Configuring Workspace Properties
To configure Workspace properties:
1.Click the Settings icon on top-right-corner of the page and select Workspace Properties.
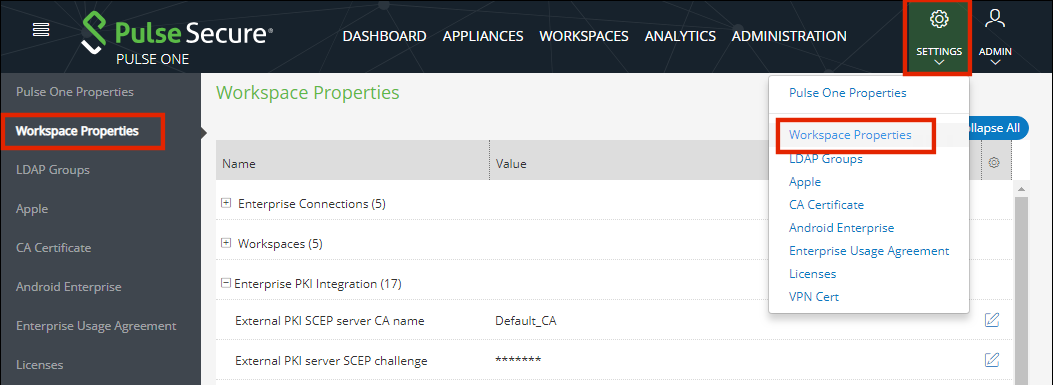
2.Click the Edit button corresponding to the field you want to edit.
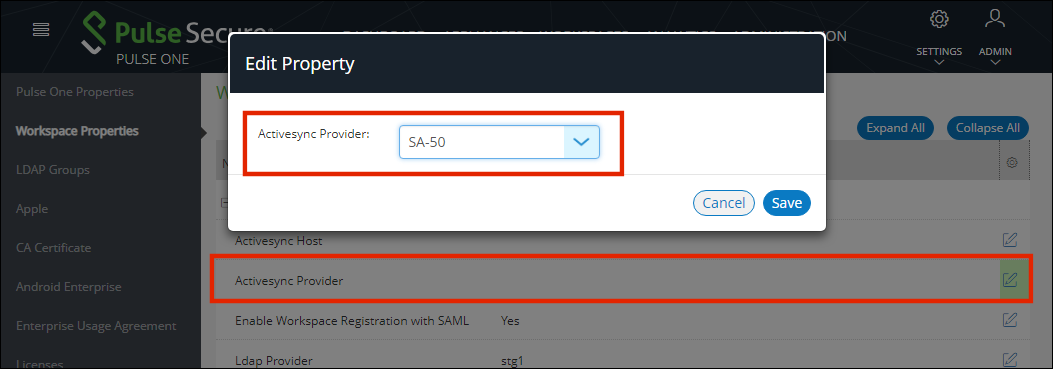
3.Change the value and then click Save. For example:
Enterprise Connections
The Enterprise Connections settings are described below:
•Activesync Host – Address of the Pulse Workspace that ActiveSync Proxy will forward ActiveSync connections to. This address must be accessible to the Pulse Workspace ActiveSync Proxy.
•Activesync Provider – Pulse Connect Secure appliance to which Pulse One / Pulse Workspace will forward the ActiveSync notifications.
•Enable Workspace Registration with SAML – Boolean. If True, enables single sign-on.
•Ldap Provider – The Pulse Connect Secure appliance that is configured for the User's group membership, based auto-provisioning.
•SDP Provision Certificate – This property is required for SDP operation. See the Pulse Secure Software Defined Perimeter documentation for full details of its use.
•VPN provider – The Pulse Connect Secure appliance that is configured to provide VPN access, see Configuring Auto-Config of a VPN Provider on Mobile Devices.
Workspaces
The Workspaces settings are described below:
•Allow the ability to perform full device wipes? – Boolean. If True, a full device wipe can be performed on a target device. See Performing Workspace Actions.
•Desired accuracy for workspace location in meters – The requested accuracy for the use of device location on iOS. The default is 100 meters for iOS devices. See Configuring Device Location.
This property is not used by Android devices. The location of Android devices is always the best approximation using available network information.
•Display Advanced AFW Properties – Boolean. If True, shows advanced AFW properties (App Permissions).
•Enable enrollment of managed iOS clients – Boolean. This controls how iOS mobile devices are enrolled by Pulse Workspace:
•If True, mobile devices will be enrolled as managed clients.
•If False (default), mobile devices will be enrolled as managed workspaces.
For full details, see Understanding Managed Devices and Managed Clients.
•Enable International App Stores – Boolean. If True, you can choose apps from international app stores.
•Enable Location Service – Boolean. If True, the device location feature is supported on all compatible devices. See Working with Device Location.
•Enable Background Location Service – Boolean. If True, the background device location feature is supported on all compatible devices. See Working with Device Location.
This property will be supported on mobile devices running Pulse Client v9.8.x or later, which is scheduled for release in July 2021.
This property is ignored if the Enable Location Service property is disabled.
•Location Maps Service API Key – Optional API Key. Where supplied, Google Maps is used to display device location. See Working with Device Location.
Enterprise PKI Integration
iOS Operating system has built-in MDM client, which handles the profile management and it has support for Simple Certificate Enrollment Protocol (SCEP). The Android Operating System does not come with the SCEP support, so SCEP functionalities are built into the Pulse Secure Android Client app.
To use SCEP with Windows server, the user needs to enable NDES service on the Windows server, and ensure it is reachable by both Workspace server and client devices. For more details, see TechNet: Active Directory Certificate Services (AD CS): Network Device Enrollment Service (NDES).
The Enterprise PKI Integration settings are described below:
•External PKI SCEP server CA name – (Optional) Windows NDES server typically accepts any value. If the user has already set up the NDES server to only accept a specific value, they can specify it here.
•External PKI server SCEP challenge – If Use static SCEP challenge for external PKI server is True, specify the challenge password required by the client to enroll the certificate.
•External PKI server SCEP URL – This is the NDES service address the client will send requests to. In general, the default location is https://FQDN-CertSrv/mscep.dll.
•Use external PKI server – This is the master switch of the external PKI feature. Boolean. If False, the system uses built-in CA no matter how other configurations were set.
•Use SCEP to request certificate for Android ActiveSync from external PKI server – Boolean. If True, a SCEP payload is delivered to all onboarded Android devices that use a policy with the Activesync Allow Authentication via Certificate property enabled. See ActiveSync. The device then automatically retrieves an ActiveSync certificate from the SCEP server.
If the Use Windows CA server CAWE to request ActiveSync certificates for both Android and iOS devices property is also True, the Use SCEP to request certificate for Android ActiveSync from external PKI server property overrides it, and SCEP is used for Android devices.
•Use SCEP to request certificate for Android VPN from external PKI server – Boolean. If True, the VPN certificate is requested from SCEP for onboarded Android devices.
•Use SCEP to request certificate for Android Wifi from external PKI server – Boolean. If True, the WiFi certificate is requested from SCEP for onboarded Android devices.
•Use SCEP to request certificate for iOS ActiveSync from external PKI server – Boolean. If True, a SCEP payload is delivered to all onboarded iOS devices that use a policy with the Activesync Allow Authentication via Certificate property enabled. See ActiveSync. The device then automatically retrieves an ActiveSync certificate from the SCEP server.
If the Use Windows CA server CAWE to request ActiveSync certificates for both Android and iOS devices property is also True, the Use SCEP to request certificate for iOS ActiveSync from external PKI server property overrides it, and SCEP is used for iOS devices.
•Use SCEP to request certificate for iOS MDM from external PKI server – Boolean. If True, the iOS MDM certificate is requested from SCEP for onboarded iOS devices. Also, the CA certificate needs to be uploaded from the CA certificate settings page.
If this value is changed, it will change how the Workspace server validates the MDM command signatures sent by iOS devices. As a result, any enrolled devices will need to be re-enrolled to get a new MDM certificate so that it can work again.
•Use SCEP to request certificate for iOS VPN from external PKI server – Boolean. If True, the VPN certificate is requested from SCEP for onboarded iOS devices.
•Use SCEP to request certificate for iOS Wifi from external PKI server – Boolean. If True, the WiFi certificate is requested from SCEP for onboarded iOS devices.
•Use static SCEP challenge for external PKI server – Boolean. Set to True if the SCEP server is set up to accept a static challenge, or any challenge (password disabled). If True, you must set External PKI server SCEP challenge.
•Use Windows CA server CAWE to request ActiveSync certificates for both Android and iOS devices – Boolean. If True, the ActiveSync certificate is requested from Windows CA server CAWE for all onboarded devices that meet the following criteria:
•This workspace property is only used on devices whose policy includes an enabled Activesync Allow Authentication via Certificate property, see ActiveSync.
•This workspace property is not used for Android devices when the Use SCEP to request certificate for Android ActiveSync from external PKI server workspace property is set to True. That is, the SCEP property is used instead.
•This workspace property is not used for iOS devices when the Use SCEP to request certificate for iOS ActiveSync from external PKI server workspace property is set to True. That is, the SCEP property is used instead.
•Use Windows CA server CAWE to request iOS MDM certificates – Boolean. If True, the iOS MDM certificate is requested from Windows CA server CAWE for onboarded iOS devices. Also, the CA certificate needs to be uploaded from the CA certificate settings page.
If this value is changed, it will change how the Workspace server validates the MDM command signatures sent by iOS devices. As a result, any enrolled iOS devices will need to be re-enrolled to get a new MDM certificate so that it can work again.
•Use Windows CA server CAWE to request SDP device certificates – Boolean. If True, the SDP device certificate is requested from Windows CA server CAWE for all onboarded devices. See the Pulse Secure Software Defined Perimeter documentation for full details of its use.
•Use Windows CA server CAWE to request VPN certificates for both Android and iOS devices – Boolean. If True, the VPN certificate is requested from Windows CA server CAWE for all onboarded devices.
•Use Windows CA server CAWE to request WIFI certificates for both Android and iOS devices – Boolean. If True, the WiFi certificate is requested from SCEP for all onboarded devices.
•Windows CA Server certsrv URL – This is the URL of the Windows certsrv web page. The mscep_admin page under this URL is used to fetch a new SCEP challenge. If the system uses static SCEP challenge, this configuration is not required.
•Windows CA Server certificate template name – (Optional) The Windows CA server template name.
•Windows CA Server certsrv page user name – Set with a username that has access to the mscep_admin page under the certsrv URL. If the system uses static SCEP challenge, this configuration is not required.
•Windows CA Server certsrv page user password – Set with a password that has access to the mscep_admin page under the certsrv URL. If the system uses static SCEP challenge, this configuration is not required.
Misc
The miscellaneous (Misc) settings are described below:
•Support Email – Pulse Workspace support center’s email address. This email address will be shown in the Support information displayed on the device.
•Support Phone – Pulse Workspace support center’s phone number. This phone number will be shown in the Support information displayed on the device.