Access Cookbook Overview
In a cloud services environment, there are service providers (SP) such as Office 365, Salesforce, Workday and there is are identity providers (IDP) such as Box, Okta, Ping to name a few in each category. Generally, a service provider is federated with an identity provider for authentication. The user gets authenticated by the identity provider and obtains a SAML token for accessing applications in a cloud environment.
There is a trust establishment between SP and IDP via SAML2 Federation. The trust is formed after exchanging the SAML2 metadata between both providers. Once the trust is formed, the IDP issues digitally-signed assertions which the SP can then verify and allow the user to access the services. SAML provides single sign-on service for users accessing their services hosted in a cloud environment.
The cookbooks serve as a step-by-step configuration manual for users working with service providers and identity providers in a cloud environment.
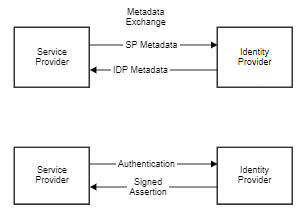
Configuring a federated pair
Configuring a federated pair in MobileIron Access requires 5 steps:
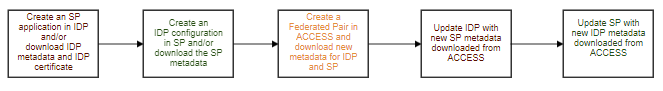
Step 1: On the IDP Portal, create an application in the IDP and download the metadata and certificate. If the application already exists, download the metadata and certificate directly. For more information on individual cookbooks, see Cookbooks for Federated Pairs table below.
Step 2: On the SP Portal, create an IDP configuration in the SP and download the metadata. If the IDP configuration already exists, download the metadata directly. For more information on individual cookbooks, see Cookbooks for Federated Pairs table below.
Step 3: On the MobileIron Access portal, create a Federated Pair in Access and download the new proxy metadata generated in Access for SP and IdP. You must configure Access to select your service provider and the identity provider. You can apply the configuration settings for the service provider and the identity provider to create a federated pair.
-
Log in to Access.
-
Click Profiles > Get Started.
-
Enter the Access host information and upload the ACCESS SSL certificate. The other fields retain the default values. Click Save.
-
Click Profiles > Federated Pairs > Add.
-
Select the appropriate service provider and complete the configuration.
-
Click Next > select the appropriate identity provider and complete the configuration.
-
Click Done. The new federated pair is created.
-
On the Federation page, download the proxy metadata for SP and IDP.
Step 4: On the IDP portal, update the IdP with the new SP proxy metadata downloaded from Access.
Step 5: On the SP Portal, update the SP with the new IdP proxy metadata downloaded from Access.
Cookbooks
|
Cookbooks for Federated Pairs |
Cookbooks for Service or Identity Providers |
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|