machines. |
|
Always enforce machine group exclusions |
When using multiple machine groups in a scan operation, if a machine is excluded from one machine group but is included in another, the machine will be excluded from the operation. If the Always enforce machine group exclusions check box is not enabled, for this same situation the machine will be included in the operation. Examples:
|
|
Use replacement patches |
Instructs Security Controls to only scan for patches that are not replaced, ignoring patches that have been replaced by other patches. For example, instead of reporting on all missing Internet Explorer patches, only the latest and most current IE patches will be reported. |
|
Keep imported files |
The results files used by a scan operation are stored on disk indefinitely rather than being deleted after the results are imported into the program. |
|
Require secure LDAP connections |
Prevents the insecure port 389 from being used if the secure port 636 fails when querying for OUs or machines in LDAP both in the machine group editor and during a scan. By default, this is disabled. Port 389 is always used when browsing domains after clicking Browse Active Directory on the Machine Group editor. However, the data sent to it is encrypted using Kerberos, so there is no security risk. |
|
Enable continuous agentless scanning |
Adds an option to schedule recurring agentless patch scans at minute-based intervals. This is only recommended for use under certain circumstances within Network Access Control (NAC) environments. For more detailed information, see Continuous Agentless Scanning. If this option is enabled and there are scheduled scans that are using minute-based intervals, you will not be able to disable this option until you delete those scheduled scans using the Scheduled Console Tasks Manager. |
|
Connection timeout (seconds) |
The maximum amount of time to wait for a target machine to respond to the console during a scan. If the console cannot make a connection to the target machine in the specified number of seconds the machine is skipped. A connection attempt may timeout earlier than the specified value, this simply puts a maximum value on the wait time. |
|
Patch scan results import timeout (minutes) |
The maximum amount of time to wait for the console to import scan results from all target machines. If all machines have not reported results within the specified number of minutes, the console will stop waiting and will proceed with any post-scan activities such as generating reports and sending email. |
|
Connect to machines by |
Specifies the method to use when connecting to your client machines. There are two options:
For more detailed information, see IP Address vs FQDN. This setting can be overridden at the machine group level. It can also be overridden at the machine level for scans that are initiated from Machine View or Scan View. |
|
Global thread pool |
Specifies the total number of threads that can be used during a patch scan or deployment, an asset scan, or a power status scan. The value you specify will be multiplied by the number of logical CPUs on the console machine to determine the maximum number of threads that may be used during a scan instance. One thread will be used to scan one machine, so if you specify a maximum of 64 threads it means that 64 machines can be simultaneously scanned during one scan. Allowing many machines to be scanned at the same time requires more network resources. Reduce this number if you are scanning over a slow link. If you are scanning machine groups that contain machines defined by an IP range, a domain or an organizational unit, this option will also be used prior to the scan. It will limit the number of threads that are used to determine which machines should be scanned. |
|
Default Deployment Template |
Specifies the deployment template to use as the default. Any new deployment templates you previously defined will be included in the drop-down list. For more information see About Deployment Templates. |
|
Create a temporary system drive share if none exists |
Enables Security Controls to create and use a temporary administrator share name on a target machine during the authentication process. The share name will be removed from the target machine when the scan or deployment is complete. While this option does not apply to most organizations, if you are an organization that for whatever reason has disabled or renamed the administrator share names (C$, D$, etc.) on your target machines, then you must enable this check box in order for Security Controls to access those machines. |