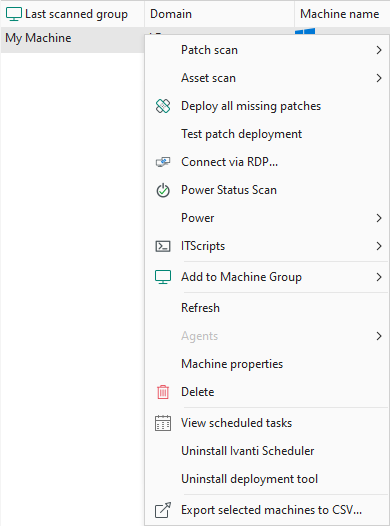
Performing Actions on Machines
You can right-click on any Windows machine in the top pane and perform a number of different actions.
|
Field |
Description |
|---|---|
|
Patch Scan |
Enables you to initiate a patch scan of the selected machines using any of the available patch scan templates. |
|
Asset Scan |
Enables you to initiate an asset scan of the selected machines using any of the available asset scan templates. |
|
Deploy all missing patches |
Enables you to deploy (install) all patches currently missing on the selected machine. See Deploy to All Scanned Machines for more information. If you deploy a patch to a specific SQL Server instance, the patch is applied to all instances on that machine. |
|
Test patch deployment |
Enables you to perform a test deployment to the selected machines. This is especially useful for patch deployments you want to schedule for a later time. Testing the deployment allows you to correct any potential problems in a deployment and make it less likely that a deployment will fail. See the Operations Monitor for more information. Test deployments will not work on offline virtual machines. |
|
Connect via RDP |
Enables you to make a Remote Desktop connection to the selected machine. See How to Initiate a Remote Desktop Connection for more details. |
|
Power Status Scan |
Enables you to perform a power status scan on the selected machines. |
|
Power |
Enables you to modify the power state of the selected machines. |
|
ITScripts |
Enables you to either open a Windows PowerShell™ prompt or select and execute an approved script. See How to Execute a Script for details. |
|
Application Control |
Enables you to retrieve Application Control events that have been uploaded from the selected machine to the database. See the Event Viewer for details of events. |
|
Add to Machine Group |
Enables you to add the selected machines to a new machine group or to an existing machine group. See Creating A New Machine Group for more information. IMPORTANT! Machines you add to the machine group are automatically assigned the associated machine credentials. (Hosted virtual machines are the exception, they are assigned the last known machine group credentials.) If no machine credentials are available, no credentials will be assigned and the default credentials will be used in any subsequent scans. If the default credentials are not valid for the machines, and if the account credentials of the person currently logged on to the program are also not valid for the machines, scans of the machines you just added to the group will fail. To prevent scanning errors, always supply credentials for machines you add to a machine group. See Supplying Credentials for more information. |
|
Refresh |
Refreshes the information displayed in the top pane. |
|
Agents |
Enables you to:
|
|
Machine Properties |
Enables you to view and edit machine properties. See Managing Individual Machine Properties for more information. |
|
Delete |
Deletes the selected machine from Machine View. If the machine is rescanned it will be re-added to Machine View. Deleting a machine from Machine View also affects the information displayed for that machine within Scan View (see Accessing Patch Scan Results). The machine will be moved to the Machines Not Scanned tab and all previous scan information for that machine will be lost. |
|
View scheduled tasks |
Enables you to view the Scheduled Remote Tasks Manager, which gives you a single location from which to monitor the |
|
Uninstall Ivanti Scheduler |
Removes the Ivanti Scheduler from the machine. Use of the Ivanti Scheduler was discontinued in v2023.2 and it should be removed from all target machines. Be careful not to remove the Ivanti Scheduler until you are certain that all scheduled tasks still using this scheduler have been run. |
|
Uninstall deployment tool |
Removes the tool used by Security Controls to execute a deployment package on the machine. This tool gets pushed to the target machine when a patch deployment is initiated from the console. You can remove this tool if you want to eliminate any temporary files on the machine. |
|
Export selected machines to CSV |
Export information about the selected machines to a Comma Separated Values (CSV) file. The CSV file can then be used within a spreadsheet program. |
You can right-click on any Linux machine in the top pane and perform a number of different actions.
|
Field |
Description |
|---|---|
|
Power Status Scan |
Enables you to initiate a power status scan of the selected machines. |
|
Add to Machine Group |
Enables you to add the selected machines to a new machine group or to an existing machine group. See Creating A New Machine Group for more information. IMPORTANT! Machines you add to the machine group are automatically assigned the associated machine credentials. If no machine credentials are available, no credentials will be assigned and the default credentials will be used in any subsequent scans. If the default credentials are not valid for the machines, and if the account credentials of the person currently logged on to the program are also not valid for the machines, scans of the machines you just added to the group will fail. To prevent scanning errors, always supply credentials for machines you add to a machine group. See Supplying Credentials for more information. |
|
Refresh |
Refreshes the information displayed in the top pane. |
|
Agents |
Enables you to install an agent, assign a different policy to the agent or uninstall an agent. Enables you to:
|
|
Machine Properties |
Enables you to view and edit machine properties. See Managing Individual Machine Properties for more information. |
|
Delete |
Deletes the selected machine from Machine View. If the machine is rescanned it will be re-added to Machine View. |
|
Export selected machines to CSV |
Export information about the selected machines to a Comma Separated Values (CSV) file. The CSV file can then be used within a spreadsheet program. |
The following keyboard shortcuts are available:
- Ctrl+A: Selects all machines.
- CTRL+click: Multiple machines can be selected by holding down the CTRL key while selecting machines.
- SHIFT+click: A contiguous group of machines can be selected by holding down the SHIFT key while selecting the starting and ending machines in the list.
- SHIFT+PAGE UP: Selects a range of machines from the one currently selected to the top of the table.
- SHIFT+PAGE DOWN: Selects a range of machines from the one currently selected to the bottom of the table.
- HOME: Moves the focus to the first cell in the table.
- END: Moves the focus to the last cell in the table.