New Features V5.3 and 5.3 U1
New Features added in V5.3 U1
You can now delete existing scan templates that you no longer need directly from the Scan Explorer.
To delete unwanted scan templates:
- On the Perform New Scan dialog, click Manage Templates.
The Manage Templates dialog appears, listing the existing templates and the number of scans related to them. - Select the template you want to delete, then click Delete Template.
You are asked to confirm the deletion. When you have deleted a template, you can no longer access any existing scans that were associated with it.
For more information about the Scan Explorer, see Working with Scan Explorer.
You can add a new column, called Managed Instance Name, in the Log Explorer to see the specific device instances and so improve the visibility and simplify the log review process. For more information about defining the settings used in the Log Explorer, see Template Settings Dialog.
You can now shadow the file name and file size on macOS devices. You configure the macOS shadowing in the same way as Windows devices directly within the Scan Explorer. For information about adding shadowing, see Add Shadowing.
Event-based notifications are now available for macOS users. You can select a specific trigger and disable the irrelevant notifications, and also configure this for specific devices or for all (general) devices connected to the computer. For information about adding event notifications, see Add Event Notification.
The Status info tab has been improved on the macOS client to increase visibility and provide more detailed information.
Whitelist (allow) and blacklist (deny) functionality for specific certificates in the trusted store is now available. This enables you to increase granularity while avoiding micro-management.
You configure this using the System Trust Subjects option on the Computer tab in the Default Options. For more information, see Computer tab.
A new Splunk Connector for IDAC provides increased visibility and predefined dashboards. You can connect directly to the IDAC database and see events when they occur.
Read a blog about the Splunk connector
The connector is available in the Splunk base.
The following customer issues have been resolved in this release:
|
Problem ID |
Title |
|---|---|
|
810657 |
OU unit groups removed in AD not removed in IDAC |
|
818561 |
Re-install not working on x64 platform |
|
824837 |
Unable to unlock medium after install, 2nd reboot of client |
New Features added in V5.3
Responding to the multiple requests submitted through our customer calls, user voice ideas, and support calls, we are supporting for the first time another operating system. 5.3 update brings to the IDAC family the new macOS agent with a modern UI that focuses on attached devices rather then device classes.
This first version enables permission assignment on Removable storage devices from the management console. The supported macOS versions are 10.15 (Catalina) and 11.2 (Big Sur).
While developing the mac agent, we have taken the opportunity to introduce an MQTT component to facilitate the communication between the server and the mac agents. This new component enables increased scalability, more efficient information distribution, reduced update rates, extremely lightweight overhead, and a more secure communication. To take full advantage of the new mac agent, you need to install an MQTT broker at your choosing or use an existing component.
No additional license is required. You can use the free seats from your current license.
Support for M1/ARM64 is currently still in Beta. To use removable encryption provided through the kernel extension you need to boot the device into recovery mode. Access Security Policy and select Reduced Security. Selecting the tick boxes underneath enables the management of kernel extensions.
For information about installing Device Control for macOS, see macOS Setup.
Using shadowing on large environments can lead to great storage requirements. To better handle this need, with IDAC 5.3 you can change the default path where shadow files are stored. In this case you can use your storage servers or even better, using third party applications that mount cloud storage drives, you can store your shadow files in the cloud.
You do this using two values of type REG_SZ in the registry key Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\sxs\parameters:
DataFileDirectory - the location used to store shadow files and scan files, and also used for temporary purposes when agents upload logs, shadow files, and scan files.
TempFileDirectory - optionally, if the server specified in DataFileDirectory is remote, the location specified here is used to offload the intensive usage of the temporary accesses to a local folder or a close share with low latency.
For more information, see Add Shadowing.
Over the years, application control was recognized as a great instrument for achieving a bullet proof environment. This is mainly because of its efficiency and robustness. But sometimes the rigidity of the product can add additional complexity to the process. We have listened your feedback and with 5.3 we are bringing new tools to make your life easier when managing application control rules.
With IDAC 5.3, when defining path rules for application control you can now use the following additional system variables: “%ProgramFiles(x86)%”, %ProgramData%, %HomePath%, %AppData%, %LocalAppData%.
For more information, see Managing Path Rules.
Trusted certificate helps administrators to manage application control. Enable the System Trust AC option in Default Options to execute on the endpoints any application or library that is digitally signed either with embedded digital signature or through a catalog file (trusted by the operating system).
For more information, see Computer tab.
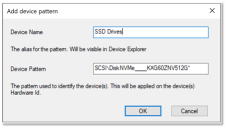
Micromanaging of devices got better with this release. We have added an option to manage device permissions using wildcards on device hardware id. If your devices match a specific pattern you can add a single entry into Device Explorer and assign your policy on this entity. All devices that are matching the hardware id rule will have this policy applied.
For more information, see Create Device Patterns.
In some situations, the notifications generated by the attachment/detachment of the devices can be alarming for the end-user. To avoid this, mainly when connecting to a docking station, you can now manage the visibility for these notifications from the Default Options panel.
For more information, see Computer tab.
To better manage the license seats, with 5.3, the administrator is notified in the console if the license limit has been reached. This is very useful in identifying when the endpoints have been disabled but are still consuming license slots. There is no enforcement linked to this feature so there is no need to worry about limited security.
A new sxopt option has been added to help with printing issues after an update occurred. In some cases, the end-user can encounter difficulties in using the printers unless they reboot after the update. Having this option enabled will disable printing shadowing until the next successful reboot but will allow printing normally. By default, the option is disabled. For more information, contact Ivanti support.
With the 5.3 update, a minimal set of anonymized data usage will be captured on a weekly basis. This data will be used to help us target common functionality areas to address in future releases as well as enabling us to gain better insight to help troubleshoot issues. We believe that capturing anonymized data will help us to give you the greatest return of value going forward with IDAC, helping us to focus in the right areas of the product that matter the most to you.
The amount of data sent through the telemetry feature can be controlled through the Management Console Default Options> Telemetry. The new telemetry options are Minimum and Full. Note that the Disable option has been changed to Minimum. For further information, please see the following KB article on the Ivanti Community.
For more information, see Computer tab.
The following customer issues have been resolved in this release:
|
Problem ID |
Title |
|---|---|
|
75016 |
IDAC 5.2 | SXS | Server.exe errors out when downloading Microsoft OLE DB Driver for SQL Server even with internet access |
|
75157 |
Warning events in Event Viewer when IDAC service account does not have sysadmin rights in SQL, and Telemetry is enabled |
|
75430 |
Server processes the logs too slowly |
|
75772 |
Exclusive Mode causes authorization loop with some devices connected |
|
75812 |
Issues with syncing domain information to the console |
|
76116 |
IDAC 5.2 | fimpex.exe not working with -u option |
|
76288 |
Enhanced hdd detection not working as expected |
|
717853 |
User who cleared database log is not captured in audit logs |
|
694210 |
Stack overflow when IDAC is used alongside with ATC module from Bitdefender |