The Endpoint Details Page
The Endpoint Details page lists general endpoint information, agent information, the modules installed on the endpoints, the groups the endpoint is included in, and the group policies applied to it. This page also includes a tab for each module installed.
This page features the following tabs:
- The Information Tab
- The Vulnerabilities/Patch Content Tab
- The Security Configuration Tab List
- The Inventory Tab
- The Deployments and Tasks Tab
- The Virus and Malware Tab
- The Antivirus Policies Tab
- The Easy Lockdown/Auditor Files Tab (Application Control only)
- The Application Control Policies Tab (Application Control only)
- The Device Control Policies Tab (Device Control only)
Viewing the Endpoint Details Page
The Endpoint Details page contains comprehensive details for an endpoint and its activity within the Ivanti Endpoint Security system.
View the Endpoint Details page for an endpoint by clicking an endpoint name link from the Endpoints page.
- From the Navigation Menu, select Manage > Endpoints.
- Click the Name link associated with the endpoint details you want to review.
The Endpoint Details page opens to the Information tab. - [Optional] Complete a task listed in Working with the Endpoint Details Page.
The Information Tab
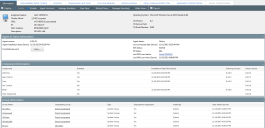
The Information tab displays information about a selected endpoint. The page displays general information organized into endpoint, agent, status, component, group, and policy sections.
Tip:
- Each Information tab section can be collapsed and expanded.
- Each section can also be dragged higher or lower on the page. Place more frequently used information high on the page.
The Information Tab Toolbar
The Information tab toolbar contains the endpoint assessment tasks and functions that are available for you to perform on managed endpoints.
The following table describes the buttons available in the Information tab toolbar.
|
Toolbar Button |
Description |
|---|---|
|
Deploy... |
Opens with Deployment Wizard , which lets you deploy content to the applicable endpoint. For additional information, refer to Deploying Content (Endpoint Details Page). |
|
Enable |
Enables the endpoint (if it is disabled). For additional information, refer to Enabling an Endpoint. |
|
Disable |
Disables the endpoint (if it is enabled). For additional information, refer to Disabling an Endpoint. |
|
Agent Versions... |
Defines the agent version(s) that can be installed on an endpoint. For additional information, refer to Upgrading the Agent on a Single Endpoint. |
|
Manage Modules... |
Opens the Add/Remove Modules dialog, which lets you manage agent features for modules install on Ivanti Endpoint Security. For additional information, refer to Managing Endpoint Modules. |
|
Scan Now (Menu) |
Opens the Scan Now menu. |
|
Discover Applicable Updates... (Scan Now Menu Item) |
Prompts the Discover Applicable Updates task to immediately check the endpoint. For additional information, refer to Using Scan Now (Endpoint Details Page). |
|
Reboot Now... (Patch and Remediation only) |
Prompts the selected endpoint to reboot. For additional information, refer to Rebooting Endpoints. |
|
Update AV Definitions |
Updates AntiVirus definitions. For additional information refer to Updating AntiVirus Definitions. |
|
Manage Remotely (menu) |
Opens the Manage Remotely menu. For additional information, refer to Management Options. |
|
Launch Remote Desktop... (Manage Remotely menu item) |
Launches the log in page for the Windows Remote Desktop Connection (RDC), which allows you to connect to a computer in another location. For additional information, refer to Starting the Remote Desktop Connection. |
|
Launch MMC: Computer Management... (Manage Remotely menu item) |
Launches the Microsoft Management Console (MMC), which allows you to manage and monitor Windows systems. For additional information, refer to Starting the Microsoft Management Console. |
|
Launch NSLookup... (Manage Remotely menu item) |
Launches the NSLookup MS-DOS command to the endpoint. For additional information, refer to Accessing the NSLookup MS-DOS Command. |
|
Launch Ping... (Manage Remotely menu item) |
Launches the Ping MS-DOS command to the endpoint. For additional information, refer to Accessing the PING MS-DOS Command. |
|
Launch Putty... (Manage Remotely menu item) |
Launches PuTTY, a remote management tool that allows you to remotely control target computers over the Internet. For additional information, refer to Starting the PuTTY Communication Tool. |
|
Launch VNC... (Manage Remotely menu item) |
Launches the log in page for the Virtual Network Connection (VNC), which allows you to remotely access another computer. For additional information, refer to Starting the Virtual Network Connection Tool. |
|
Wake Now... |
Wakes the endpoint. For additional information, refer to Waking Endpoints from the Information Tab. |
|
Export |
Exports the page data to a comma-separated value (.csv) file. For additional information, refer to Exporting Data. Important: The Enhanced Security Configuration feature for Internet Explorer suppresses export functionality and must be disabled to export data successfully. Pop-up blockers in Internet Explorer or other supported browsers may also suppress export functionality and should be disabled. |
For additional information about using core features, refer to The Information Tab Toolbar in the Ivanti Endpoint Security Help.
Endpoint Information
The fields that appear in this section of the Information tab contain identifier and operating system details, such as the IP address and the operating system.
The Endpoint Information section displays the following endpoint data:
|
Field |
Description |
|---|---|
|
Endpoint Name |
The name of the endpoint. |
|
DNS |
The DNS name of the endpoint. |
|
Display Name |
Alternate name or phrase (up to 50 characters) for the endpoint to help you identify and distinguish it. Endpoint decision-making information you can provide here includes what system it belongs to, where it is located, and what it is used for. The Display Name will appear as a tool-tip when you hover over the Endpoint Name in the on the Manage > Endpoints page and Manage > Groups page (Endpoint Membership view). |
|
IP |
The IP Address of the endpoint. |
|
MAC Address |
The MAC address of the endpoints. |
|
Description |
The description of the endpoint, if available. |
|
Operating System |
The abbreviated name of the operating system detected on the endpoint. |
|
OS Version |
The version number of the operating system running on the endpoint. |
|
OS Service Pack |
The service pack level of the endpoint. |
|
OS Build Number |
The build number of the operating system running on the endpoint. |
Agent Information
The fields that appear in the Agent Information section of the Information tab contain agent status, version, and connectivity details for the agent installed on the endpoint.
The Agent Information section displays the following agent data.
|
Field |
Description |
|---|---|
|
Agent version |
The version of the agent that the endpoint is currently running. A |
|
Agent installation date (Server) |
The date and time on the server when the agent registered with Ivanti Endpoint Security. This is typically the date the agent was installed on the endpoint. |
|
Uninstall password (button) |
Click View to view the uninstall password assigned to the endpoint. See Viewing the Agent Uninstall Password for more information. |
Status Information
The fields that appear in the Status Information section of the Information tab contain status and connectivity details for the agent installed on the endpoint.
The following fields are added to Status Information after Patch and Remediation is installed.
|
Field |
Description |
|---|---|
|
Agent status |
Indicates the status of the endpoint. The following list defines column values: Online: The agent is able to communicate with the Ivanti Endpoint Security server in the predefined time period. Refer to Configuring the Agents Tab for additional information on configuring agent default behavior. Offline: The agent is unable to communicate with the Ivanti Endpoint Security server in the predefined time period. In an Offline status, the agent still enforces all policies. A Warning ( Disabled: The agent will no longer enforce any module policies or complete tasks. All endpoints must show a Disabled status in order to delete the endpoint. Refer to Disabling the Ivanti Endpoint Security Agent. |
|
Last connected date (Server) |
The date and time on the server that the agent last communicated with Ivanti Endpoint Security. |
|
EDS Status |
The status of the Endpoint Distribution Service on the server. Service statuses include Started and Stopped. |
|
PR status |
The Patch and Remediation status for the endpoint. |
|
Last DAU scan status |
The status of the Discover Applicable Updates (DAU) scan when last run. The status also serves as a link to the Deployment Results page. Status values include: Success, Failure followed by the failure code, and Not Available, which indicates that the endpoint has not checked in. The Not Available Last DAU Status does not serve as a hyperlink. |
|
Last DAU scan time (server) |
The time of the last successful DAU scan. A value of Not Available indicates the endpoint has not completed a DAU scan. |
|
Last PM reporting time (Server) |
The date and time that endpoint last uploaded power management information to the server. |
Component Information
This table lists which module components are installed on the endpoint. It also lists additional information about each module.
Information for the Patch and Remediation endpoint module is displayed after its installation. The following table describes each Component Information table column.
|
Column |
Description |
|---|---|
|
Component |
Indicates the name of the applicable module. |
|
Installed |
Indicates whether the module is installed on the endpoint. Values include: Yes: The module is installed. No: The module is not installed. Pending Install: The module is in the process of installing. Pending Uninstall: The module is in the process of uninstalling. Pending Reboot: The module has been installed, but the endpoint needs to reboot to complete installation. Error: There was an error while installing or uninstalling the module. Click the for additional information about the error. Expired: The module license has expired. |
|
Installation Date/Time (Server) |
Indicates the date and time on the server that the user initiated a module install. |
|
Running Version |
Indicates the version of the module installed on the agent. |
|
Policy Version |
Indicates the version of the module that is should be installed based on the agent version defined in the applicable agent policy set. |
Group Information
The columns that appear in the Group Information section of the Information tab contain group membership details for the endpoint.
The Group Information section displays the following group data for an endpoints.
|
Column |
Description |
|---|---|
|
Group Name |
The group that the endpoint holds membership in, either through direct assignment or inheritance. Click the group name to open Group Information page. |
|
Originating Group |
The name of the group in the parent hierarchy from which the endpoint inherits membership. If the endpoint is directly assigned to a group, the value displayed is Direct Assignment. Click the value to go to the Group Information page. |
|
Type |
The group type, which can include:
|
|
Deployments Applicable |
Indicates that there are applicable deployments available for this endpoint. |
|
Added By |
The Ivanti Endpoint Security user who added the endpoint to the group. If the endpoint was added Ivanti Endpoint Security, the column contains a value of System. |
|
Date Added (Server) |
The date and time that the endpoint was added to the group. |
Note:
- If the values in the Group Name and the Originating Group columns are identical, then the endpoint is directly assigned to that group and is not inherited.
- Groups listed in gray indicate that the endpoint holds group membership through inheritance.
Policy Information
The fields that appear in the Policy Information section of the Information tab contain details about the policies used by the endpoint during a deployment.
New Ivanti Patch and Remediation policies are listed if they have been applied to the endpoint.
These policies are the results of applying each of the policies defined by the endpoint’s group membership and filling in any undefined policies from the Global Policy. Conflict resolution rules are applied when applicable.
|
Column |
Description |
|---|---|
|
Name |
The name of the policy applied to the endpoint. |
|
Value |
The value of the policy applied to the endpoint. |
|
Description |
The description of the policy. |
For a description of all agent policies, including agent policies not applied to the endpoint, refer to The Agent Policy Sets Page List.
Antivirus Policies
This section lists the antivirus policies assigned, and whether or not that policy set is directly assigned or inherited from a parent. This section only shows the antivirus policies assigned; you cannot use it to assign one. Assign an antivirus policy to the selected group via the Antivirus Policies view.
The following reference describes the Antivirus Policies table.
|
Field |
Description |
|---|---|
|
Policy Name |
Indicates the name of the antivirus policy. |
|
Policy Type |
Indicates if the antivirus policy type is a Recurring Virus and Malware Scan or a Real-time Monitoring Policy. |
|
Source |
Indicates if the antivirus policy is directly assigned or inherited from a parent. |
Antivirus Real-time Monitoring Resultant Policy
If two or more real-time monitoring policies are assigned, their combined resultant effect is displayed in this section. The policy details can only be viewed here; you cannot change or edit them.
The following reference describes the Antivirus Real-time Monitoring Resultant Policy table.
|
Field |
Description |
|---|---|
|
Virus Detection Action |
Indicates actions to take upon virus/malware detection. |
|
Local users |
Indicates real-time scan options for local users. |
|
Services and remote users |
Indicates real-time scan options for services and remote users. |
|
Exclude Path/ Filename |
Indicates if path(s)/filename(s) will be excluded from the scan |
|
Optional drives |
Indicates if optional drives will be included in the scan. |
The Vulnerabilities/Patch Content Tab
The Vulnerabilities/Patch Content tab displays vulnerability information associated with the selected endpoint. The tab displays the same information shown on each Patch Content page (My Default Patch View, Vulnerabilities, Software, and so on). However, this tab is filtered for the endpoint.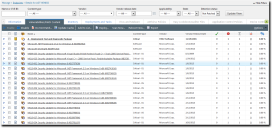
The Vulnerabilities/Patch Content Tab Toolbar
The Vulnerabilities/Patch Content tab toolbar contains the tasks and functions that are available for you to perform on managed endpoints.
|
Button |
Function |
|---|---|
|
Enable |
Enables a selected disabled vulnerability. For additional information, refer to Enabling Content. |
|
Disable |
Disables a selected enabled vulnerability. For additional information, refer to Disabling Content. |
|
Do Not Patch... |
Disables the selected patch for specific groups and endpoint that you select. For more information, see Disabling Content for Groups/Endpoints. |
|
Update Cache |
Updates the package cache for selected packages. For additional information refer, to Updating the Cache. |
|
Deploy... |
Opens the Deployment Wizard . For additional information, refer to Deploying Content (Endpoint Details Page). |
|
Scan Now... |
Prompts the Discover Applicable Updates task to launch immediately and scan all agent-managed endpoints within your network for vulnerabilities. For additional information, refer to Using Scan Now (Endpoint Details Page). |
|
Reboot Now... |
Prompts the selected endpoint to reboot. For additional information, refer to Rebooting the Endpoint. |
|
Export |
Exports the page data to a comma-separated value (.csv) file. For additional information, refer to Exporting Data. Important: The Enhanced Security Configuration feature for Internet Explorer suppresses export functionality and must be disabled to export data successfully. Pop-up blockers in Internet Explorer or other supported browsers may also suppress export functionality and should be disabled. |
|
Options (menu) |
Opens the Options menu. For additional information, refer to The Options Menu. |
The Vulnerabilities/Patch Content Tab List
The Vulnerabilities/Patch Content tab list tracks package name, cache status, content type, and deployment data.
The following table describes each list column.
|
Column |
Icon |
Definition |
|---|---|---|
|
Status |
|
The content item status, which indicates when the server downloaded the content item metadata. For additional information, refer to Content Status and Type. |
|
Package Status |
|
The cache status for the content item, which indicates if the server downloaded the content item packages. For additional information, refer to Content Icons and Descriptions. |
|
Name |
N/A |
The content item name, which links to the Patch Status of the item. For additional information, refer to The Patch Status Page. |
|
Content Type |
N/A |
Indicates the content item type. For more information, see one of the following topics: |
|
Vendor |
N/A |
The name of the vendor that created the software in the content item. |
|
Vendor Release Date |
N/A |
The date and time that the vendor released the software in the content item. |
|
Number of endpoints which came up Patched |
|
The number of endpoints patched with the content item. |
|
Number of endpoints which came up Not Patched |
|
The number of endpoints not patched with the content item. |
|
Total Applicable |
|
The number of endpoints that the content item applies to. |
|
Number of endpoints which came up Do Not Patch |
|
The number of endpoints that administrators have created a patch exception for. |
|
Percent Patched |
|
The percentage of applicable endpoints patched with the content item. |
Additionally, you can expand each content item by clicking its arrow (>). The following table describes each field that displays when you expand a content item.
The following detail information appears on this page.
|
Name |
Description |
|---|---|
|
Beta |
Indicates if the content item is in beta. |
|
Downloaded on (UTC) |
The date and time on which the content was downloaded. |
|
Associated packages |
The number of packages associated with the content item. |
|
Packages status |
The cache status for the content item packages. |
|
Ivanti Endpoint Security ID |
The Ivanti Endpoint Security identifier for the content item. |
|
Custom Patch Lists |
A listing of all Custom Patch Lists that the content item is included in. |
|
State |
The enabled/disabled/completed status of the content item. |
|
Enabled/Disabled by |
The Ivanti Endpoint Security user who last disabled or enabled the content. |
|
Enabled/Disabled date (Server) |
The date and time the content was disabled or enabled. |
|
Enable/Disable reason |
The reason the user provided for disabling or enabling the content. You can click the Edit link to change the reason. |
|
Vendor product ID |
The identifier given to the security content item by the vendor. |
|
Vendor release date/time (UTC) |
The date and time the vendor released the software in the content item. |
|
Common Vulnerability Exploit (CVE)1 |
The CVE number for the content. |
|
Vulnerability Code Description1 |
A description of the vulnerability associated with the content item. |
|
Reference Text1 |
The reference text(s) associated with the content item vulnerability. |
|
Description1 |
The narrative description of the distribution package. This section may include important notes about the content item and a link to more information. |
|
1This meta data appears conditionally based on whether it was added for the content item. Additionally, there may be multiple instances of each meta data section. |
|
The Security Configuration Tab
The Security Configuration tab contains security configuration assessment data for endpoints that have agent policy sets that include security configuration benchmarks received during Security Configuration Assessment package deployment.
You can expand the assessment sets to view the individual assessments performed on the endpoint. Icons next to the individual assessments indicate if the endpoint passed or failed the assessment.
This tab is only available when you are licensed for the Ivanti Security Configuration Management module, and the module is installed.
The Security Configuration tab has functionality that allows you export assessment results. The following table describes this functionality.
|
Button |
Definition |
|---|---|
|
Export |
Exports the security configuration assessment results in .csv file format. For additional information, refer to Exporting SCM Data to CSV. |
|
Export XCCDF |
Exports the security configuration assessment results in XML eXtensible Checklist Configuration Description Format (XCCDF). For additional information, refer to Creating the XCCDF Export Job. |
The Security Configuration Tab List
The Security Configuration tab list tracks security configuration benchmark identification information, assessment parameters, and assessment status data.
The following table describes the column headers found on the Security Configuration tab.
|
Column |
Icon |
Definition |
|---|---|---|
|
Benchmark |
N/A |
Indicates the security configuration assessment benchmark applied to the endpoint through an agent policy set. |
|
Profile |
N/A |
Indicates the benchmark profile applied to the endpoint. |
|
Assessment Engine |
N/A |
Indicates the version number of the check tool in use at the time the benchmark was uploaded. |
|
Date Assessed |
N/A |
Indicates the date on which the endpoint was assessed. |
|
Number of assessments which came up Compliant |
|
Indicates the number of assessments that the endpoint passed. |
|
Number of assessments which came up Non- Compliant |
|
Indicates the number of assessments that the endpoint failed. |
|
Number of assessments which came up Error |
|
Indicates the number of assessments that did not run. |
|
Total Percent Complete |
|
Indicates the percentage of assessments that the endpoint passed. |
Individual Assessment Results Fields
The Assessment Details window contains fields that provide a narrative description of the assessment and the criteria applied to determine passed/failed status.
You can click the Expand button to view the registry location evaluated by the assessment.
The following table describes the columns that appear in the assessment details table. These are the values that the assessment criteria are evaluated against.|
Column |
Definition |
|---|---|
|
TestID |
A unique identifier for the assessment. |
|
Actual Value |
The value found on the endpoint by the assessment. |
|
Operation |
The mathematical operation between the actual value and the expected value that was performed during assessment. |
|
Expected Value |
The value that, if found, would result in a pass result. |
|
Result |
The end result of the criterion assessment. |
The Inventory Tab
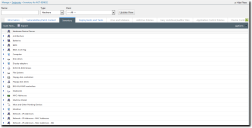
The Inventory tab displays the inventory information for the selected endpoint. Inventory is organized by hardware device class. The page displays the same information as is presented in the Inventory page.
The Inventory Tab Toolbar
The Inventory tab toolbar contains functions that allow you to detect inventory on managed endpoints.
The following table describes the toolbar functions used in the Inventory tab.
|
Toolbar Item |
Description |
|---|---|
|
Scan Now... |
Prompts the Discover Applicable Updates (DAU) task to launch on the endpoint. For additional information, refer to Using Scan Now (Endpoint Details Page). |
|
Export |
Exports the page data to a comma-separated value (.csv) file. For additional information, refer to Exporting Data. Important: The Enhanced Security Configuration feature for Internet Explorer suppresses export functionality and must be disabled to export data successfully. Pop-up blockers in Internet Explorer or other supported browsers may also suppress export functionality and should be disabled. |
|
Options (menu) |
Opens the Options menu. For additional information, refer to The Options MenuThe Options Menu. |
The Inventory Tab List
The Inventory tab lists the components found on each endpoint registered with the Ivanti Endpoint Security Server. From this tab you can view info about the operating system, software, hardware, and services found on the endpoint. You can change the inventory listed on the page by selecting a
Operating System Inventory
When the Inventory tab filter row is set to type Operating System, the page list displays the following information:
|
Column |
Description |
|---|---|
|
Operating System |
The operating system installed on the endpoint. |
|
|
The number of endpoints that the operating system is installed on. This is the total number of endpoints running this operating system, not just the endpoint you're working with. |
Software Inventory
When the Inventory tab filter row is set to type Software Programs, the page list displays the following information:
|
Column |
Description |
|---|---|
|
Software Programs |
The software programs installed on the endpoint. There's a row for each program. |
|
|
The number of endpoints that the program is installed on. This is the total number of endpoints that have this program installed, not just the endpoint you're working with. |
Hardware Inventory
When the Inventory tab filter row is set to type Hardware, the page list displays the following information:
|
Column |
Definition |
|---|---|
|
Icon |
An icon that depicts the Hardware Device Class. |
|
Hardware Device Classes |
Indicates the hardware device class. |
Each Hardware Device Class can be expanded to list class devices found on endpoints. To expand a class, click the rotating chevron (>). The following table describes the columns that display after expanding a class.
|
Column |
Definition |
|---|---|
|
Device |
Indicates the hardware devices found for the class. |
|
Icon |
Indicates the number of endpoints that host the device. |
Services Inventory
When the Inventory tab filter row is set to type Hardware, the page list displays the following information:
|
Column |
Definition |
|---|---|
|
Service Name |
The name of the service on the endpoint. |
|
System Name |
The file path that the service is running from. |
|
Current State |
The state that the service is in. |
|
Startup State |
The state the service enters upon startup. |
The Deployments and Tasks Tab
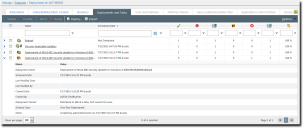
The Deployments and Tasks tab lists the deployments assigned to an endpoint and their status. Deployments remain listed until deleted.
The Deployments and Tasks Tab Toolbar
The Deployments and Tasks tab toolbar contains buttons that let you control existing deployments and export deployment data.
The following table describes each toolbar button.
|
Menu Item |
Function |
|---|---|
|
Enable |
Enables the selected disabled deployment. For additional information, refer Enabling Deployments. |
|
Disable |
Disables the selected deployment. For additional information, refer to Disabling Deployments. |
|
Abort |
Cancels the deployment or task for any endpoints which have not already received the deployment package. For additional information, refer to Aborting Deployments. |
|
Delete |
Removes the deployment from your Ivanti Endpoint Security. For additional information, refer to Deleting Deployments. |
|
Deploy... |
Opens the Deployment Wizard . For additional information, refer to Deploying Content (Endpoint Details Page). |
|
Export |
Exports the page data to a comma-separated value (.csv) file. For additional information, refer to Exporting Data. Important: The Enhanced Security Configuration feature for Internet Explorer suppresses export functionality and must be disabled to export data successfully. Pop-up blockers in Internet Explorer or other supported browsers may also suppress export functionality and should be disabled. |
|
Options (menu) |
Opens the Options menu. For additional information, refer to The Options MenuThe Options Menu. |
The Deployments and Tasks Tab List
The Deployments and Tasks tab list contains a record of each deployment for the endpoint. Each list item remains until deleted.
The following table describes each list column.
|
Column |
Icon |
Description |
|---|---|---|
|
Action |
N/A |
Contains Edit and Delete icons you can use to control packages in a deployment. For additional information see: |
|
Name |
N/A |
The name of an individual package or task included in a deployment targeted at the endpoint (not the name of the deployment itself). Click the name display Deployment Details. For more information, see The Deployment Details Page. |
|
Scheduled Date |
N/A |
The date and time a user scheduled the package or task to deploy. |
|
Status Icon |
N/A |
An icon that indicates the status of the package deployment. For information on what each icon means, see Deployment Status Icons. |
|
Number of Successful Endpoints |
|
The total number of endpoints and groups that finished the deployment successfully. |
|
Number of Failed Endpoints |
|
The total number of endpoints and groups that finished the deployment unsuccessfully. |
|
Number of Endpoints Assigned to the Deployment |
|
The total number of endpoints and groups that are assigned to the deployment. |
|
Number of In Progress Endpoints |
|
The total number of endpoints and groups that are receiving the deployment. If you deploy to a group using Agent Local Time, the deployment remains in progress until all time zones have passed. This behavior ensures any endpoints added to the group following deployment start also receive content. This behavior does not occur when using Agent UTC Time. |
|
Total Not Deployed |
|
The total number of endpoints and groups that were excluded from the deployment (because the package was already applied, not applicable, or marked Do Not Patch). |
|
Number of Endpoints That Have Completed the Deployment |
|
The total number of endpoints and groups that finished the deployment. |
|
The Percentage of Completed Endpoints |
|
The percentage of endpoints and groups that finished the deployment. Percentage = [Total Finished endpoints / Total Assigned endpoints] |
The Virus and Malware Tab
Use the Virus and Malware tab on the Endpoint Details page provides a view of all alerts generated by virus and malware scans performed by Ivanti AntiVirus on a selected endpoint.
The information and features enable you to:
Review current status: You can see the types of malware that have been detected and the endpoints that have been infected. This information will help you to determine how the infection originated and the best way to handle it.
Take remedial action: You can use Scan Now to launch the Virus and Malware Scan Wizard, configuring it to perform specific actions that will reduce the threat to the network. See Using the Virus and Malware Scan Wizard for more information.
The Virus and Malware Tab Toolbar
Enables you to perform functions on the listed event alerts, and to run an on-demand scan on a selected endpoint.
|
Button |
Function |
|---|---|
|
Scan Now |
Opens the Virus and Malware Scan Wizard. This enables an administrator to react to incoming alerts with an immediate scan on the endpoint. When configured appropriately, this scan can eliminate the problem by cleaning or deleting the infected files. For more information on running these scans, see Using the Virus and Malware Scan Wizard. |
|
Remove |
Removes the selected event alert(s) from the list. |
|
Export |
Exports the event alerts list to a comma separated value (.csv) file. |
Only event alerts from the previous 90 days are displayed. If there are a large number of event alerts and you no longer need to view all of them, you can use the Remove button to remove unwanted alerts from the list. This does not delete them from the database, however, so you can always view these removed alerts by generating an appropriate report.
The Virus and Malware Tab List
Provides a comprehensive and constantly updated list of all event alerts generated by virus and malware scans performed on the endpoint.
|
Column |
Description |
|---|---|
|
Virus/Malware Name |
The name of the virus or malware detected. If a virus or malware is detected by behavior-based techniques such as Sandbox, it will not have a unique name. Instead, the column will indicate how the malware was identified. Each example links to the relevant entry in the Virus/Malware Details page. |
|
Alert Source |
The type of scan that generated the alert:
|
|
Alert Message |
The message related to the alert status:
Both the Cleaned status and Deleted status use the same icon because in both cases the malicious code has been removed and no longer presents a danger. |
|
File Name |
The name of the file in which the malware was detected. |
|
File Path |
The file path of the file in which the malware was detected. |
|
Last Detected Date (Server) |
The date and time the alert was generated (server time). |
You can use the Group By row, available above the list, to sort list items into groups based on column headers. This feature (along with the filters above the toolbar) is useful when you need to examine a large number of event alerts.
The Antivirus Policies Tab
Use the Antivirus Policies tab on the Endpoint Details page to manage antivirus policies for a selected endpoint.
The Antivirus Policies Tab Toolbar
Contains the tasks and functions that are available for you to perform on an endpoint with AntiVirus features enabled.
|
Button |
Function |
|---|---|
|
Create |
Enables you to create a Recurring Virus and Malware Scan policy or a Real-time Monitoring Policy. |
|
Assign |
Assigns the selected policy to one or more endpoints or groups. |
|
Un-assign |
Un-assigns the selected policy from one or more endpoints or groups. |
|
Export |
Exports the selected policy to a comma separated value (.csv) file. See Exporting DataExporting Data for more information. |
|
Options |
Features options to set page views, filter data, and enable clipboard copy. See The Options Menu for more information. |
The Antivirus Policies Tab List
Provides information on existing antivirus policies assigned or inherited by a selected endpoint.
|
Column |
Description |
|---|---|
|
Select check box |
Select this check box to perform an action on the policy. |
|
Status |
An icon representing whether the policy is enabled or disabled. |
|
Policy Name |
The name given by the policy creator. |
|
Policy Type |
|
|
Source |
Defines whether the policy is assigned or inherited. |
|
Assigned Date (Server) |
The server date and time when the policy was assigned to the endpoint. |
The Easy Lockdown/Auditor Files Tab
Use the Easy Lockdown/Auditor Files tab on the Endpoint Details page to view the files that existed on a selected endpoint when an Easy Lockdown or Easy Auditor policy was assigned to it.
This content is only available when the Application Control module is installed.
The Easy Lockdown/Auditor Files Tab Toolbar
The Easy Lockdown/Auditor Files tab toolbar contains buttons that you can use to allow or deny file use for the endpoint.
The following table describes each toolbar button.
|
Button |
Description |
|---|---|
|
Authorize... |
Opens the Authorize Selected Files dialog, which you can use authorize the selected files for the applicable endpoint. For additional information, refer to Authorizing Selected Files in Application Library. |
|
Deny... |
Opens the Deny Selected Files dialog, which you can use to deny the selected files for the applicable endpoint. For additional information, refer to Denying Selected Files in Application Library. |
|
Export |
Exports the page data to a comma-separated value (.csv) file. For additional information, refer to Exporting Data. Important: The Enhanced Security Configuration feature for Internet Explorer suppresses export functionality and must be disabled to export data successfully. Pop-up blockers in Internet Explorer or other supported browsers may also suppress export functionality and should be disabled. |
|
Options (menu) |
Opens the Options menu. For additional information, refer to The Options Menu. |
The Easy LockDown/Auditor Files Tab List
The Easy LockDown/Auditor Files tab contains a list of files and file details found during audits. This list is similar to the list featured on the Application Library page.
The following table describes each column in the tab list.
|
Column |
Description |
|---|---|
|
Verification |
Indicates whether the file has been assessed by the Ivanti Endpoint Integrity Service. |
|
File Name |
The file name, including extension. |
|
File Version |
File version number. |
|
First Found Path |
The path where the file was first discovered by Application Control. |
|
Company Name |
The company that created the file. |
|
Product Name |
The product that the file is part of. |
|
Certificate |
The status of the file's certificate (if it has one):
|
|
Date Added To Library (Server) |
The date and time that the file was added to Application Library, shown as server time (UTC). |
The Application Control Policies Tab
Use the Application Control Policies tab on the Endpoint Details page to manage Application Control policies for a selected endpoint.
This content is only available when the Application Control module is installed.
The Application Control Policies Tab Toolbar
The Application Control Policies tab toolbar contains buttons you can use to create and manage Application Control policies.
The following table describes each toolbar button.
|
Button |
Description |
|---|---|
|
Create... (menu) |
Opens the Create menu. |
|
Trusted Publisher... (menu item) |
Opens the Trusted Publisher dialog, which you can use to create trusted publisher policies. |
|
Trusted Updater... (menu item) |
Opens the Trusted Updated dialog, which you can use to create trusted updater policies. |
|
Easy Auditor... (menu item) |
Opens the Easy Auditor dialog, which you can use to create easy auditor policies. |
|
Easy Lockdown... (menu item) |
Opens the Easy Lockdown dialog, which you can use to create easy lockdown policies. |
|
Assign... (menu) |
Opens the Assign menu. |
|
Trusted Publisher... (menu item) |
Opens the Assign Policy dialog, which you can use to assign a policy to groups or endpoints. |
|
Trusted Path... (menu item) |
Opens the Assign Policy dialog, which you can use to assign a policy to groups or endpoints. |
|
Trusted Updater... (menu item) |
Opens the Assign Policy dialog, which you can use to assign a policy to groups or endpoints. |
|
Local Authorization... (menu item) |
Opens the Assign Policy dialog, which you can use to assign a policy to groups or endpoints. |
|
Denied Applications Policy... (menu item) |
Opens the Assign Policy dialog, which you can use to assign a policy to groups or endpoints. |
|
Easy Auditor... (menu item) |
Opens the Assign Policy dialog, which you can use to assign a policy to groups or endpoints. |
|
Easy Lockdown... (menu item) |
Opens the Assign Policy dialog, which you can use to assign a policy to groups or endpoints. |
|
Supplemental Easy Lockdown/Auditor Policy... (menu item) |
Opens the Assign Policy dialog, which you can use to assign a policy to groups or endpoints. |
|
Unassign |
Unassigns the selected policy (or policies) from the applicable groups and endpoints. |
|
Export |
Exports the page data to a comma-separated value (.csv) file. For additional information, refer to Exporting Data. Important: The Enhanced Security Configuration feature for Internet Explorer suppresses export functionality and must be disabled to export data successfully. Pop-up blockers Internet Explorer or other supported browsers may also suppress export functionality and should be disabled. |
|
Options (menu) |
Opens the Options menu. For additional information, refer to The Options Menu. |
The Application Control Policies Tab List
The Application Control Policies tab contains a listing of Application Control policies assigned to the endpoint.
The following table describes each list column.
|
Column |
Description |
|---|---|
|
Action |
Removes the policy from the applicable groups and endpoints. |
|
Status |
Indicates the status of the policy (Enabled or Disabled). |
|
Policy Name |
Indicates the policy name. |
|
Policy Type |
Indicates the policy type (Trusted Publisher, Trusted Path, Trusted Updater, Local Authorization, Denied Applications, Easy Auditor, Easy Lockdown, or Supplemental Easy Lockdown/Auditor). |
|
Source |
Indicates the policy source. |
|
Assigned Date (Server) |
Indicates the date and time the policy was assigned to the applicable endpoints and groups. |
The Device Control Policies Tab
Use the Device Control Policies tab on the Endpoint Details page to manage Device Control policies for a selected endpoint.
This content is only available when the Device Control module is installed.
The Device Control Policies Tab Toolbar
The Device Control Policies tab toolbar contains buttons you can use to create and manage Device Control policies for the applicable endpoint.
The following table describes each toolbar button.
|
Button |
Description |
|---|---|
|
Create |
Displays a drop-down menu that allows you to select the type of policy to create. A user should have Manage Centralized DC Policies access rights to access this functionality. |
|
Assign |
Opens the Assigned Users and Endpoints dialog for the selected policy. This button is enabled only if the user has Assign Centralized DC Policies access rights and a policy is selected from the list. |
|
Unassign |
Allows you to unassign the selected policy. This button is enabled only if the user has Assign Centralized DC Policies access rights and an assigned policy is selected from the list. |
|
Delete |
Allows you delete the selected policy. This button is enabled only if the user has Manage Centralized DC Policies access rights. |
|
Edit |
Opens the respective policy wizard with the policy details. This button is enabled only if the user has Manage Centralized DC Policies access rights. |
|
Enable |
Allows you enable a policy that is currently disabled. |
|
Disable |
Allows you disable a policy that is currently enabled. |
|
Export |
Exports the page data to a comma-separated value (.csv) file. For additional information, refer to Exporting Data. Important: The Enhanced Security Configuration feature for Internet Explorer suppresses export functionality and must be disabled to export data successfully. Pop-up blockers in Internet Explorer or other supported browsers may also suppress export functionality and should be disabled. |
|
Options (menu) |
Opens the Options menu. For additional information, refer to The Options Menu. |
The Device Control Policies Tab List
The Device Control Policies tab contains a listing of Device Control policies assigned to the endpoint.
The following table describes each list column.
|
Field |
Description |
|---|---|
|
Status |
The enabled or disabled status of the policy. |
|
Policy Name |
The name of the policy. |
|
Assigned |
The assigned or unassigned status of the policy. |
|
Device Class |
The device class to which the policy applies. |
|
Device Collection |
The device collection to which the policy applies. |
|
Last Update (Server) |
The date the policy was modified last. |